
Troves of Real-Time Bidding (RTB) data used in digital advertising are now systematically abused by spyware makers to track billions of people worldwide.
The Irish Council for Civil Liberties (ICCL) has published a report highlighting the widespread misuse of sensitive RTB data, which lacks stringent control and security. The report also reveals the emergence of surveillance tools offered by private companies that utilize RTB for real-time spying.
ICCL’s investigation reveals massive potential for high-level compromise of sensitive organizations and personnel in the U.S. and Europe and underlines rampant data flow of key figures to foreign state and non-state entities in geopolitical rivals such as Russia and China.
The ICCL has published the full details of its investigation in two separate reports, one dedicated to the United States and a second focusing on the problem’s manifestation in Europe.
RTB system logic and abuse
RTB is a digital advertising buying process allowing advertisers to bid on ad inventory in real-time, directly or through representatives called “Demand-Side Platforms” (DSPs). The bidding process is based on various factors such as the user’s browsing behavior, demographics, and the context of the website, so for DSPs to bid, the websites will need to feed them with that information.
Advertisers specify the type of audience they want to reach based on factors like location, age, interests, etc., and how much they’re willing to pay for each impression, and the DSPs perform the bidding based on these parameters. The result is highly effective, targeted advertising that is more likely to lead to purchases.
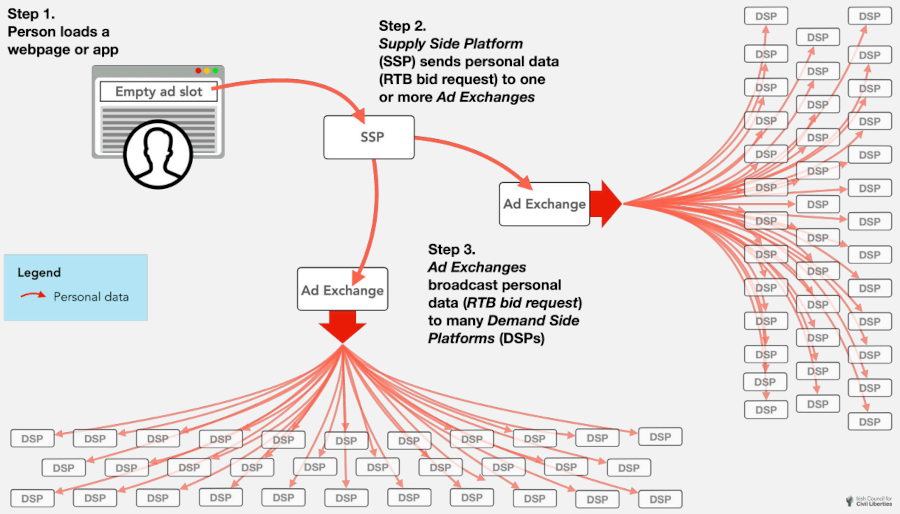
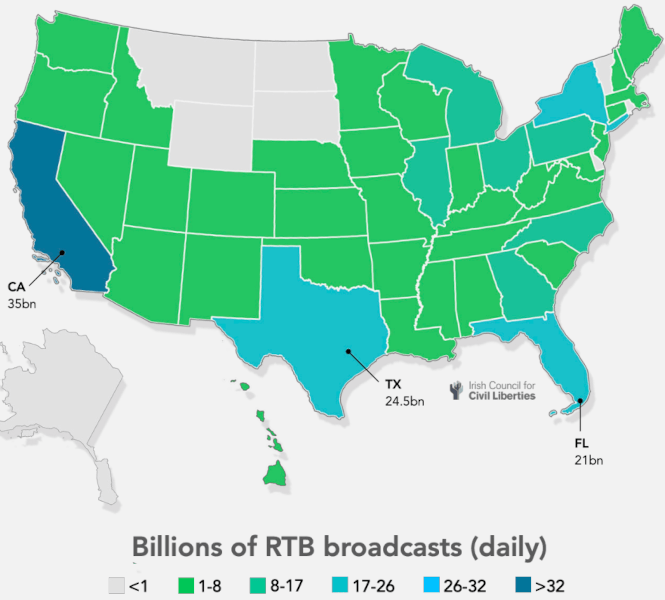
ICCL has found that Google sends RTB data to 2,051 entities, Microsoft to 1,647 DSPs, while Meta, Amazon, and other big tech firms follow similar practices. In the U.S., Google controls 10.5% of all RTB broadcasts, and its trackers are active on 15.6 million websites and apps. In Europe, Google holds 21% of the RTB space, while 79% is governed by the industry’s standards body, IAB TechLab.
