
Kaspersky researchers have uncovered a crafty crypto fraud where scammers target dishonest cryptocurrency users by faking wallet leaks and manipulating them over several months. This scheme demonstrates how those attempting to steal can put themselves into a vulnerable situation and fall prey to scams.
Fraud details
Mikhail Sytnik, the web content analysts' team lead at Kaspersky, stumbled upon this scam through a forwarded Telegram message about a supposed cryptocurrency sale. The message contained a five-second video clip with a screenshot advertising a heavily discounted sale of two lucrative crypto projects.
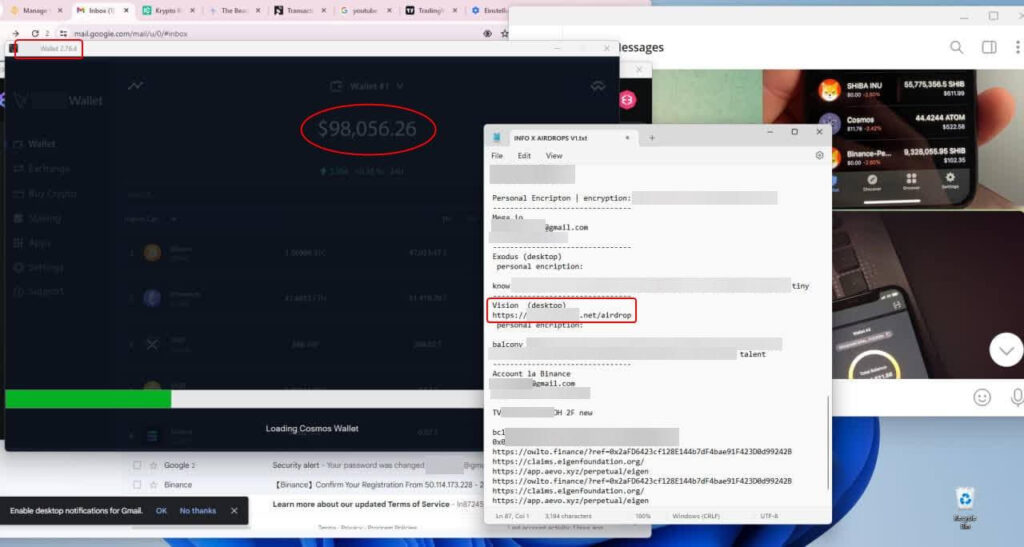
The clip led to a legitimate second-tier crypto exchange and a suspicious link that directed users to a server's root directory listing, displaying enticing file names. This setup made it appear as if the server had been misconfigured, exposing sensitive data such as wallet details, passwords, and seed phrases.
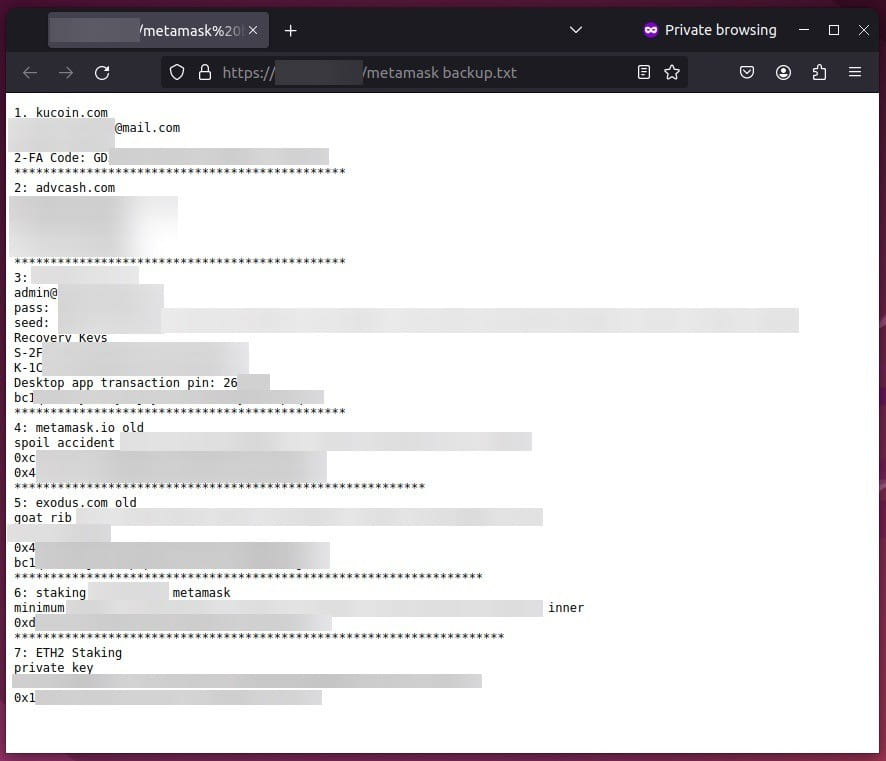
The files in the root directory were formatted in easily accessible types like TXT, PDF, PNG, and JPG, creating an illusion of genuine leaked data. Screenshots depicted a lavish lifestyle funded by substantial cryptocurrency balances, and text files contained comprehensive wallet details.
