
Attackers are using trojanized LetsVPN installers to silently deploy Winos v4.0, a stealthy, memory-resident malware that grants attackers remote access while bypassing traditional antivirus defenses.
The operation, tracked by Rapid7 and active throughout 2025, highlights the continued exploitation of popular VPN brands to distribute malware, marking the second major case involving LetsVPN in less than two years.
Rapid7 analysts uncovered this latest operation during a February 2025 MDR investigation. The campaign relies on tampered Nullsoft Scriptable Install System (NSIS) installers, embedded shellcode, and a multi-stage loader chain dubbed Catena. These elements work in concert to ensure that every stage of the malware, beginning with the fake VPN installer and ending with Winos v4.0, executes entirely in memory, effectively bypassing disk-based detection mechanisms.
LetsVPN, a popular mobile VPN product developed by LetsGo Network and boasting over a million downloads on Google Play, has once again proven to be a high-value lure for threat actors. In 2023, we reported on a separate case where copycat websites used the LetsVPN name to push malware families like BlackMoon, Farfli, and KingsSoft. That campaign relied on malvertising and typosquatting domains to trick users into installing fake VPN apps. In contrast, the current Winos v4.0 campaign involves signed Windows installers that convincingly mimic real LetsVPN software to target desktop environments.
LetsVPN loads Winos malware
In the latest variant, attackers use an installer labeled Lets.15.0.exe, which contains a validly signed decoy VPN executable (Iatsvpn-Latest.exe) and a series of malicious components staged across %LOCALAPPDATA% and %APPDATA%\TrustAsia. A loader named insttect.exe, disguised as a Tencent PC Manager setup, reads and executes Single.ini, a shellcode blob containing a reflectively loaded DLL. From there, the malware chain continues through intel.dll, additional .ini payloads, and finally culminates in the download of Winos v4.0 from attacker-controlled infrastructure.
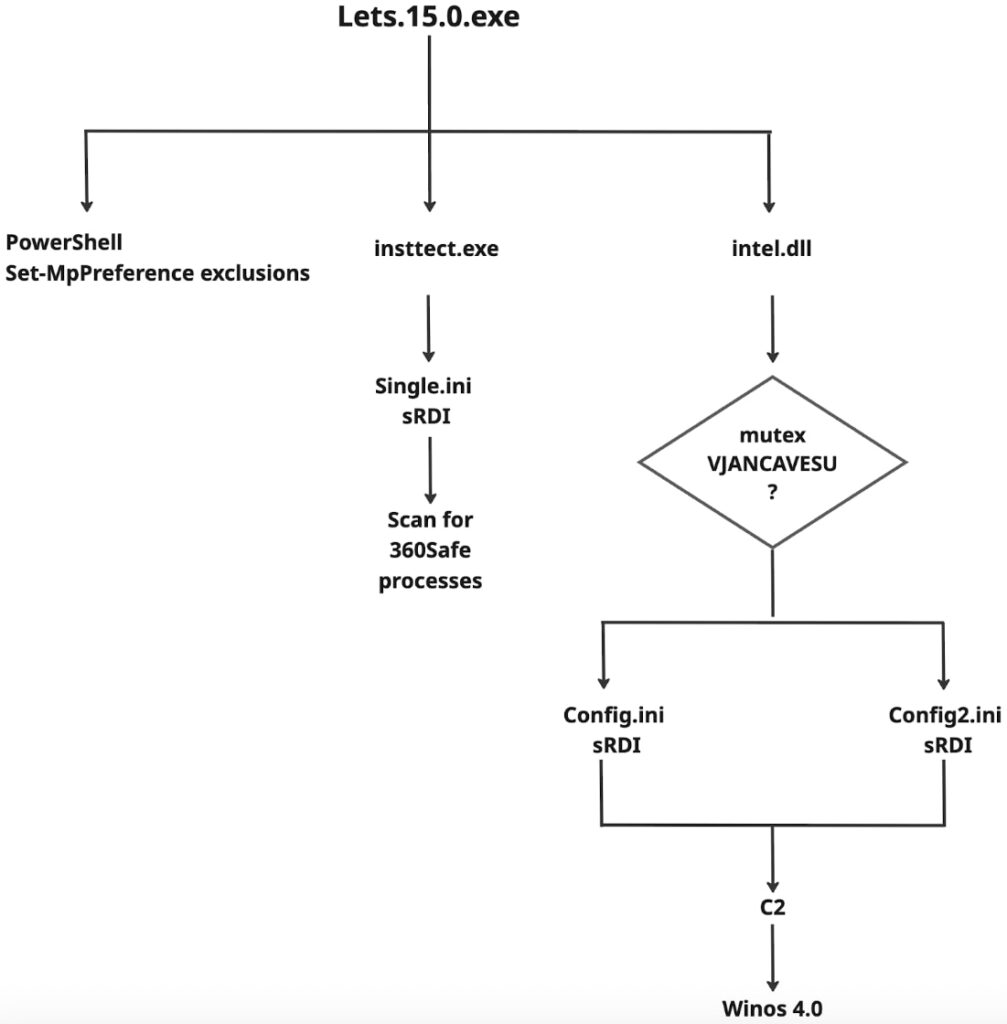
Rapid7
Winos v4.0 itself is a compact 112 KB stager embedded within sRDI-formatted shellcode. It exports a single function (VFPower), operates entirely in memory, and connects to hardcoded command-and-control servers using TCP and HTTPS. The configuration includes adjustable runtime behaviors, beacon intervals, and command flags for advanced control over infected hosts. Debug metadata embedded in the malware points to a Chinese-language development environment, and the campaign exhibits hallmarks of the Silver Fox APT group, which was previously linked to Winos deployments in operations such as CleverSoar.
Persistence mechanisms are equally elaborate. The malware sets PowerShell-based exclusions in Microsoft Defender, registers scheduled tasks, monitors key processes, and uses batch scripts as watchdogs. Notably, execution logic varies based on environmental indicators, such as the presence of messaging apps (e.g., Telegram or WhatsApp) or specific mutex handles.
The supporting infrastructure is spread across multiple servers, many of which are hosted in Hong Kong and linked to providers like Alibaba Cloud, OK COMMUNICATION, and MEGA-II IDC. Rapid7’s infrastructure mapping revealed over a dozen IPs distributing identical stage-one payloads, suggesting a well-resourced and centrally coordinated malware distribution network.
This campaign constitutes yet another example of the grave risks of downloading VPN software from unofficial sources. Avoid clicking on promoted search results or following download links for third-party sites, social media posts, and DMs.







Leave a Reply