
Researchers from the Citizen Lab have presented a paper expanding the threat model of a 2021 attack impacting popular VPN software dubbed “Port Shadow.”
Presented by Benjamin Mixon-Baca at the Privacy Enhancing Technologies Symposium (PETS) 2024 in Bristol, UK, the paper details how the “Port Shadow” attack, and the underlying vulnerability which is tracked as CVE-2021-3773, still affects major VPN protocols such as OpenVPN, WireGuard, and OpenConnect on Linux and FreeBSD systems.
The Port Shadow attack
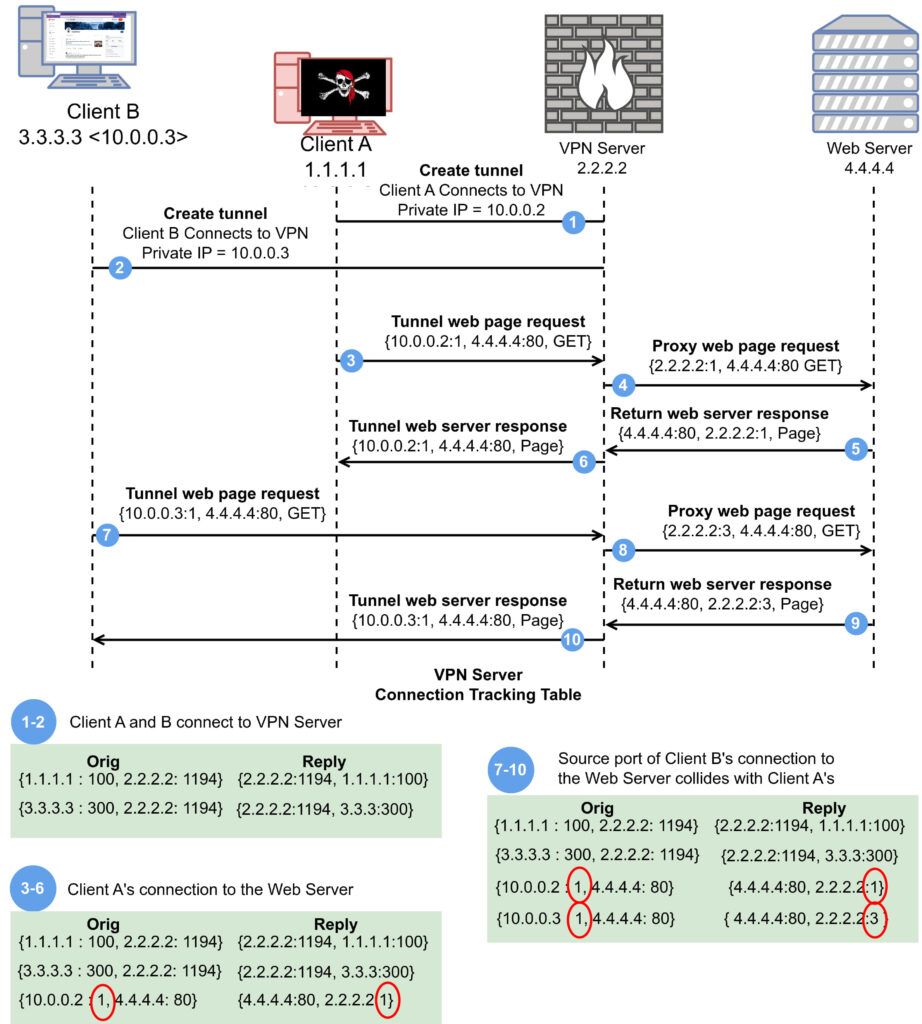
The port shadow attack, first documented roughly three years ago, concerns an exploit that significantly extends the reach and capabilities of attackers targeting VPN users. At its core, this attack manipulates the shared resources on a VPN server, specifically, the ports used by the connection tracking framework.
The mechanism of the attack compromises specific components as listed below:
- Shared resource exploitation: In a typical VPN setup, multiple users connect to the same VPN server, and each connection is assigned a unique port. These ports are part of the connection tracking framework, which manages how data packets are routed between the users' devices and the internet.
- Crafting malicious packets: An attacker, who is also connected to the same VPN server, can craft malicious data packets. These packets are designed to exploit the connection tracking framework by mimicking legitimate traffic and manipulating the shared port assignments.
