
A new malvertising campaign has surfaced, targeting users searching for Slack on Google. Discovered by Malwarebytes, this campaign highlights the growing sophistication and patience of threat actors who exploit online ad platforms to spread malware.
Malwarebytes reported nearly 500 malvertising incidents related to Google search ads in the past year. The latest campaign, however, stands out for its subtlety and meticulous planning. The threat actor behind this campaign used various online services to refine their target list and evade detection, ultimately aiming to infect users with a remote access Trojan (RAT).
Building legitimacy
The incident began with a seemingly legitimate Google ad for Slack. For days, when users searched for Slack on Google, they would see this ad displayed above the official Slack site in the search results. Initially, clicking the ad redirected users to Slack's official website, raising no immediate red flags. However, Malwarebytes' researchers noticed something unusual: the ad was linked to an advertiser that primarily targeted the Asian market, making the Slack ad appear out of context.
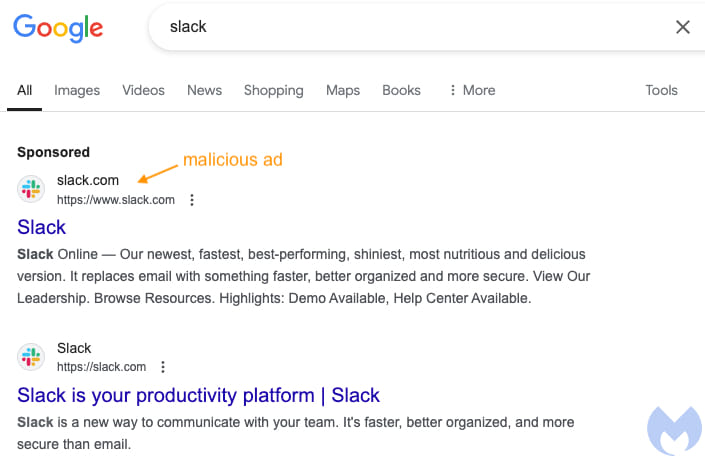
Malwarebytes
The research team used Google Ads Transparency Center to investigate further, which revealed the odd mix of promoted products. Contextual clues like these often help in identifying compromised advertiser accounts—a method Malwarebytes has successfully used to uncover other malicious campaigns.
Intent unveiled
After several days of monitoring, the ad's behavior changed. Instead of redirecting users to Slack's website, it began directing them through a series of click trackers. These trackers obscured the final destination, allowing the threat actor to filter traffic and redirect users to a domain of their choice. This tactic, known as “slow cooking,” is commonly used by malvertisers to avoid early detection.
The final URL, slack-windows-download[.]com, was registered just days before the attack. When initially accessed, the site displayed a decoy page with no malicious content. However, after adjusting various settings, the Malwarebytes team uncovered the real threat: a fake Slack download page designed to distribute malware. This tactic, known as “cloaking,” allows attackers to show different content to different users, making it harder for security tools to identify malicious behavior.
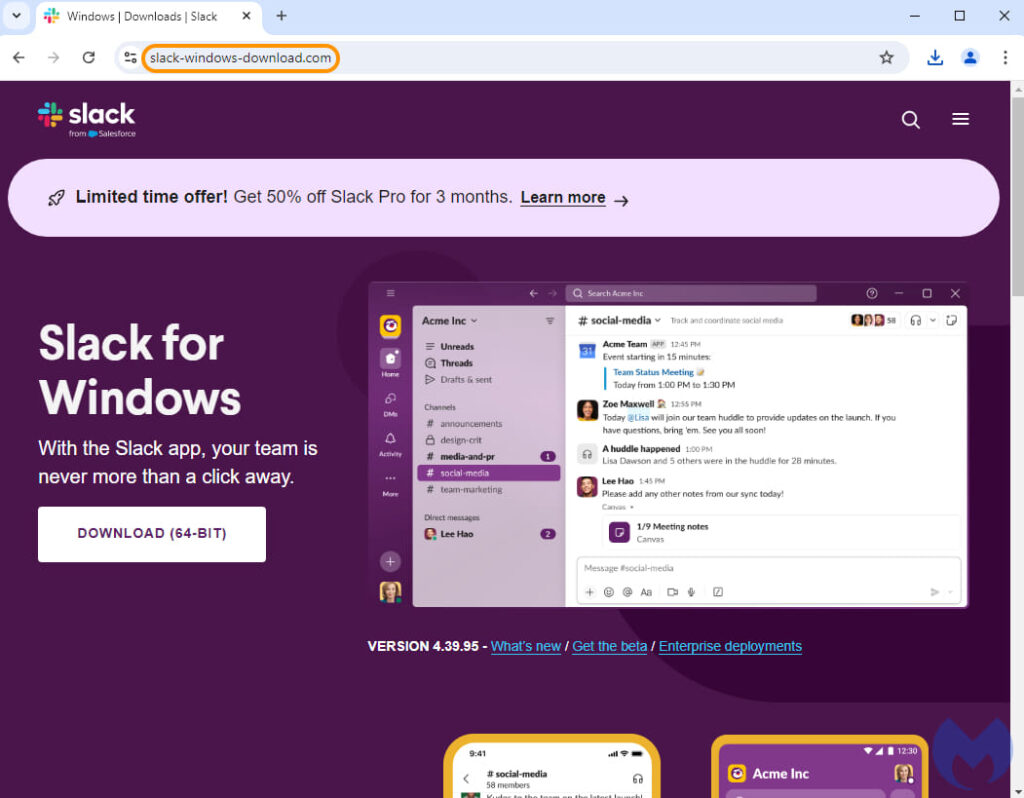
Malwarebytes
The fake Slack page hosted a download button that triggered the download of a malicious file from another domain. This domain suggested a parallel campaign targeting Zoom, indicating a broader attack strategy. The downloaded file connected to a server previously associated with SecTopRAT, a remote access Trojan known for its data-stealing capabilities. SecTopRAT has been linked to other malvertising campaigns, including one impersonating NordVPN.
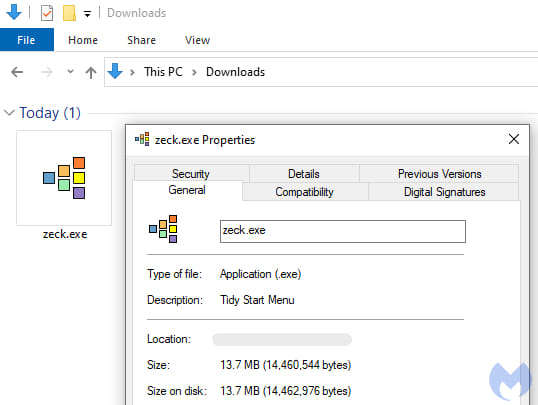
Malwarebytes
Response
Malwarebytes quickly moved to block the command-and-control server associated with the campaign. They also expanded their detection coverage to include the supporting infrastructure used by the attackers. The malicious ad was reported to Google, and the decoy domains were flagged as phishing by Cloudflare, which had been unknowingly providing services to the threat actor.
This incident underscores the need for vigilance when interacting with online ads, even those appearing on trusted platforms like Google. Users are advised to:
- Use a reputable ad blocker to mitigate exposure to malvertising campaigns.
- Verify URLs before clicking on ads, especially for popular software like Slack or Zoom.
- Keep security software up to date to ensure protection against the latest threats.
- Report suspicious ads to platforms like Google to help disrupt malicious campaigns.







Leave a Reply