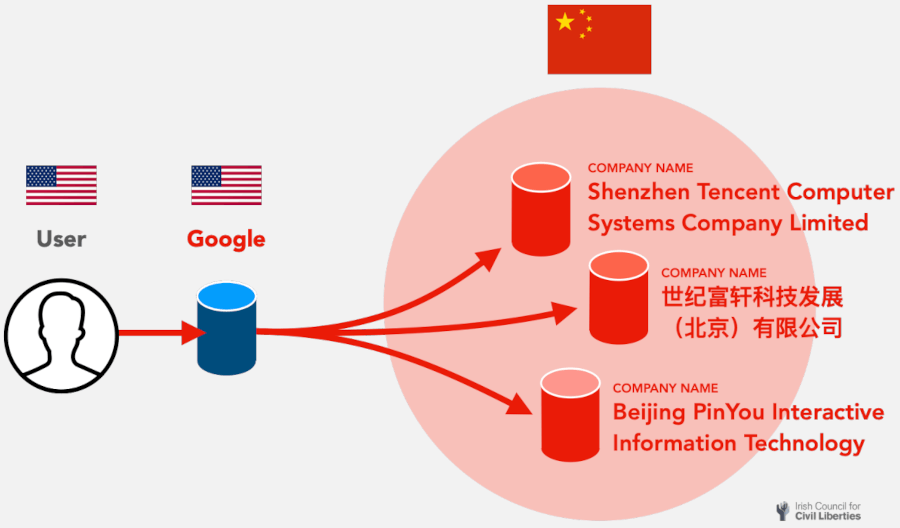
A big issue arising from RTB broadcasts is that the data they carry isn’t controlled or restricted, so DSPs may forward it to others for profit. In other cases, the DSPs themselves are companies based in China or Russia, having murky relations with the state, and possibly sharing that data or analysis of it for targeted surveillance.
“RTB data broadcasts reveal highly sensitive information about a person including location and movements over time, what they are reading or watching or listening to, sexual interests, and personal problems.”ICCL
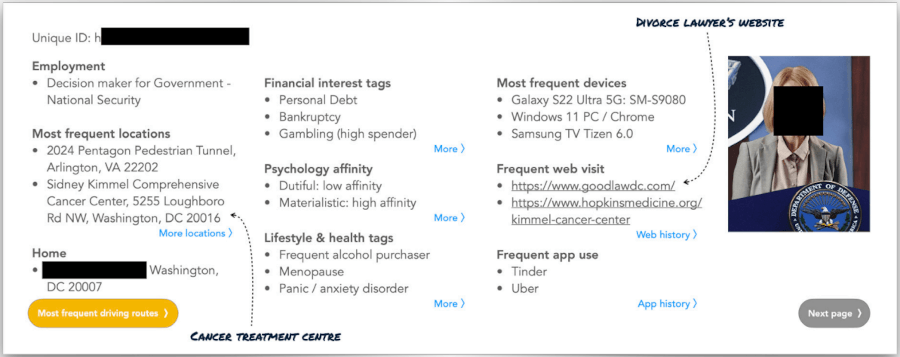
ICCL’s investigation located massive amounts of sensitive data in RTB marketplaces containing information about people working in government agencies and military organizations, lawmakers, judges, individuals working for aerospace and defense manufacturing firms, and even segments dedicated to their spouses and children.
Surveillance tools landscape
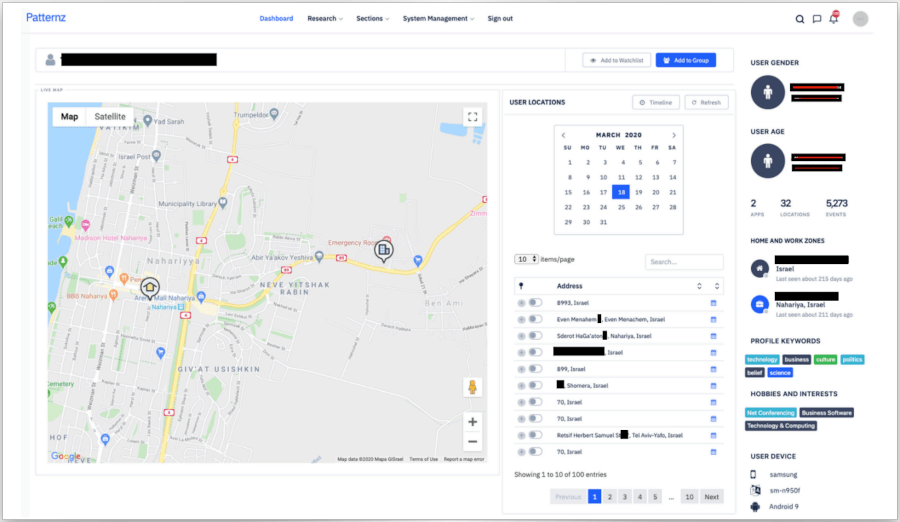
The report highlights a surveillance tool named “Patternz,” marketed by the private Israeli company ISA, which draws data from RTB broadcasts to provide real-time location for the target, historical activity dating back several months, driving paths, installed mobile apps, and identification of family members of co-workers. Patternz claims it has profiled 5 billion people, and on its website, it mentions the processing of 700,000 ad transactions per second to achieve unparalleled data flow.
A second example in the report is “Echo,” a surveillance tool developed by a private company named Reyzone. The firm operates its own DSPs to mass-collect data on internet users, serving advertisers and feeding its tool with tracking information.