This convincing setup made potential victims believe they had stumbled upon a careless crypto owner's personal data, reducing their skepticism.
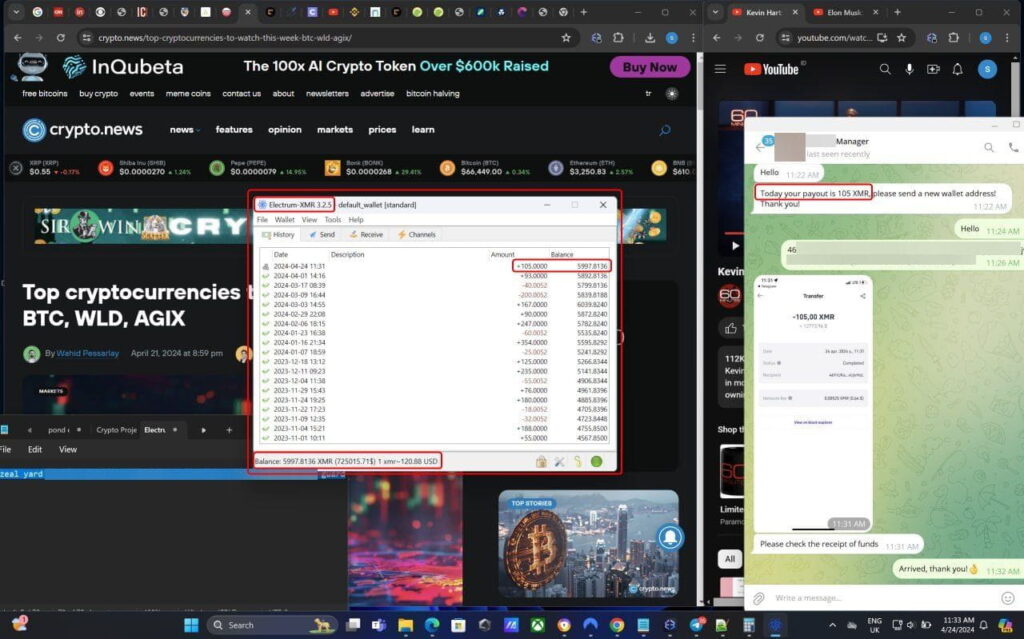
What made this scam particularly clever was that the wallet details were real, though the funds were staked and thus inaccessible. This gave the impression of authenticity, making victims less suspicious and more inclined to believe they had found a real leak. Kaspersky monitored the site for two months, observing no changes, indicating that scammers were waiting to attract a critical mass of interested users before proceeding to the next stage.
After a two-month pause, scammers updated the site with a new Telegram screenshot showing a Monero wallet with nearly a million dollars. A new text file with a seed phrase for the wallet appeared alongside the screenshot. Greedy users attempted to access the wallet, only to find that Electrum, the wallet app they tried to use, does not support Monero and requires a private key, not a seed phrase.
Desperate to access the funds, users searched for “Electrum XMR” or “Electrum Monero,” leading them to a fake website designed to look like an Electrum fork supporting Monero.
