
A sweeping new study by Citizen Lab and Princeton University reveals that nearly half of the most popular Android apps on Xiaomi's Mi Store use insecure, proprietary cryptographic protocols instead of industry-standard TLS, exposing users to surveillance and data theft.
Xiaomi Mi Store falls short under scrutiny
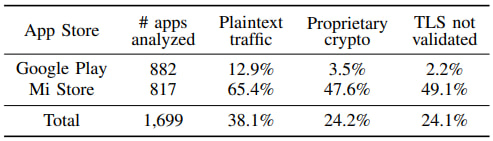
The project, dubbed WireWatch, analyzed 1,699 Android apps — 882 from the Google Play Store and 817 from the Mi Store. Researchers found that 47.6% of the Mi Store apps deployed non-standard cryptographic schemes, compared to only 3.5% on the Play Store. Critically, 8 out of 9 major proprietary protocol families were found to be vulnerable to network decryption by eavesdroppers, enabling attackers to read user browsing data, extract device metadata, and even access local files.
The study, conducted in late 2024 and presented at the 2025 IEEE Security and Privacy Symposium, attributes these weaknesses to cryptographic systems developed by Chinese tech giants including Alibaba, Tencent, iQIYI, Kuaishou, and others. Protocols were commonly implemented via third-party SDKs bundled into many apps, affecting a staggering 26.9% of the Mi Store dataset, which represents roughly 130 billion cumulative downloads.
These “home-rolled” cryptosystems often made fundamental mistakes such as:
- Use of deprecated or broken algorithms like DES and AES in insecure modes such as ECB and CBC, often without any authentication.
- Static or guessable keys, sometimes derived from hardcoded values or weak random sources.
- Improper TLS usage, with 49.1% of Mi Store apps failing to validate TLS certificates, rendering them vulnerable to MITM attacks.
- RSA encryption without OAEP padding, enabling chosen-ciphertext attacks to extract encryption keys.
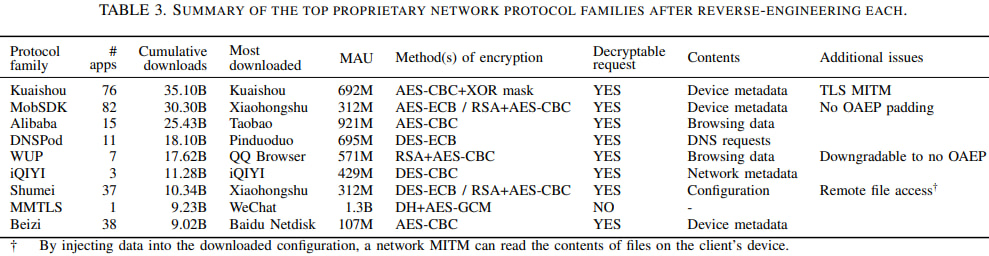
Among the worst offenders was Tencent WUP, that when used in QQ and Sogou browsers, allowed attackers to downgrade encryption and exploit RSA oracles to extract AES keys. Also, Shumei SDK exposed a regex-based file access mechanism that let network adversaries extract data from files on the user's device using response size as a side-channel. Finally, Kuaishou SDK sent encrypted data over TLS without validating server certificates, undermining any benefits of the encryption.
Notably, the more popular an app was, the more likely it was to use proprietary encryption. For apps with over one billion downloads, 67.2% employed such insecure protocols. Apps with under 50 million downloads dropped to 40.8%.
Like many Chinese app ecosystems, Xiaomi's Mi Store lacks the security oversight seen on the Google Play Store, including mandatory TLS validation and transparency requirements. While Google Play applications must disclose whether they encrypt data in transit, no such requirement exists in Chinese stores, despite claims of manual security reviews.
The researchers coordinated disclosures with affected vendors starting in November 2024. While iQIYI, Kuaishou, MobTech, and Tencent acknowledged the issues and began issuing patches, others, including Alibaba and Shumei, failed to respond by the April 2025 deadline.







Leave a Reply