
Cybersecurity researchers from WatchTowr Labs have uncovered a troubling method for exploiting abandoned domains linked to backdoors in compromised systems. By purchasing unregistered domains referenced in web shells — backdoors used by hackers — the team managed to commandeer thousands of systems worldwide with minimal effort. This follows their earlier work on vulnerabilities in the .MOBI domain system, which highlighted similar issues with expired infrastructure.
Mass-hacking-on-autopilot
WatchTowr’s latest research targeted abandoned web shell backdoors, particularly those embedded in other malicious tools. By registering expired domains once used by the web shells, the team was able to hijack traffic and potentially gain control over compromised systems.
WatchTowr
This exploit works because many web shells include callbacks to domains controlled by their creators for updates or logging. When these domains expire, attackers — or researchers — can purchase them, effectively inheriting access to the infected systems. Using this technique, WatchTowr intercepted traffic from over 4,000 unique backdoors, tracking compromised hosts as they “checked in” to the re-registered domains.
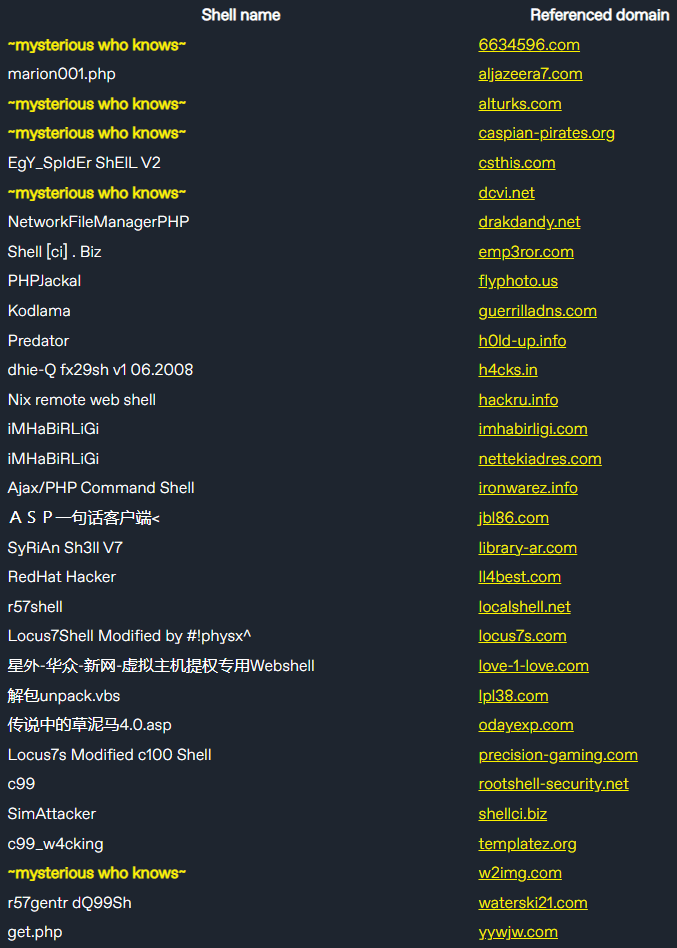
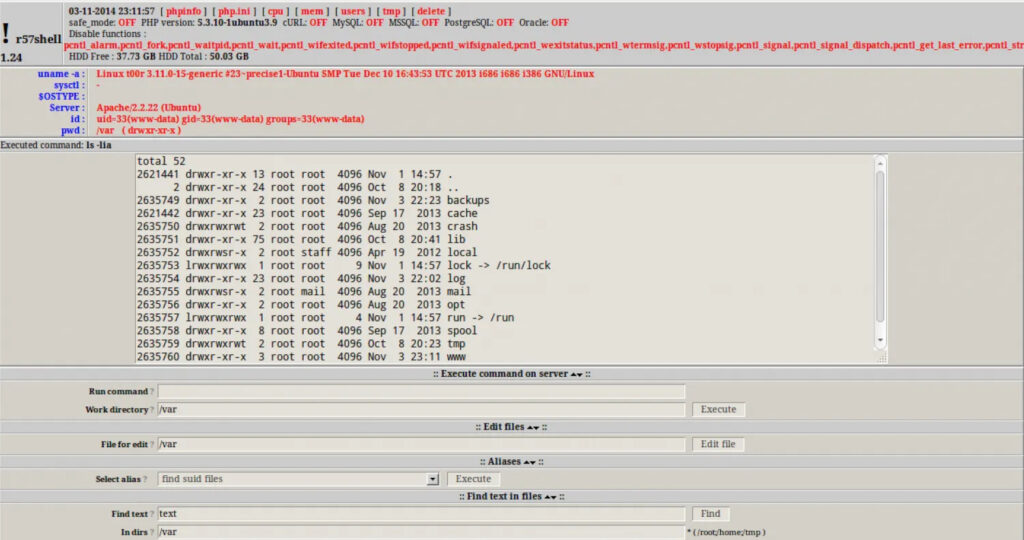
The collected data, amounting to over 300MB of logs, revealed high-profile victims like governments in Bangladesh, China, and Nigeria, as well as universities in South Korea, Thailand, and China. Many of the intercepted backdoors used older hacking tools, such as the infamous r57shell and c99shell, which have their own backdoors to allow the original authors to hijack other hackers' operations.
WatchTowr
This exploit highlights a growing problem with abandoned infrastructure. Web shells, which are malicious scripts deployed after a successful compromise, often rely on hardcoded domains or IP addresses to communicate. When attackers fail to maintain control over these domains, they leave behind a “door” for others to take over.
WatchTowr discovered this vulnerability by systematically collecting and analyzing popular web shells, identifying references to expired domains, and re-registering them. The team obtained 40+ domains for around $20 each and set up servers to monitor incoming connections.
One example involved an older Lazarus Group-associated backdoor, which included a mechanism to send URLs of compromised systems via HTTP referrer headers. By acquiring its callback domain, WatchTowr intercepted traffic from thousands of infected systems.
Risks of abandoned infrastructure
This research echoes the lessons from WatchTowr's previous findings in the .MOBI case, where an expired WHOIS domain allowed them to subvert critical internet infrastructure. The recurring theme is the security risk posed by forgotten or poorly maintained resources.
While WatchTowr has taken steps to mitigate this risk — partnering with organizations like the Shadowserver Foundation to sinkhole the newly purchased domains — the sheer scale of abandoned infrastructure underscores the ongoing challenges in securing the internet.






Leave a Reply