- Hijacking connections: By carefully injecting these crafted packets, the attacker can redirect traffic intended for another user to themselves. This effectively makes the attacker an in-path router, intercepting and potentially altering the data being transmitted between the victim and the VPN server.
- Deanonymizing and interfering: Once in this position, the attacker can deanonymize the victim's connection, perform port scans, inject malicious DNS responses, or even redirect the victim to malicious websites. The attack is not limited by the attacker's physical location but rather by their ability to connect to the same VPN server as the victim.
Citizen Lab
“We found that Linux/Netfilter + (OpenVPN and WireGuard), which a large fraction of VPN services use, has the highest susceptibility to these attacks regardless of client platform (PC, Android, and iOS).”
Citizen Lab
Risk mitigation
The researchers demonstrated that VPN servers using OpenVPN or WireGuard today can still be exploited through the port shadow attack, allowing attackers to hijack connections, inject malicious packets, or perform denial-of-service attacks.
Neither OpenVPN nor WireGuard have addressed the risks that arise from CVE-2021-3773 because the flaw isn't part of their software stacks. The Linux kernel team did attempt to fix the issue in December 2021, but the fixing commit was reverted due to backwards compatibility issues in March 2022, and the flaw remains unaddressed since them. Citizen Lab says CVE-2021-3773 is still exploitable in the most recent Linux kernel version.
To mitigate the risk, VPN vendors should randomize source port selection to reduce predictability in port assignment, implement specific firewall rules that block unauthorized port usage, and limit concurrent connections to lower numbers.
For end users, since the discovered flaws that make the port shadow attack possible lie on the server and not the client app, there's only a little they can do to reduce the risk. The researchers recommend connecting to private VPN servers or using non-vulnerable protocols like Shadowsocks or Tor. Ultimately, it's up to the users to do due diligence to ensure their software is safe against CVE-2021-3773.
VPN services like NordVPN, ExpressVPN, and Surfshark typically utilize the mentioned protocols, but CitizenLabs notes that they are not vulnerable to CVE-2021-3773. It is unclear what the status is with other VPN vendors, so users are recommended to ask their providers directly about implemented fixes and mitigations.






I was using NordVPN for some time.
Suddenly my internet connection was completely cut, except via Tor network and I wasn’t able to restore it, except by erasing the disk and reinstalling Linux.
On some forum someone told me that NordVPN could be to blame.
I stopped using VPNs since then. It seemed they were dangerous and this article confirms it.
If problem can be solved with kernel only, then why are you lying about VPN who aren’t affected.
What lies, I only see updated news that the treat is still actice for Popular VPN Products on Linux. And Alex, who only quoted CitizenLabs results. That notes a few vpns by name as to – that they are not vulnerable to CVE-2021-3773.
Citizen Lab says CVE-2021-3773 is still exploitable in the most recent Linux kernel version.
“We found that Linux/Netfilter + (OpenVPN and WireGuard), which a large fraction of VPN services use, has the highest susceptibility to these attacks regardless of client platform (PC, Android, and iOS).”
Citizen Lab
The Linux kernel team did attempt to fix the issue in December 2021, but the fixing commit was reverted due to backwards compatibility issues in March 2022, and the flaw remains unaddressed since then.
No one is willing to fix, so the issue as well of a vpn threat is a current crisis!
Looks like it’s time to clean up the CommenTard list, Alex….
Sven Sir do you recommend 3rd party Anti-viruses for Windows, Android and Mac OS? Or built-in protection is sufficient? Is there a benefit in subscribing and paying for yearly subscriptions to the likes of Bitdefender and Sophos to secure one’s devices and digital life or one need not pay for an Antivirus these days and should use the default Windows Defender, Google Play Protect etc. built into the modern Operating Systems? Is paying for an Antivirus a waste of money as being said by many people and experts alike?
But sometime back Linus Tech Tips and NFC God got hacked and they were probably using the default Windows Defender? Similarly people get infected on Mac OS by info-stealers and also fall victim to various phishing etc. scams on their mobile devices? And it is not always possible in all scenarios to stay protected just by being vigilant and cautious (like recieving a malicious link in email etc. by a relative who has been hacked) and so may be one needs an Antivirus as the last line of defence against online threats? What are your views?
I have not spent time researching AV solutions but I think it’s a good idea.
How many carrots on your finger dear? Sorry, Im baddddddd.
Stop, stop, stop following advice and blaze your own path to facts and gain underdtandings in the questions you’ve asked.
