
1Password has introduced a new browser-based phishing protection feature to intercept credential theft before it happens, in response to a surge in AI-generated phishing attacks that are becoming harder for users to detect.
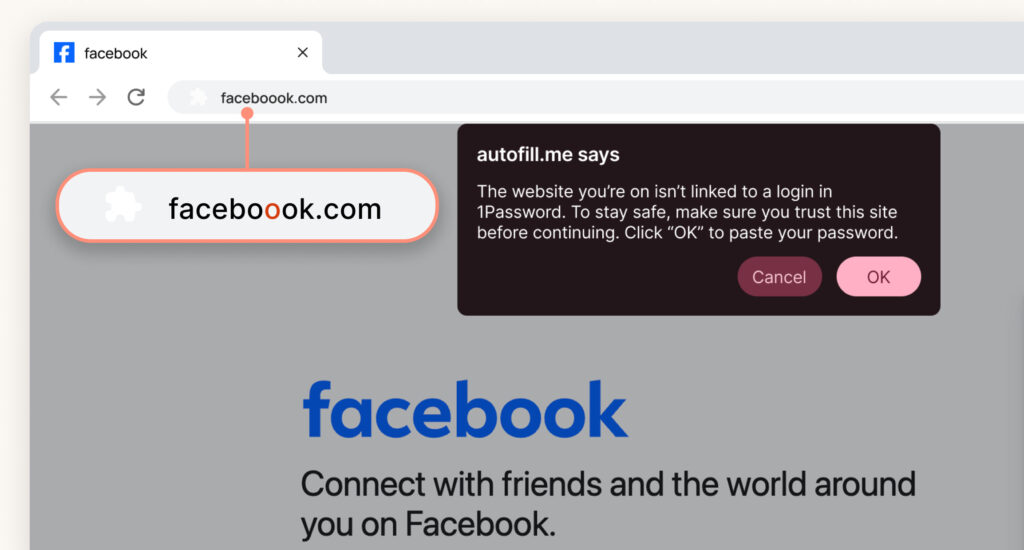
The feature, now rolling out to individual, family, and business users, enhances 1Password’s autofill security by adding a critical warning step when login credentials are used on suspicious websites. Previously, if a user visited a URL that didn’t match their saved login, 1Password would simply withhold autofill. Now, if the user attempts to manually paste their credentials, the browser extension will display a real-time warning pop-up, urging caution and effectively acting as a second layer of protection against fraudulent sites.
1Password
This development comes amid a marked increase in phishing attacks fueled by generative AI, which enables threat actors to craft convincing emails, websites, and even voice calls that bypass traditional detection methods. The warning system is designed to alert users to subtle URL mismatches, such as a single extra character in a domain name, that might otherwise go unnoticed.
For 1Password’s individual and family plan users, the feature will be enabled by default. Business customers can activate it via the Authentication Policies section of the 1Password admin console.
Response to AI-driven threats
The feature’s release coincides with new internal research from 1Password that highlights the scale and complexity of modern phishing. In a survey of 2,000 American adults, the company found that 89% have encountered phishing scams and 61% have been successfully phished.
The phishing tactics described often exploit urgency and emotional response, such as fake job offers, legal notices, or time-limited sales. These lures are becoming more believable thanks to AI tools that allow scammers to mimic brands and writing styles with unprecedented precision.
For enterprise environments, the stakes are even higher. Phishing remains the leading cause of ransomware breaches, with stolen credentials serving as the attacker’s entry point into corporate networks. 1Password warns that poor password hygiene, such as reusing passwords, neglecting MFA, or using default credentials, continues to be a systemic vulnerability in organizations.
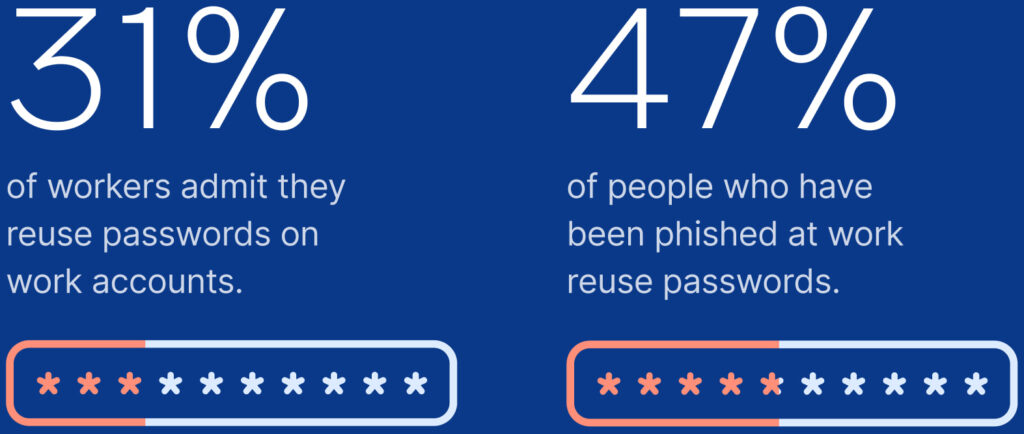
The company’s survey data reflects that 36% of workers admitted to clicking suspicious links in work emails, with 26% of those cases involving fake messages from HR or management. Unsurprisingly, employees who believed phishing prevention was solely IT’s responsibility were significantly more likely to fall for scams.







Leave a Reply