
A new Ransomware-as-a-Service (RaaS) operation named ‘Global Group' has surfaced on underground forums, positioning itself as a rebranded successor to the Black Lock and Mamona ransomware campaigns.
According to an in-depth analysis by EclecticIQ, the threat actor behind this group, who uses the moniker “$$$,” has launched an advanced extortion platform with artificial intelligence–powered ransom negotiations, mobile-accessible affiliate panels, and broad targeting capabilities across healthcare, industrial, and legal sectors.
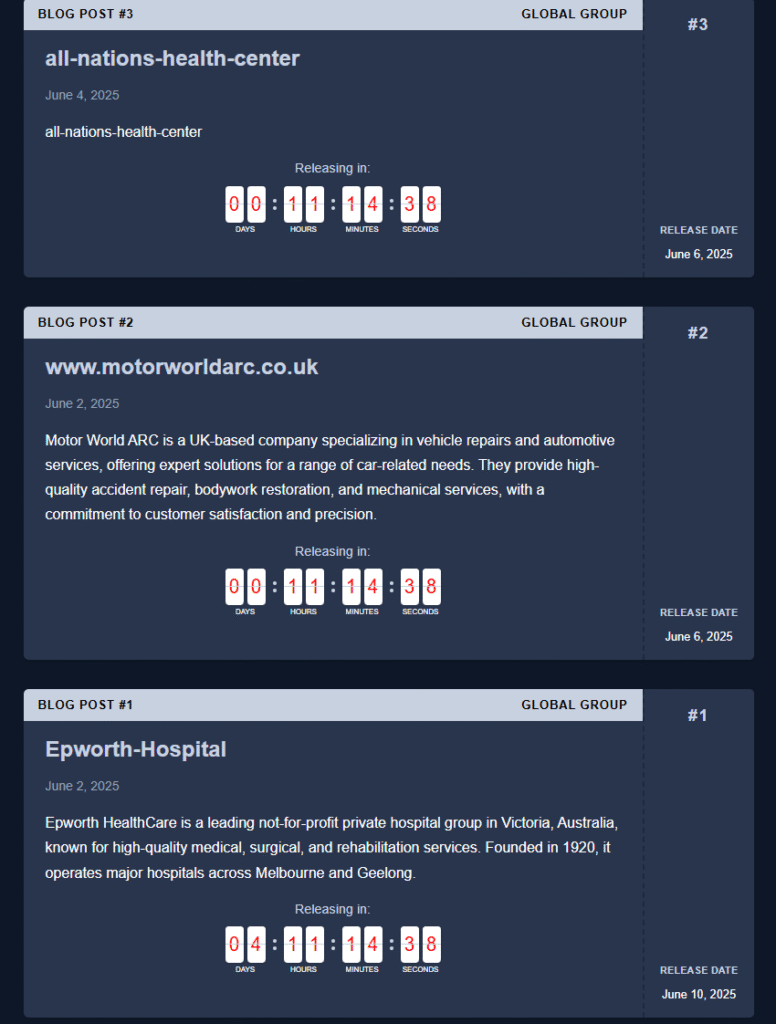
EclecticIQ analysts first observed the ‘Global Group' brand being promoted on June 2, 2025, via a post by “$$$” on the Ramp4u cybercrime forum. Though the actor initially described the project as pre-operational, the group quickly transitioned to live operations, claiming nine victims in its first five days. By July 14, ‘Global Group' had listed 17 victims spanning healthcare providers in the U.S. and Australia, industrial firms in the U.K., and service firms in Brazil. Analysts believe the group is an evolution or rebranding of the Black Lock RaaS, which suffered reputation damage after being exposed earlier this year.
EclecticIQ
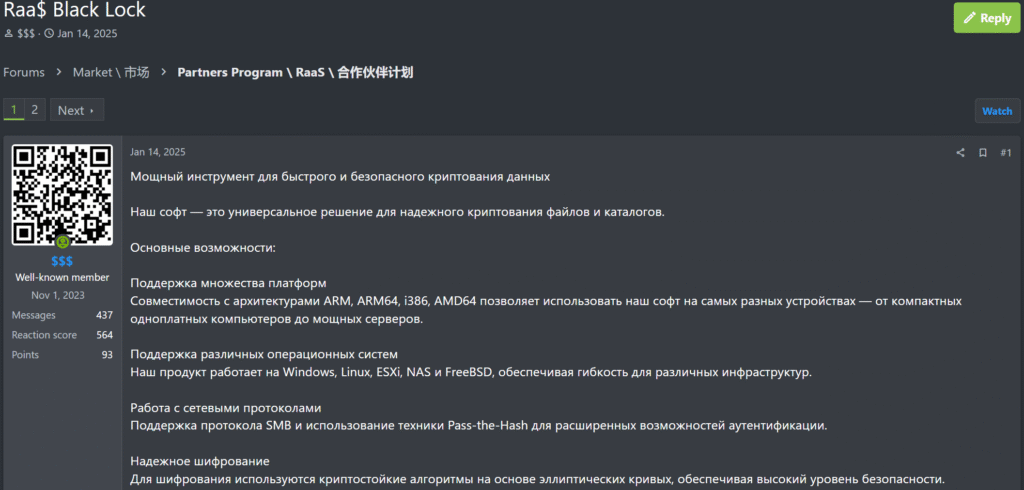
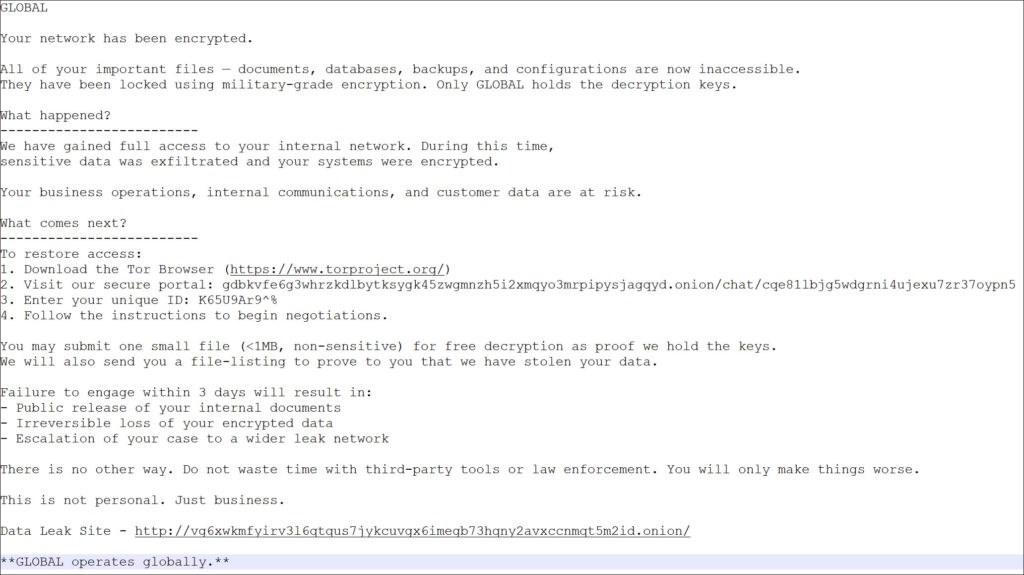
The Global Group leak site, hosted on the Tor network but inadvertently leaking its real-world IP address, has been linked to the same Russian VPS provider previously used by Mamona operations. Technical analysis revealed that the group reused infrastructure and malware code, including a shared mutex key (Global\Fxo16jmdgujs437), indicating continuity in the threat actor's identity. The