
A recent investigation by Censys has revealed that the Polyfill.io supply chain attack has impacted 384,773 hosts, a significant increase from the initially reported 100,000. This attack, which began in February 2024, highlights the widespread and severe nature of the compromise.
Initial findings
On June 25, 2024, the Sansec Forensics team first uncovered an attack targeting the Polyfill.io JavaScript library. The attack was traced back to February 2024, when Funnull, a Chinese CDN company, acquired the Polyfill.io domain and GitHub account. Shortly after the acquisition, the domain began redirecting users to malicious sites and deploying malware designed to evade detection.
Ongoing threat
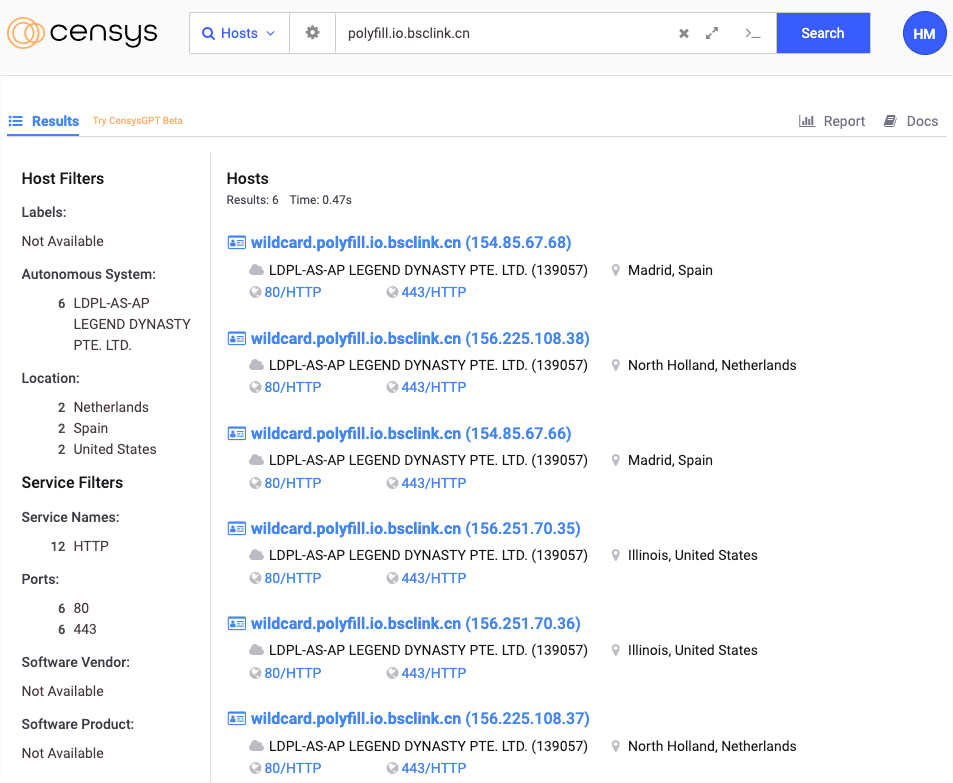
By June 27, 2024, Namecheap had suspended the malicious polyfill.io domain to mitigate the immediate threat. Despite this action, Censys detected 384,773 hosts still embedding the compromised Polyfill JS script as of early July, with a significant concentration of these hosts located in Germany.
Polyfill.io, crucial for enabling modern web functionalities on older browsers, saw its widespread use become a vulnerability. Major platforms, including Hulu, Mercedes-Benz, and Warner Bros, are among the high-profile entities that remain affected.
Further technical analysis by Censys has shown that around 237,700 of the affected hosts are located within the Hetzner network (AS24940), a popular web hosting service primarily based in Germany. The most common hostname associated with these compromised hosts is ns-static-assets.s3.amazonaws.com, indicating extensive usage among Amazon’s S3 static website hosting users.
Censys
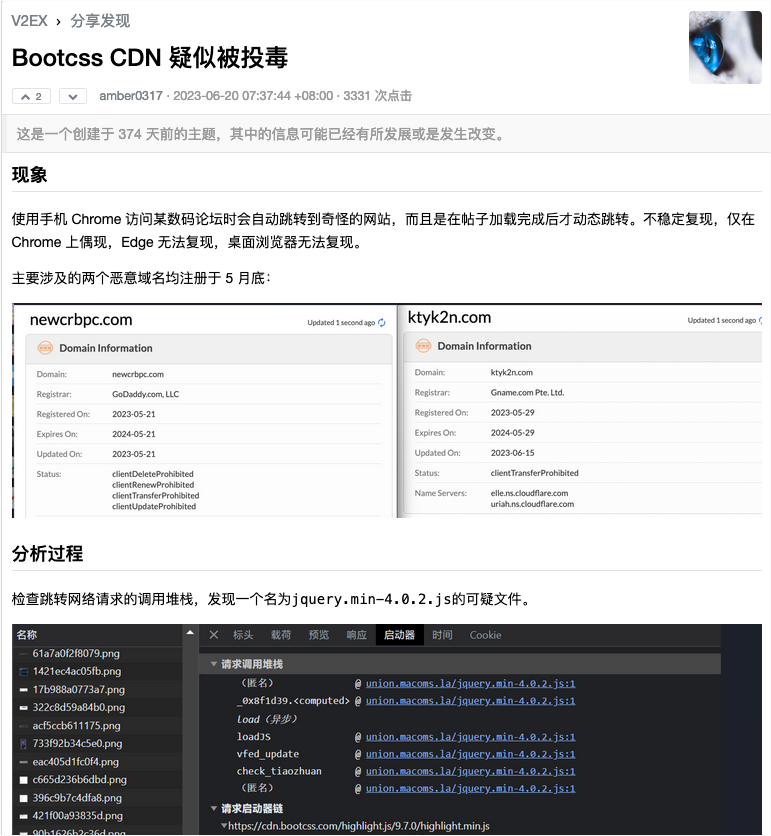
Additionally, the investigation uncovered a broader network of potentially compromised domains linked to the same account that owned polyfill.io, with 1,637,160 hosts referencing these additional domains. One domain, bootcss.com, had been engaging in similar malicious activities since June 2023.
The malicious JavaScript code found in these older attacks includes a function named check_tiaozhuan(), which checks if the user is on a mobile device and then redirects them based on specific conditions. This tactic mirrors the evasion techniques used in the polyfill.io attack, making detection and mitigation particularly challenging.
Censys
Mitigating the attack
The response from the tech community has been robust. Cloudflare and Fastly offered alternative secure endpoints for Polyfill services. Google blocked ads for e-commerce sites using Polyfill.io, and the website blocker uBlock Origin added the domain to its filter list. Andrew Betts, the original creator of Polyfill.io, recommended discontinuing its use, noting that modern browsers no longer require such libraries.
Security experts advise website owners to immediately remove references to polyfill.io and its associated domains from their codebase. They should adopt secure endpoints from Cloudflare and Fastly, regularly monitor software supply chains for vulnerabilities, and use tools like Content Security Policy (CSP) monitoring and backend scanners to detect compromised libraries.







Leave a Reply