
The Seiko Group Corporation (Seiko) has suffered a data breach resulting from a ransomware attack that has entered today its blackmail phase.
Earlier in the month, the Japanese maker of wristwatches, clocks, semiconductors, jewelry, and optical elements, informed of a possible data breach that occurred on July 28, impacting at least one of its servers. Seiko responded to the incident by forming an investigation team that included external cybersecurity experts, who concluded that information stored in the firm’s systems had been compromised.
Although the company is still in the process of evaluating what information was accessed by the unauthorized third-party that performed the breach, the BlackCat (also known as “ALPHV”) ransomware gang posted Seiko on its extortion site today, along with very exposing data samples.
RestorePrivacy
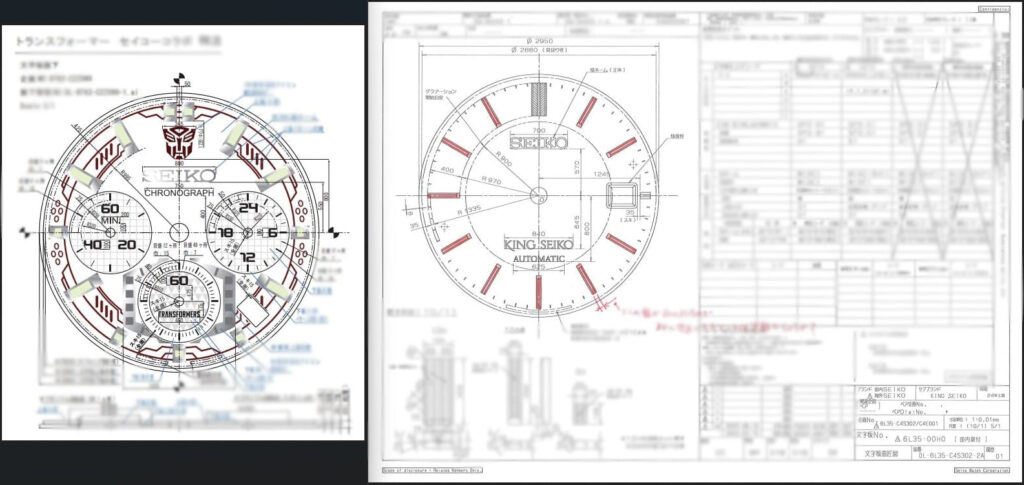
RestorePrivacy has seen watch designs and schematic diagrams disclosing precise dimensions, some technical data about internal mechanisms such as dual spring barrels, what appears to be lab test results for materials used in the watches, ID cards, passports, and internal email communication. We have blurred the schematics below to avoid exposing Seiko’s intellectual property.
RestorePrivacy
This controlled data disclosure process aims to showcase select stolen files to the affected party, emphasizing the advantages of settling the ransom over facing the repercussions of a public data leak. In this case, revealing confidential technical details about Seiko watches might provide competitors an opportunity to bridge the gap by replicating or reverse-engineering proprietary technology. Simultaneously, brands selling counterfeit products could leverage the exposed information to produce imitations that are more indistinguishable from authentic Seiko pieces.
Typically, ransomware perpetrators give companies a timeframe to meet their monetary demands before publicly releasing the stolen data. However, in this instance, BlackCat hasn’t initiated a countdown yet. It’s plausible that these details are negotiated privately between the threat actors and the company’s agents, although it is unknown if Seiko has opted to engage with the cybercriminals or decided to dismiss the blackmail.
The watchmaker closes its data breach notice statement by urging its customers and business partners to inform them immediately should they receive an email that spoofs the brand, as that would help track down the threat actors. Also, organizations working with Seiko are advised to be very cautious from now on, as a single employee clicking on a phishing link could be enough to compromise their network too.







This is scaring, almost everyday happens a data breach from a big company or government agency. Thank you for the information Heinrich!
I was gonna say the mysterious user strikes again but this time you made a very good point.
Nicely done user 😉