
/
Earlier this month the FBI issued a cybersecurity alert to US businesses about Eastern European ransomware gangs sending out malicious USB drives. Today, a prolific hacking group has announced they are selling data obtained from hacking Lockheed Martin. The hacking group has already published samples of the data and provided us with exclusive commentary on their attack methods using malicious holiday gifts.
Just a few weeks after the FBI issued a cybersecurity alert to US businesses about ransomware gangs sending malicious USB drives, it appears that one of the world\'s largest aerospace and defense contractors may have fallen victim to a similar attack.
Earlier today, a well-known hacking group made a post on a popular hacking forum advertising internal documents from Lockheed Martin. We examined a sample of the documents and also obtained exclusive commentary from the hacker group, including how they claimed to have breached Lockheed Martin's network by sending select employees gifts during the 2021 holiday season.
The threat actor, who goes by the username 1941Roki (but uses a different name on Telegram), is now offering all of the data obtained from Lockheed Martin for sale for $999. The post is currently visible on the hacking forum and includes internal documents from Lockheed Martin as proof of the breach.
The hacker claims to have 40 GB of internal Lockheed Martin documents, including:
- Design drawings
- Design documentation
- Test records
- Active projects (Indago 4)
- Contract details
Below is the original post from user 1941Roki. It directs interested parties to Telegram, where the group maintains a public channel with proof and documentation from this alleged hack, as well as other past breaches. There is also a private channel for direct communication with the group.
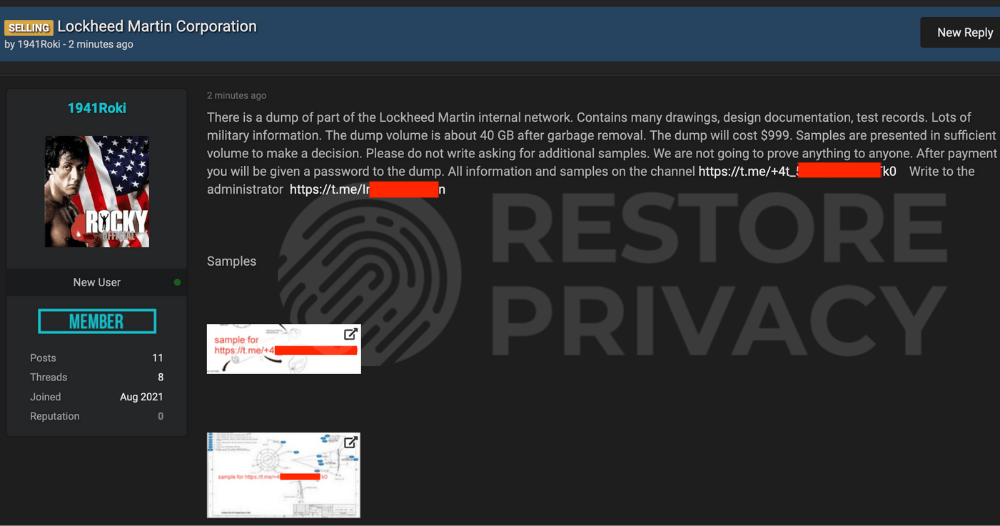
The hacking group posted a selection of Lockheed Martin documents in both the hacking forum and also on the group's public Telegram channel.
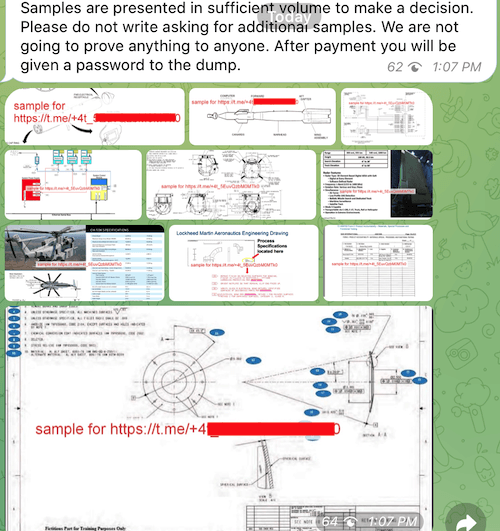
We asked the hackers if they obtained any data on active contracts and/or defense projects, and they had this to say:
I can say to representatives of the corporation about the interest of interested persons to the company's defense contracts with the government. The highlight will be the disclosure of the technical documentation of Indago 4 that the corporation collected along with PacketDigital and Sanadianuavs – contracts for the supply of components with these corporations as well as in the dump.
