
Researchers from PCAutomotive have uncovered several vulnerabilities in Skoda and Volkswagen vehicles, which could allow attackers to access sensitive systems, disable vehicles, or extract user data.
HThe vulnerabilities were discovered by PCAutomotive security researchers during a detailed analysis of the Skoda Superb III 2022 (3V3) 2.0 TDI model. This mid-size car, part of the Volkswagen Group, uses the Modularer Querbaukasten (MQB) platform.
PCAutomotive
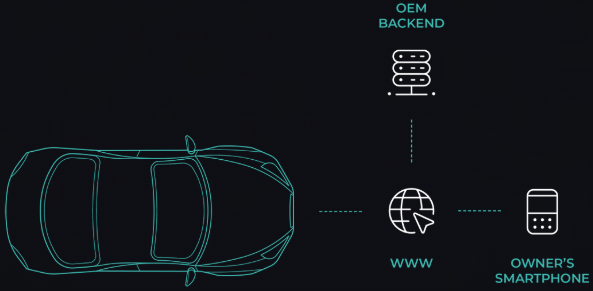
Key components affected by the researchers’ attack include the MIB3 infotainment unit, manufactured by Preh GmbH, which integrates Apple CarPlay, Android Auto, and MirrorLink for mobile device connectivity, the Telematics Control Unit (TCU), which provides over-the-air (OTA) updates and communication with backend servers via cellular networks, the OBD interface, which enables diagnostics and system commands, and the Skoda Connect Cloud Backend that hosts user and vehicle data.
The vulnerabilities uncovered by this research, presented earlier in the BlackHat Europe conference, include:
Denial-of-Service Attacks (CVE-2023-28898, CVE-2023-28899)
- MIB3 Infotainment Unit: Exploitable via Wi-Fi and Apple CarPlay connections to crash the unit, causing service disruptions.
- Engine Shutdown: Certain OBD commands could remotely disable the vehicle's engine and systems while in motion.
Debug Interface Access (CVE-2023-28895)
- Infotainment System: A hard-coded password on the Power Controller Chip (PWC) could allow attackers with physical access to extract and modify firmware, unlocking debug capabilities.
Weak Authentication on UDS Services (CVE-2023-28896, CVE-2023-28897)
- OBD Interface: Vulnerabilities in UDS authentication allowed attackers to extract passwords from CAN bus traffic and execute unauthorized diagnostic commands.
Data Leaks via Backend APIs (CVE-2023-28900, CVE-2023-28901)
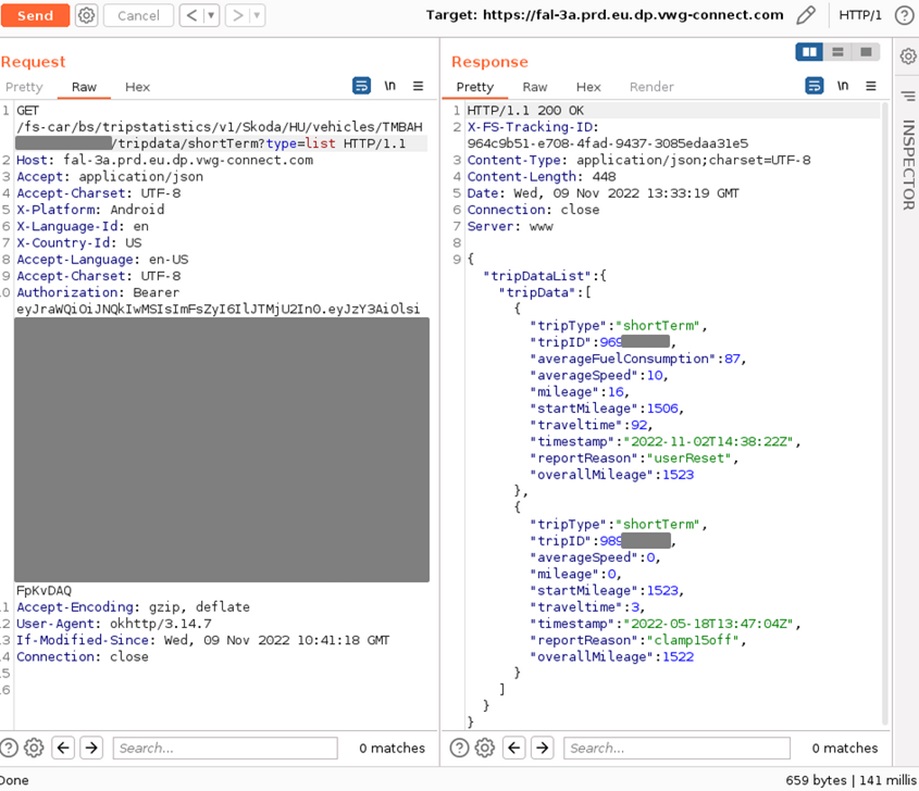
- Skoda Connect Cloud: An attacker could retrieve usernames, trip data, and sensitive vehicle details by exploiting improper access controls using Vehicle Identification Numbers (VINs).
Risks for Skoda owners
Exploitation scenarios for these vulnerabilities require varying levels of access, including physical and remote access.
In the first case, the debug interface and OBD vulnerabilities demand close proximity to the vehicle or its components. Remote access can open the way to exploiting the backend API flaws and in-car Wi-Fi. The researchers also note that installing rogue devices via OBD ports could allow long-term, persistent access to attackers.
PCAutomotive
While PCAutomotive confirmed that backend issues have been patched, fixes for the remaining vulnerabilities, particularly hardware-level flaws, have not been disclosed, so they’re assumed unfixed at the time of writing.
To mitigate these risks, car owners are advised to restrict physical access to the OBD port using a lockable cover, disable unnecessary wireless connectivity when not in use, and regularly update vehicle firmware and monitor manufacturer advisories.
For VW and Skoda, and car manufacturers in general, it is advised to strengthen debug and authentication mechanisms to prevent hard-coded passwords and weak encoding, implement robust access control for backend systems, and secure firmware update processes to prevent tampering.







Leave a Reply