
WhatsApp has patched a critical zero-click vulnerability that was exploited in the wild in a sophisticated campaign targeting Apple users.
The flaw, tracked as CVE-2025-55177, was reportedly combined with a recently disclosed Apple zero-day (CVE-2025-43300) to deliver spyware without requiring user interaction.
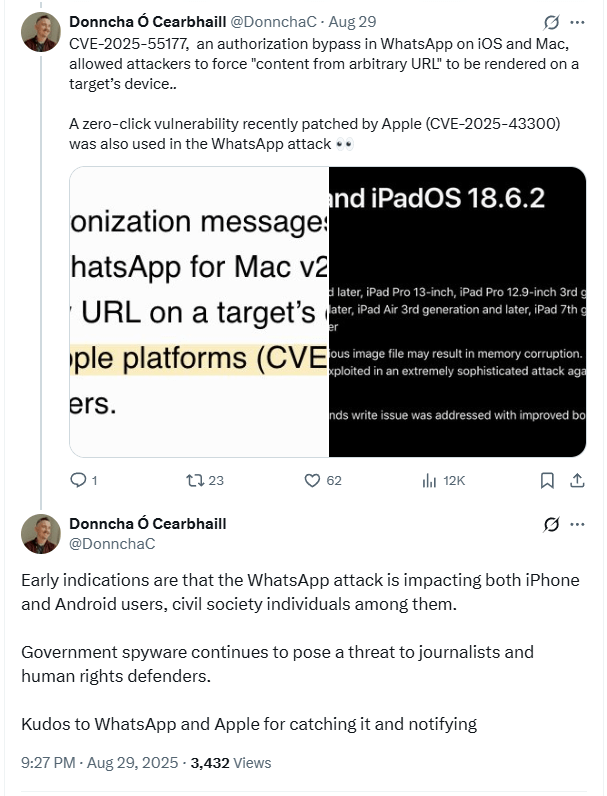
WhatsApp disclosed the vulnerability in a security advisory published late Friday, noting that it was discovered internally by its security team. The flaw affects WhatsApp for iOS versions prior to 2.25.21.73, WhatsApp Business for iOS versions prior to 2.25.21.78, and WhatsApp for Mac versions prior to 2.25.21.78. The vulnerability stems from incomplete authorization checks in the synchronization mechanism used by linked devices. This oversight allowed attackers to force a target’s device to fetch and render content from an arbitrary URL, essentially giving remote actors control over what the device would process without user input.
WhatsApp, owned by Meta, is one of the most widely used messaging platforms globally, with over two billion users. It supports device linking for multi-device access, a feature that was at the heart of this security lapse.
Citizen Lab’s security researcher Bill Marczak highlighted on X that this WhatsApp bug served as a delivery vector in a zero-click attack chain. The full exploit sequence leveraged CVE-2025-43300, a zero-day vulnerability in Apple’s Image I/O framework, which Apple patched earlier this month. That flaw allowed attackers to compromise devices by embedding malicious code in image files, an ideal pairing for the WhatsApp bug, which could silently fetch and display such content.
CVE-2025-43300 was fixed on August 20, 2025, in iOS 18.6.2, iPadOS 18.6.2, macOS Sequoia 15.6.1, and other corresponding OS versions. The bug, caused by an out-of-bounds write issue in Image I/O’s image parsing logic, affected nearly all current Apple devices, including iPhones, iPads, and Macs. By corrupting memory during image handling, the flaw enabled arbitrary code execution, facilitating complete device compromise when combined with another delivery mechanism, such as CVE-2025-55177.
According to Amnesty International’s Security Lab, Android users were also affected. The organization’s head of security, Donncha Ó Cearbhaill, confirmed that his team is assisting multiple individuals targeted by the campaign, many of whom are from civil society, including journalists and human rights defenders.
WhatsApp has issued targeted threat notifications to impacted users, advising them to seek expert support.
Users should update their WhatsApp apps to version 2.25.21.73 or later on iOS, 2.25.21.78 or later on macOS, and also ensure they have patched CVE-2025-43300. Also, consider enabling Lockdown Mode on iOS or Advanced Protection Mode on Android, which harden device security against zero-click and spyware attacks.







Leave a Reply