
After a period of dormancy, the Predator spyware has resurfaced with new infrastructure and improved tactics to bolster its anonymity and evade sanctions. The Insikt Group, a division of Recorded Future, uncovered this revival despite prior expectations that public exposure and U.S. sanctions had curbed its activity. Predator's comeback includes a sophisticated delivery system that masks the origin of its operations, enabling continued exploitation of high-profile targets across multiple countries.
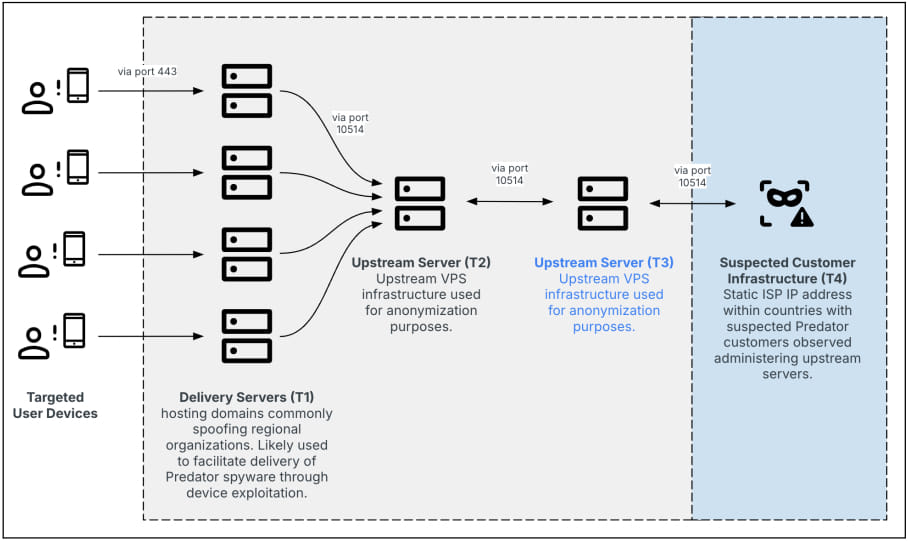
The new infrastructure, identified by Insikt Group in mid-2024, integrates an additional tier within its delivery network to obfuscate customer activity, making it harder to pinpoint its users' locations. This design change was likely implemented to counteract the growing scrutiny and sanctions on the spyware's operator, Intellexa, a cybersecurity firm responsible for Predator's development.
Despite the security improvements, the spyware retains its core functionality of targeting mobile devices through both “one-click” and “zero-click” attack vectors. These attacks can compromise Android and iPhone devices, providing attackers with unfettered access to microphones, cameras, and sensitive data without the user's awareness.
Predator's global reach
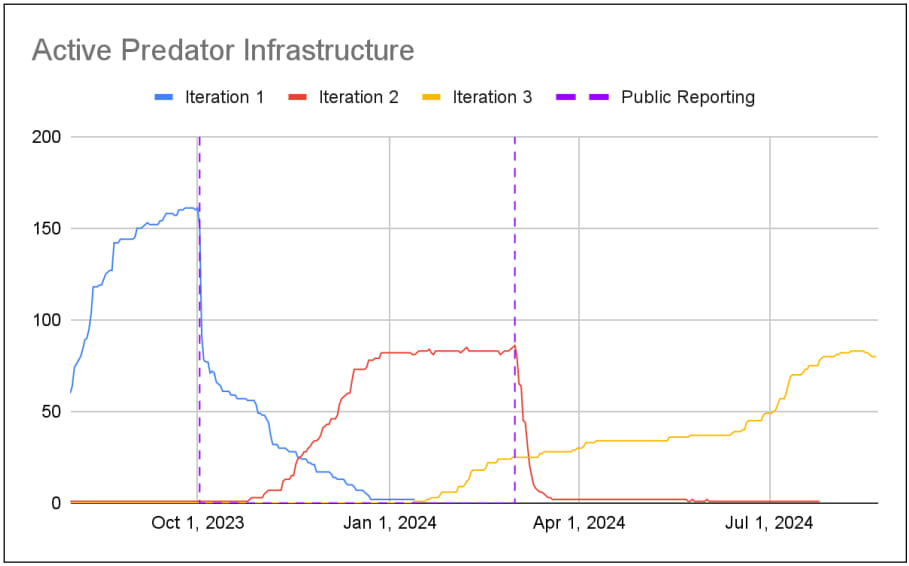
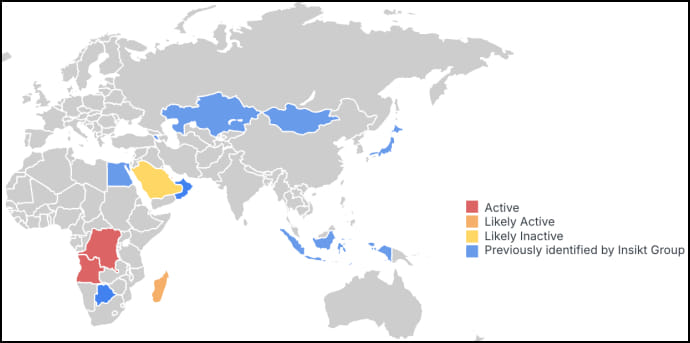
Insikt's findings highlight clusters of Predator activity across different nations, including one newly linked to the Democratic Republic of the Congo (DRC), where Predator domains have been linked to infrastructure in conflict-ridden regions. Other countries associated with this malicious infrastructure include Angola, possibly Madagascar, and the UAE. This latest iteration, dubbed “Iteration 3,” marks a stark evolution from earlier versions, which relied on fewer obfuscation measures.
Recorded Future
Predator has been around since 2019, originally developed by Cytrox and later commercialized by Intellexa. The spyware has garnered attention for its minimal traceability on infected devices, making forensic analysis challenging. Its resurgence indicates continued demand for its capabilities among governments and organizations targeting high-profile individuals such as political activists, corporate executives, and opposition figures. In fact, Insikt's report suggests that the spyware's use is reserved for high-stakes intelligence operations due to its costly licensing model.
Recorded Future
Despite Predator's sophistication, the commercial spyware operation has faced setbacks in recent years. Major reports on its infrastructure in 2023 and early 2024, followed by U.S. government sanctions, led to a temporary decline in activity. Yet, Intellexa has been able to adapt, updating its architecture and operations to maintain functionality. For instance, the new tiered delivery system helps prevent attribution by funneling traffic through virtual private servers and obfuscated domains, making it significantly more challenging for researchers to track.
Recorded Future
Mitigating the threat
To protect against Predator and similar spyware, organizations and individuals in vulnerable regions should adopt robust cybersecurity practices. Insikt Group recommends regularly updating mobile devices, using secure device management systems, and enabling features like Apple's “Lockdown Mode” to block some attack vectors. Rebooting devices periodically, while not foolproof, can help deactivate or remove some spyware components that can't survive reboots or rely on manual activation in the post-infection stage.
Predator's return signals that the global market for mercenary spyware remains strong, driven by demand from state and non-state actors seeking advanced surveillance tools. Despite increased awareness and efforts to dismantle such operations, the fight against these sophisticated digital threats is far from over.







Leave a Reply