
Cloudflare has successfully disrupted a phishing campaign by the Russia-aligned threat actor FlyingYeti, which targeted Ukraine.
The operation involved the detection, denial, degradation, disruption, and delay of malicious activities aimed at exploiting Ukrainian citizens' anxieties over housing and utility debt.
FlyingYeti discovery and disruption
The investigation revealed that FlyingYeti began its campaign in April 2024, leveraging the increased financial pressure on Ukrainians following the January 2024 lifting of a moratorium on evictions and utility service terminations. This moratorium had been in place since February 2022, at the onset of Russia's invasion of Ukraine, and its removal resulted in significant debt liabilities for many Ukrainian citizens.
FlyingYeti exploited this situation by using debt-themed phishing lures, enticing targets to open malicious files that would infect their systems with COOKBOX malware. This malware, once activated, allowed FlyingYeti to install additional payloads and gain control over the victim's system.
Cloudflare's proactive measures began on April 18, 2024, when they detected FlyingYeti preparing to launch the phishing campaign. The threat actor's tactics, techniques, and procedures (TTPs) closely resembled those of UAC-0149, a group previously tracked by the Ukrainian CERT.
Cloudflare observed FlyingYeti conducting reconnaissance throughout the operation, creating lure content, and developing malware iterations. By mid-May, just as FlyingYeti was about to deploy its final COOKBOX payload, Cloudflare successfully disrupted the campaign.
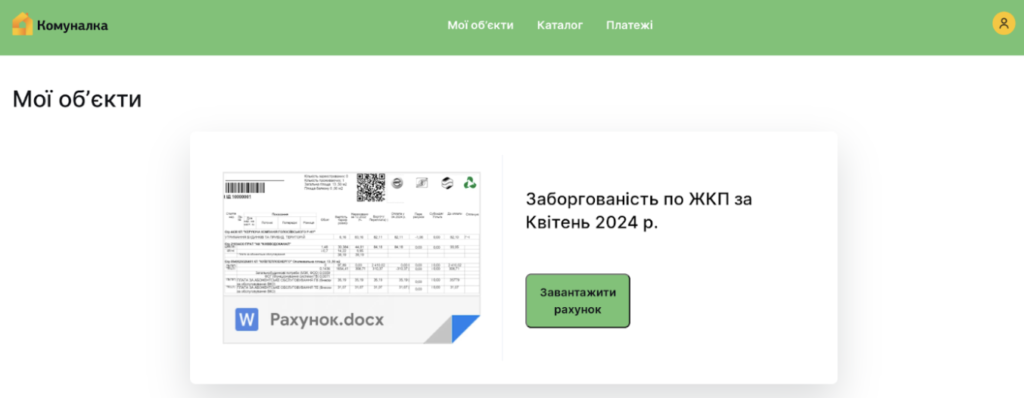
FlyingYeti's phishing lures involved spoofed payment notices hosted on a GitHub page mimicking Kyiv's Komunalka housing site. Victims were directed to download a malicious RAR file, deceptively presented as an overdue invoice.
Cloudflare
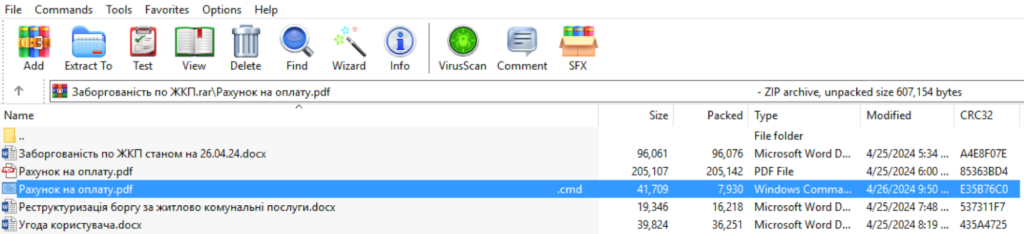
This RAR file exploited the WinRAR vulnerability CVE-2023-38831 to execute a CMD file containing the COOKBOX malware. The CMD file, cleverly disguised with a Unicode character to appear as a benign PDF document, facilitated the malware's persistence and control over infected devices. Additionally, the phishing site included decoy documents with tracking links to enhance the legitimacy of the malicious operation.
Cloudflare
Cloudflare's defense measures significantly impacted FlyingYeti's operations. The team detected and took down several of FlyingYeti's Cloudflare Workers and GitHub repositories. By coordinating with GitHub and other industry partners, they removed the malware and phishing sites, effectively extending the threat actor's operational timeline from hours to weeks.
Each time FlyingYeti adapted its tactics—switching malware delivery methods and using alternative file-sharing sites—Cloudflare effectively countered its moves. Still, this shows the threat actor's persistence and adaptability.
FlyingYeti, also tracked as UAC-0149, primarily targets Ukrainian defense entities and uses dynamic DNS (DDNS) and cloud platforms for hosting malicious content. The group's activities suggest alignment with Russian interests, as indicated by Russian-language code comments and operational hours matching the UTC+3 time zone.
Defense recommendations
To mitigate threats like FlyingYeti's phishing operations, Cloudflare recommends the following actions:
- Isolate critical applications and enforce strict access controls.
- Ensure all systems, including WinRAR, are up-to-date with the latest security patches.
- Use email security solutions to detect and block phishing attempts.
- Employ tools like CrowdStrike or Microsoft Defender to monitor and analyze binary execution on hosts.
- Identify potential infections by searching for specific IOCs related to FlyingYeti's activities.






Leave a Reply