Why protect…initial path av test results…
[https://www.technorms.com/78228/antivirus-testing-labs]
[https://www.av-test.org/en/]
[https://www.av-comparatives.org/test-results/]
[https://selabs.uk/reports/]
[https://www.virusbulletin.com/testing/vb100/]
Second path, how you going to rebound if, your system has been hacked and demands payment to restore it?
Ransomware attacks are often designed to spread quickly, so it’s crucial to act swiftly to minimize damages.
If you haven’t already, create a backup of your essential files and data to an external drive or cloud storage service. This will help you recover your data if you need to wipe and reinstall your operating system.
Regularly update your operating system, antivirus software, and security tools to maintain a strong defense against future threats.
Third path, Deny by default firewalls, also known as default deny policies, are a security best practice that denies all incoming and outgoing traffic unless explicitly permitted. This approach provides a robust defense against unauthorized access and malicious attacks. Thus, reduces attack surface; by default denying all traffic, you minimize the number of potential entry points for attackers.
These help any ?
= )
That’s not advice but experience Bunny.
You see, that forming a question puts your thoughts into an order. An order of logic, that given to the reversed/expaneded views, leads to finding the correct answers as sought. With your common sense or that gut feeling, so trust in your instincts that your brain’s logic gives to you.
AV softwares; Some are extensively collecting data about your computer usage to improve their products. While simple product usage telemetry is usually anonymized, some products may also upload suspicious files from your computer to the vendor’s scanning cloud. You need to be able to fully trust that the vendor will handle your files responsibly, ethically and securely. After all, a private document could be part of such an upload, too…
Modern Apps are way more powerful and feature rich, seemingly, as your users trust is being traded for CONVENIENCE anymore. This has a consequence for users having blindly trusted any software or service from a PAST history in their use of it.
Not knowing the emerging trend of having to “Verify before Trust” must be the users digital golden rule going foreward. Expessed by a phrase, witnessed in the current trend of compaines choosing Business Over Security practices for moral judgments relating to their customers data today.
“However, we do not have a comprehensive list of VPN services that are not vulnerable.”
Does anyone know if Mullvad is susceptible to this?
A growing trend?
Business Over Security “a business decision, not a technical one.”
Your call but note,
*VPN servers using OpenVPN or WireGuard today can still be exploited – the discovered flaws that make the port shadow attack possible lie on the server and not the client app – OpenVPN nor WireGuard have addressed the risks that arise from CVE-2021-3773 because the flaw isn’t part of their software stacks – The Linux kernel team did attempt to fix the issue in December 2021 – so users are recommended to ask their VPN providers directly about implemented fixes and mitigations. Help any?
Not the first for a server exploit to lay unanswered making users vulnerable.
Like this one-
[https://www.propublica.org/article/microsoft-solarwinds-golden-saml-data-breach-russian-hackers]
Customers were told the cloud was the safest place to put their most precious data. The product, which was used by millions of people to log on to their work computers, contained a flaw that could allow attackers to masquerade as legitimate employees.
SolarWinds proved that, for the millions of users whose systems included AD FS, their cloud was only as secure as their on-premises servers.
Wow bad VPN news for sure and unaddressed still today. Alex, I’m trying to understand as the study tells.
“In this study, the authors explore the connection tracking frameworks used in major operating systems”.
Does that refer to a server’s operating OS, specifically the Linux and FreeBSD systems, as you mention? What about major OSs in Apples, Windows, and Linux Androids through the addon VPN client users have installed to those commerical OSs? Any VPN usage will still cause commerical OSs to be vulnerable, if an attacker, acts as an in-path router between these users VPN clients and its VPN server.
As the port shadow vulnerability, that can extend the range of attackers to targets in countries outside their normal administrative boundaries and launch machine-in-the-middle attacks.
Seems to me that ^ above is fairly right with the below. So the VPN and Servers makes a users commerical OS vulnerable through the port shadow exploit.
“The connection tracking framework is the engine that drives the identity obfuscation and facilitates the VPN client application’s ability to forward a user’s transmissions to the VPN server. It also facilitates the VPN server’s ability to transmit users’ requests to the website and trick the website into thinking the VPN server sent the transmission instead of you, and transmit the website’s responses back to you.”
“We disclosed this vulnerability to the VPN software developers, Linux, and FreeBSD, but, because of the way the vulnerability works, the mitigation strategy is limited to using specific firewalls rules as opposed to a code fix.” WOW!
Thanks for sharing.