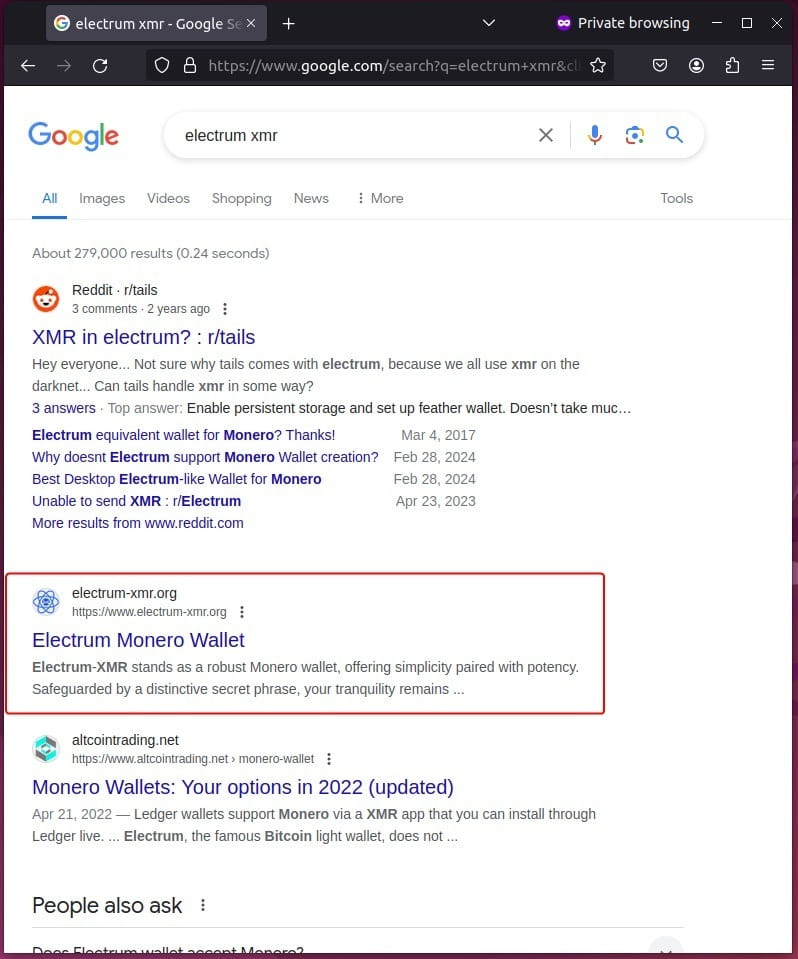
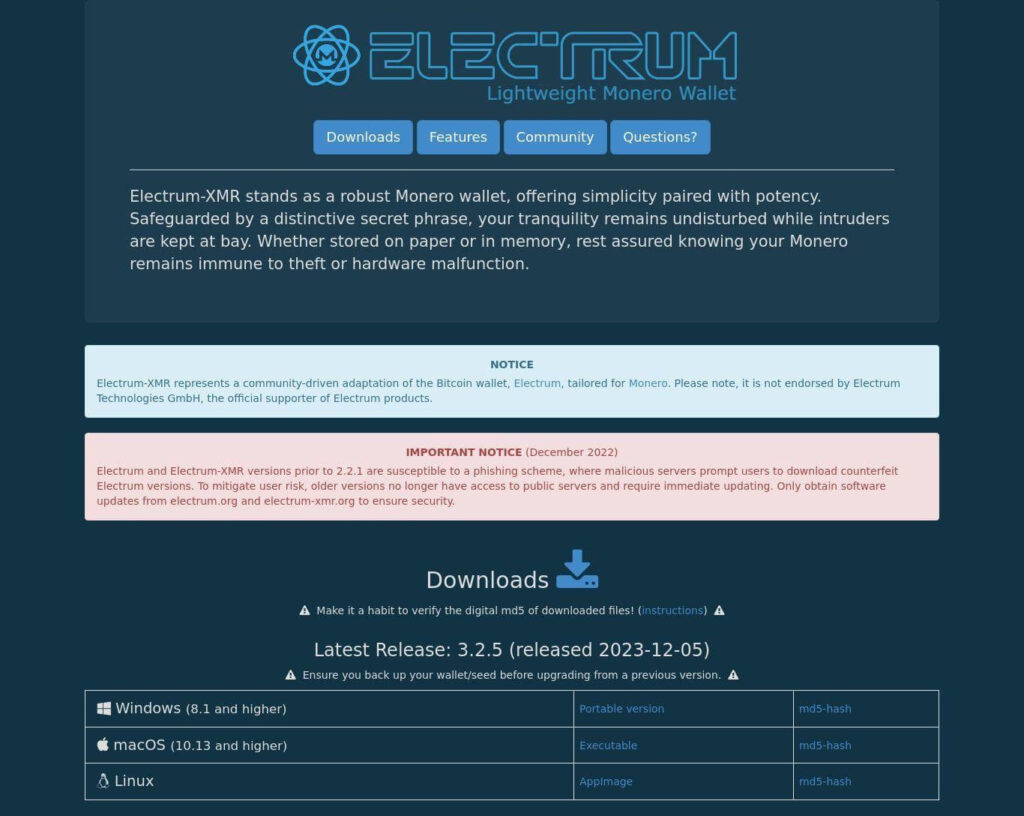
This site, which closely resembled the original Electrum website, offered downloads for macOS, Windows, and Linux, but the installers contained malware identified by Kaspersky as Backdoor.OLE2.RA-Based.a.
Other variants
After completing their investigation, Kaspersky noticed a second round of the scam. This time, the scammers were more direct, presenting a fake wallet balance alongside personal information and a link to a malicious site. This streamlined approach indicated the scam's effectiveness and the likelihood of more attacks of the same kind.
Victims of this scam, attempting to steal from others, ended up losing their own data and potentially their funds. Kaspersky emphasizes the importance of skepticism and caution when encountering seemingly lucrative opportunities. Key steps to avoid such scams include sticking to reputable crypto wallet apps and exchanges and ensuring you are signing in and downloading apps from the official project sites.







Leave a Reply