–1941Roki hacking group\'s statement to RestorePrivacy
The hacking group also provided us with an explanation for how they obtained access to Lockheed Martin's network.
Malicious holiday gifts for Lockheed Martin employees
The group claims to have hacked Lockheed Martin's network earlier this month, in January 2022, for a particular client. However, because the hacking deal allegedly fell through, the group is now publicly selling the data.
Most interesting, however, is how the group claims to have gained access. They told us that the attack first involved network analysis, then identifying Lockheed Martin employees who “had access to the technical information… but did not have sufficient qualifications in the field of information security” — and finally targeting these employees with holiday gifts.
In our communications with the group earlier today, we sent a few private questions and were given the answers below.
The process of obtaining data is presented by real Christmas history. We analyzed the security of the internal network of the company and came to the conclusion that it would not be crazy. So we analyzed LinkedIn information, compared it with other leaks and on the basis of this selected several employees of the company. Who, in our assumption, had access to the technical information you are interested in, but did not have sufficient qualifications in the field of information security. These employees received pleasant baubles [trinkets] on Christmas holidays.
The most difficult was to choose what a person with a lot of probability will take to work. It was much easier to establish a certain technical stuffing in our gifts (full of services that offer these services for your needs). That is, the answer to your second question is insider employees who did not understand their status. And at the beginning of January a signal was received from two of our gifts. Next, just technical work. I want to notice the professionalism of corporate employees – they are pretty quickly visited and localized our access, which unfortunately led to such a small amount of data obtained. We tried to reach representatives of the company with a coating path with a proposal to resolve information security incident. But unfortunately we did not receive an adequate answer from them.
–1941Roki hacking group\'s statement to RestorePrivacy
This lines up exactly with the FBI security alert from earlier this month about hackers targeting defense contractors and other industries with malicious USB drives.
Bleeping Computer was the first to report on this trend and the FBI's announcement a few weeks ago. According to their report,
The Federal Bureau of Investigation (FBI) warned US companies in a recently updated flash alert that the financially motivated FIN7 cybercriminal group targeted the US defense industry with packages containing malicious USB devices to deploy ransomware.
The attackers mailed packages containing ‘BadUSB' or ‘Bad Beetle USB' devices with the LilyGO logo, commonly available for sale on the Internet.
Additionally, this group's posting history on the hacking forum and Telegram channel suggests a connection to eastern Europe. Previous posts includes leaks on Russian and Ukrainian residents.
We have reached out to Lockheed Martin for a comment on this situation and will update this report with any new information we receive.







Damn, this attack is nearly as sophisticated as the one from the US on Iran’s (Stuxnet) nuclear uranium refineries. Executed in the same way but for different goals.
Hi Sven,
Great article.
I have been reading around your sites and have noticed how current and regularly update your guides are.
All the time and effort you and your team put in is very much appreciated.
Regards
BoBeX
Thanks BoBeX
I have found USB’s in parking lots before that even I coudnt resist plugging in . However , I have a technical background and used Linux for being curious . Worst case : it ask me for my password ? I am always disappointed so far by the way . I have found a guys music collection .
Cant I get lucky and find the guy that keeps his passwords in nice, neat, named, text files :/
It has to exist .
Yep there have also been studies where researchers dropped USB drives around college campuses to see how many people would plug them in and then the USB drive would “phone home” for the study:
“48 percent of drives were picked up and plugged into a computer with the user clicking on files”
https://threatpost.com/never-trust-a-found-usb-drive-black-hat-demo-shows-why/119653/
Hi Anonymous,
Have you ever tried one with out storage, instead capacitors?
BoBeX