Another case highlighted in ICCL’s report is that of Near Intelligence, a company that owns a DSP receiving RTB broadcasts from three ad exchanges. According to its website, it has leveraged this data to profile 152 million internet users in Europe, with information about their home addresses, workplaces, and frequently visited locations.
VPNs as mitigation
Apart from the high-level security and national risks highlighted in the report, ICCL’s findings serve as excellent reminders of the technical simplicity of user profiling and tracking and the normalization that underpins the process.
ICCL calls for the European Commission and the FTC in the U.S. to take immediate measures to strengthen the security of RTB broadcasts, apply strict controls over their transmissions and reach, and limit sensitive information in those packets. A comprehensive revision of the RTB system’s technical standards is called for, and at this stage, the matter is urgent.
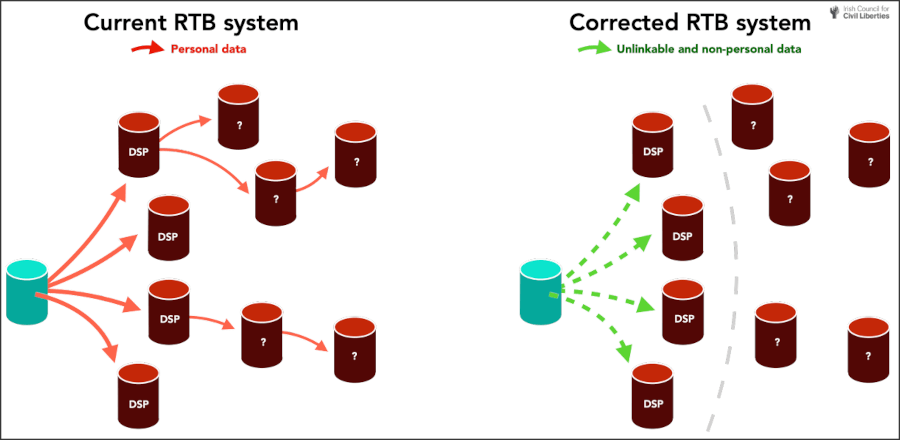
The perforated system of digital advertising, its potential for abuse against billions of internet users, and the cases of actual exploitation are largely ignored and often go unnoticed. Existing data protection laws are ineffective against these hidden data collection and distribution mechanisms, leaving users unprotected and powerless to prevent becoming targets.
VPN tools can help mitigate RTB-assisted profiling and persistent tracking by masking the user’s real IP address, which constitutes a critical piece of information for surveillance tools. Also, by encrypting all internet traffic, VPNs make analysis by third-parties difficult, so browsing behavior and personal information are effectively hidden, thwarting data inter-correlations and profiling. Finally, many VPNs actively block trackers (see VPN ad blockers) and minimize browser fingerprinting, so each browsing session appears unique, making it challenging to connect the dots.







I use offshore vpns that block at least most trackers and adds
Use extreme caution in letting out my real name, real birthdate, etc. to websites and even “you know who” operating systems.
I don’t have social media accounts, I scratch my head over people who put their whole lives online, including embarrasing spats and none of my business info, as well as on the phone.
Location is turned off, as well as wifi, gps, etc.
I use virtual “burner” email addresses, a different one for every business or website I patronize.
Virtual phone numbers, I never give out my sim card phone number. The service I use is configurable to whitelist so I don’t whack -a-mole blacklist telemarketers or other irritants that waste my time.
I also use a service that has chatbots which waste telemarketer’s time for the very few that slide past my sim card number
The virtual numbers are divided into catagories: family and trusted friends, business and politicians, medical, financial institutions… etc
Maintain contact list on a voip service, not on device.
No one has my sim number on their contact list. I might have to copy and paste numbers to my virtual numbers, but it’s worth it
The third party contact list app on phone is empty
I don’t do anything critical on my phone like banking, email, etc. I use a dedicated laptop linux os for only those items. Brave browser.
Removed laptop sda drive, boot usb with several different linux os for different purposes – several security issues resolved. I never conduct online business on my phone, and avoid qr codes with a passion.
Only necessary apps on phone, replace as many os apps as possible, camera disabled and tape over lenses.
I don’t purchase telecom specific phones, only unlocked phones so I only have to deal with subverting the manufacturer installed crap. Cheaper phones, never flagships.
As little personal data on the phone as possible.
The email providers I use on laptop linux block tracking pixels and more.
I try to stay away from texting anything potentially controversial, because the telecoms keep texts forever and some datamine personal info for profit. No one I know is the slightest interested in secure communication such as signal.
To reset phone I do it in a place with no wifi signals and sim card out, then turn off all tracking, etc, then go through permissions on each and every installed app, disabling many of them and removing others. It’s a very long and tedious process.
There’s more…
It sounds paranoid, but I just want to be left alone and it’s like that’s too much to ask for… I miss that ugly, old rotary phone of my younger days. Everyone now expects you to be immediately available.
Check how personally identifiable your browser is
https://coveryourtracks.eff.org/
Even the FBI recommends ad blockers.
Scaring how they track everyone online. Thank you so much to Restoreprivacy because of you, we can fight back!
Hi,
Is AdGuard app can solve the same issues?
Hi AronS, I would rather use ublock origin