ransomware payload is compiled in Golang and leverages ChaCha20-Poly1305 encryption, offering cross-platform functionality for Windows, Linux, macOS, and ESXi environments. One variant uploaded to VirusTotal on June 7 showed rapid encryption capabilities through Go's multithreaded architecture.
EclecticIQ
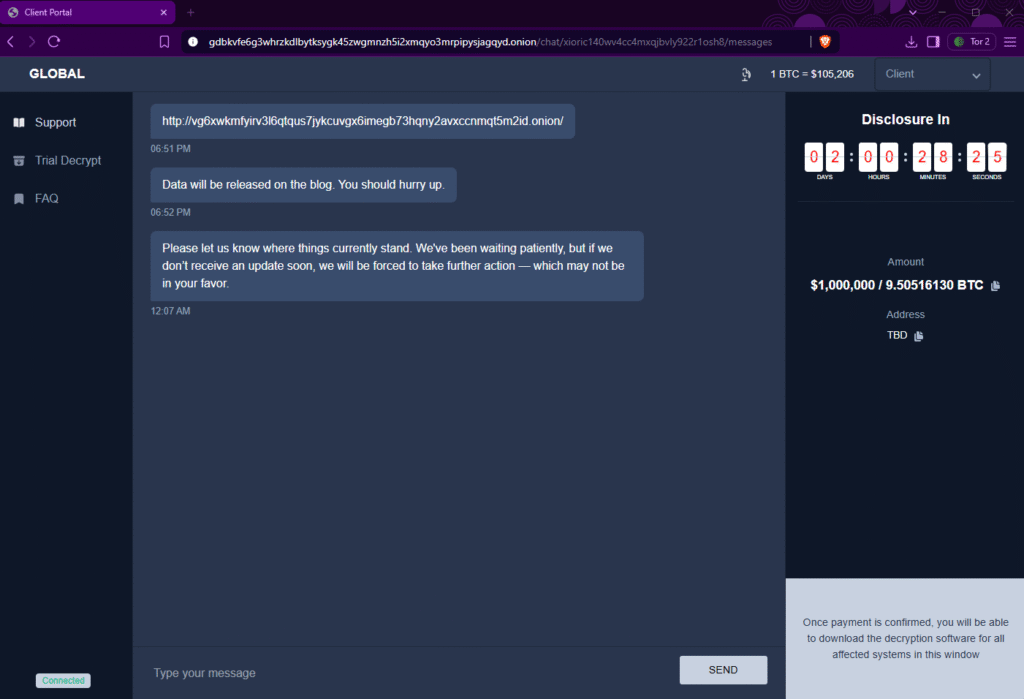
Global Group operates under a RaaS business model, offering affiliates 85% of ransom proceeds, a higher-than-average share designed to attract skilled collaborators. The affiliate portal supports real-time victim tracking, customizable payload creation, and remote operations via mobile devices. The platform also includes AI-powered ransom negotiation bots, enabling non-English-speaking affiliates to effectively engage with victims and apply psychological pressure to secure seven-figure demands.
EclecticIQ
The group's operations depend heavily on Initial Access Brokers (IABs) to infiltrate enterprise networks. Analysts observed “$$$” communicating with an IAB known as “HuanEbashes,” who offered RDP access to a U.S. law firm in February 2025 and later promoted a VPN brute-forcing tool tailored for Fortinet, Palo Alto GlobalProtect, Cisco VPN, RDWeb, and Outlook Web Access. These tools enable Global Group affiliates to bypass endpoint defenses by acquiring valid credentials and exploiting perimeter devices, often leading to full domain compromise and ransomware detonation.
EclecticIQ
Global Group's emergence and adoption of AI-driven operations reflect a new reality where ransomware is no longer a single tool, but a service-oriented ecosystem with high agility, scalability, and increasing automation.







Leave a Reply