
A new study uncovering flaws in fingerprint authentication from Huazhong University of Science and Technology and collaborating institutions proposes a novel side-channel attack method called PrintListener.
The attack leverages the sound made by fingertips swiping across a screen to extract fingerprint features and construct more effective MasterPrints for fingerprint authentication systems.
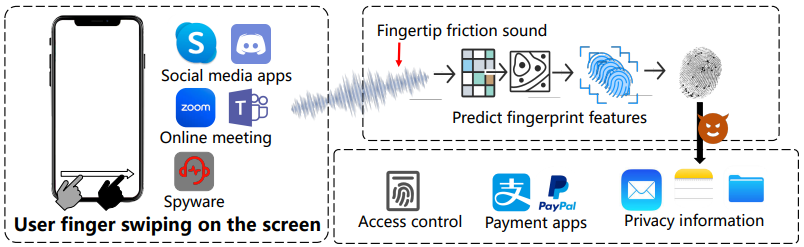
Researchers demonstrated that by recording fingertip friction sounds, something easily done via software that offers sound sampling rates above 16 kHz, like Microsoft Teams, Google Meet, FaceTime, Skype, and Wecom, attackers can significantly enhance the efficacy of fingerprint dictionary attacks.
Their findings highlight a significant potential risk in the security of biometric systems that rely on fingerprint recognition.
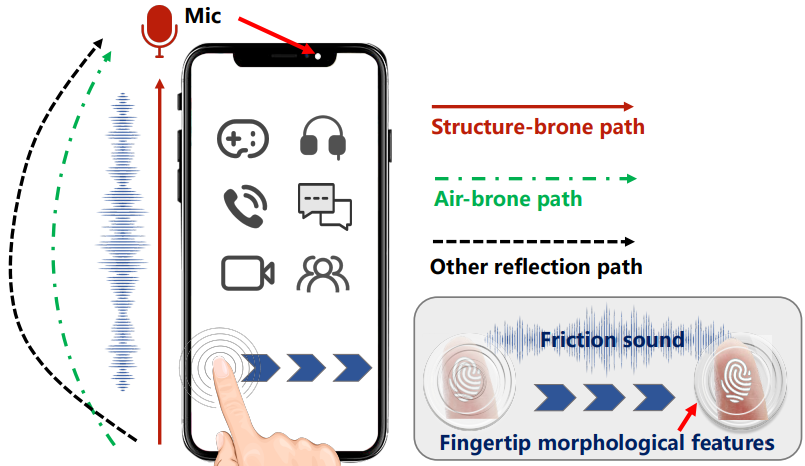
The team, led by Man Zhou of Huazhong University's School of Cyber Science and Engineering, developed PrintListener to analyze and utilize sounds generated during common user interactions with touchscreens, such as during phone calls or gaming sessions on mobile devices.
The method employs advanced algorithms to isolate these subtle friction sounds from background noise, extract fingerprint pattern data, and synthesize these into MasterPrints capable of deceiving fingerprint identification systems.
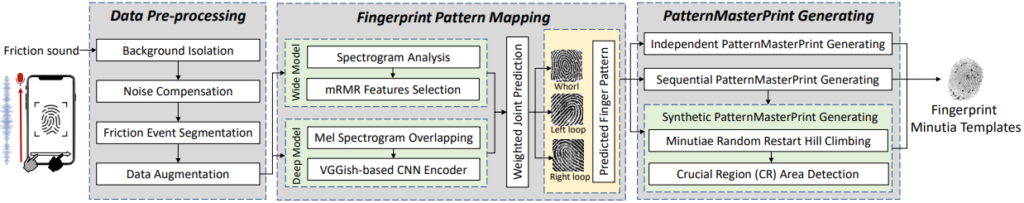
PrintListener exploits a vulnerability inherent in the widespread use of fingerprint sensors in mobile and security devices worldwide. It demonstrates a significant improvement in attack success rates compared to previous methods, achieving unauthorized access in a notable percentage of attempts under realistic conditions.
“Extensive experimental results in real-world scenarios demonstrate that Printlistener can attack up to 26.5% of partial fingerprints and 9.3% of complete fingerprints within five attempts at the highest security FAR setting of 0.01%” – PrintListener paper.
For protection against such attacks, the researchers suggest several mitigation strategies. These include modifying user behavior to reduce or alter finger swiping on sensitive devices during potential recording scenarios and technical adjustments in devices to limit the fidelity of recording fingertip friction sounds.
Moreover, the researchers note that different screen protectors affect the finger's sliding friction and the resulting sound characteristics, impacting PrintListener's accuracy in classifying the sound profiles. In general, the team's experiments showed that matte films are more susceptible to the attack when compared to glossy finishes.
As biometric authentication becomes increasingly common, ensuring the security of these systems is crucial to safeguarding personal and professional data against emerging attack methodologies like PrintListener.







Leave a Reply