
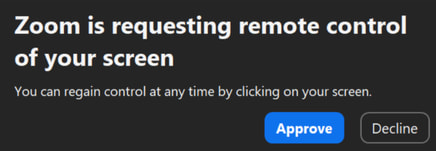
A new campaign by ELUSIVE COMET, a threat actor responsible for large-scale cryptocurrency thefts, exploits Zoom's remote control feature through social engineering.
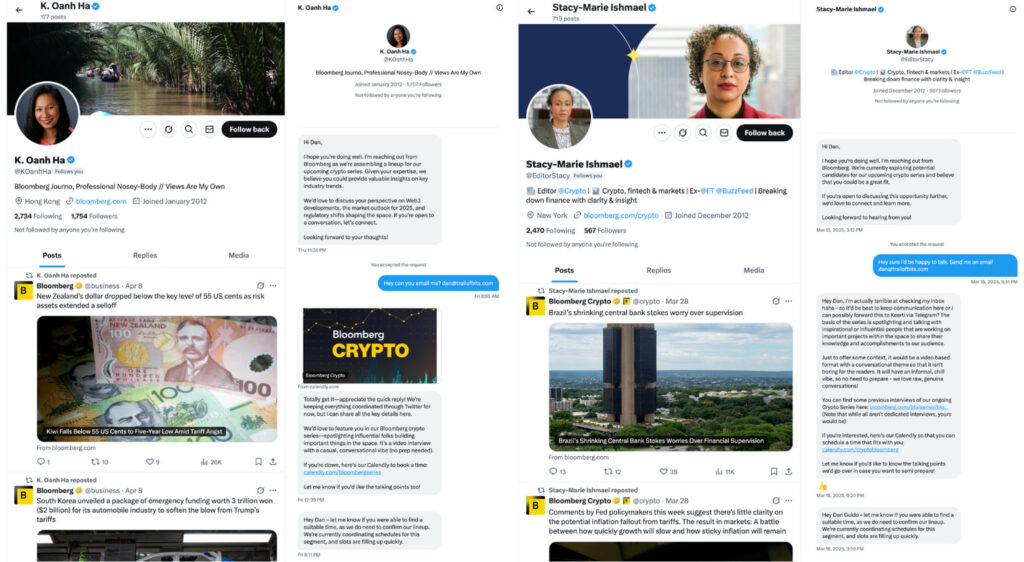
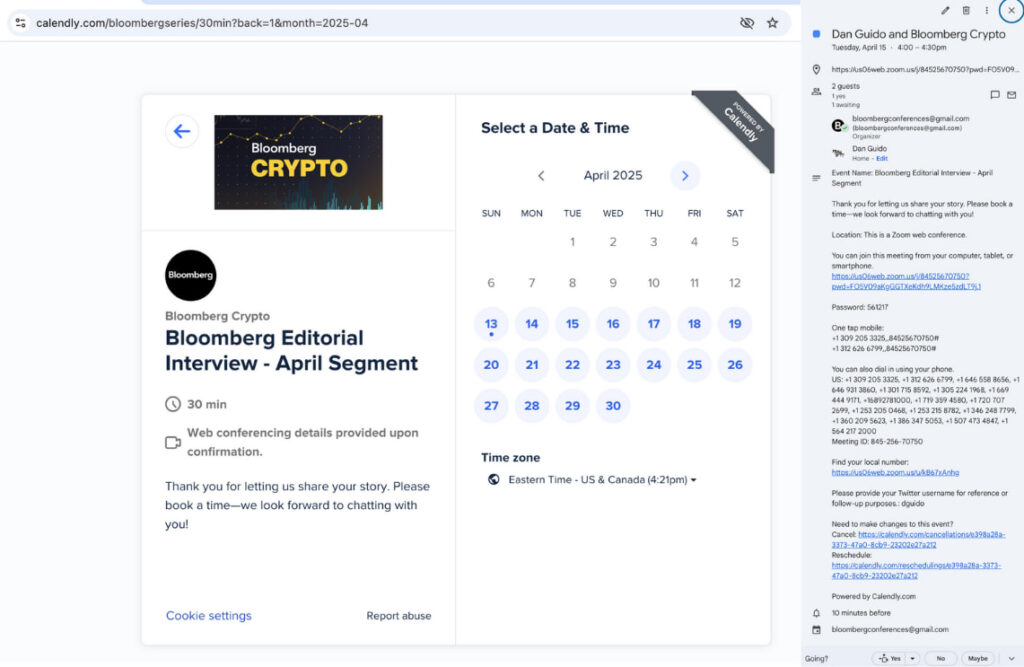
The attack came to light when Dan Guido, CEO of Trail of Bits, received a fraudulent interview request supposedly from “Bloomberg Crypto” via Twitter. The request, routed through unofficial Calendly links and Gmail addresses, exhibited suspicious traits — such as avoiding email communication and mimicking legitimate business workflows — that raised red flags for the security-conscious executive. The firm traced the origin to ELUSIVE COMET, a threat actor previously linked to the $1.5 billion Bybit breach earlier this year, which similarly relied on human error over code flaws.
The ELUSIVE COMET operation weaponizes a legitimate Zoom feature that allows one participant to request remote control of another's machine during screen sharing. The attackers exploit this feature by renaming themselves to “Zoom,” making the permission prompt appear as a benign system message. During fake interviews or business meetings, victims — often distracted and under time pressure — may unknowingly grant full access to their systems. This access enables attackers to install malware, steal credentials, or siphon cryptocurrency wallets with little resistance.
Trail of Bits
Indicators of compromise (IoCs) uncovered by Trail of Bits include several new attacker-controlled accounts and domains:
- X accounts: @KOanhHa, @EditorStacy
- Email: bloombergconferences[@]gmail.com
- Zoom meeting URL: us06web[.]zoom[.]us/j/84525670750
- Calendly URLs: calendly[.]com/bloombergseries, calendly[.]com/cryptobloomberg
Trail of Bits
The success of this campaign lies in its nuanced understanding of user behavior and interface design. Rather than relying on malware delivery through exploits, ELUSIVE COMET capitalizes on interface ambiguity, trust in routine business processes, and human habituation. By embedding the attack in seemingly legitimate video calls, attackers bypass traditional defenses entirely.
Trail of Bits
To counteract this threat, Trail of Bits has implemented a rigorous multi-layered defense strategy focused on endpoint hardening, strict access control, and proactive communication policies.
The firm also highlights the effectiveness of PPPC profiles in denying Zoom accessibility permissions at the system level — preventing the remote control feature from functioning altogether. For environments that must retain Zoom, a TCC monitoring script is shared that runs every 15 minutes to revoke any permissions that may have been granted, maintaining a clean operational state. For high-security setups, Zoom should be removed entirely.
Beyond technical countermeasures, Trail of Bits emphasizes user awareness and organizational processes. Employees are trained to spot unusual permission requests and verify all external engagements through official channels.
The ELUSIVE COMET case underscores a shift in the threat landscape where attackers prioritize psychological manipulation over technical exploits. As video conferencing becomes embedded in business workflows, familiar tools like Zoom can become high-risk vectors unless proactively constrained.







Leave a Reply