
A newly identified variant of the notorious Octo (ExobotCompact) malware, named “Octo2,” now targets users across Europe, posing significant risks to mobile banking security. Researchers at ThreatFabric revealed that the malware developers have enhanced their tactics, using sophisticated methods to remain undetected and boost their success in hijacking mobile devices. In a concerning twist, the latest campaigns leverage trusted brands like NordVPN to lure unsuspecting users into downloading the malicious software.
Octo2 emerges
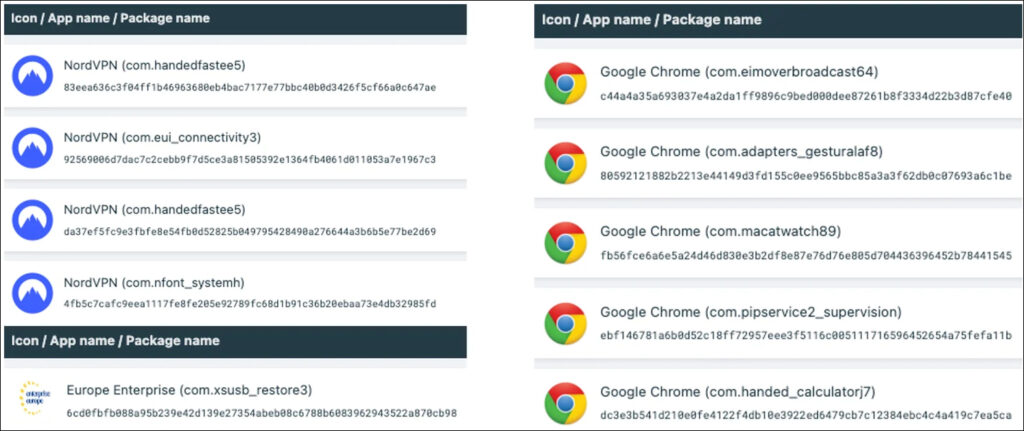
ThreatFabric first detected Octo2 malware masquerading as legitimate apps, including Google Chrome, Enterprise Europe Network, and NordVPN. The initial samples were found in Italy, Poland, Moldova, and Hungary. The malicious NordVPN impersonation highlights the increasing deception of these attacks, as users are more likely to trust and install apps that resemble well-known services.
Once installed, Octo2 uses advanced obfuscation techniques and remote access tools (RAT) to covertly take over devices, allowing attackers to control banking apps, intercept sensitive notifications, and execute on-device fraud without the victim's knowledge.
Octo2 specifically targets push notifications from banking apps and financial services, using a “block_push_apps” setting that ensures notifications are intercepted and hidden from the victim. This allows attackers to execute fraud while preventing users from noticing unauthorized activities on their accounts.
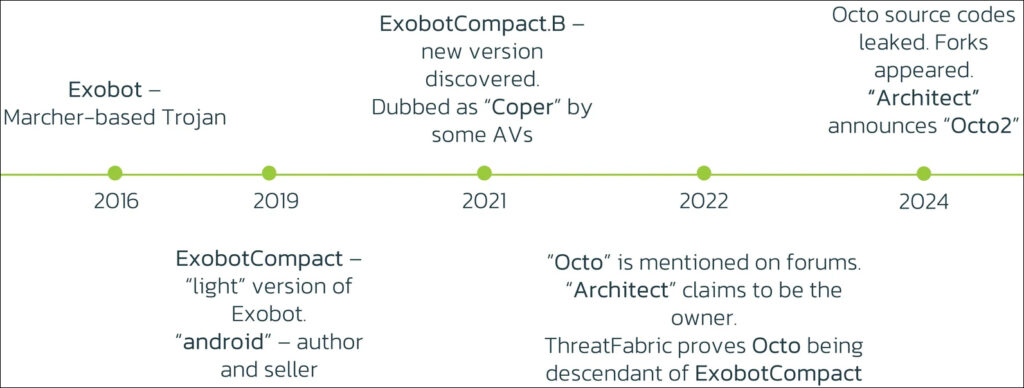
Octo malware evolution
Octo2 is the latest variant of the ExobotCompact family, which originated in 2016 as a banking trojan. After years of refinement, the malware became known as “Octo” in 2022, followed by a source code leak that enabled numerous threat actors to adopt and modify the malware. The release of Octo2 is a direct response to this leak, with the original developer updating the malware to enhance its capabilities and stay ahead of competitors using the earlier versions.
ThreatFabric
ThreatFabric notes that Octo2's developers have focused on increasing the stability of device takeover attacks, refining the malware's RAT functionality, and implementing anti-analysis techniques to prevent detection.
Specifically, the latest version implements the following:
- Enhanced RAT stability: By optimizing the quality of remote sessions, the malware can maintain control over devices, even on unstable networks. The “SHIT_QUALITY” setting, as crudely labeled by its developers, reduces the resolution of screen captures, enabling smoother operation in low-bandwidth environments.
- Obfuscation techniques: The malware's obfuscation processes have become more complex, making it harder for antivirus solutions to detect. Octo2 dynamically loads additional libraries to decrypt its payload, further complicating manual and automated analysis.
- Domain Generation Algorithm (DGA): Octo2 uses DGA to generate new domain names for communication with C2 servers. This approach makes it easier for the malware to switch servers when existing ones are taken down by law enforcement or cybersecurity teams.
NordVPN impersonation
The impersonation of NordVPN, one of the most trusted virtual private network (VPN) services globally, is particularly alarming. By mimicking NordVPN's branding and functionality, Octo2 effectively bypasses users' usual security suspicions. The app would appear to be legitimate, and once installed, the malware works quietly in the background, intercepting sensitive data and enabling the attackers to conduct fraudulent activities on mobile banking apps.
ThreatFabric
Though ThreatFabric does not delve into how victims are tricked into downloading those fake apps in the first place, common methods include malvertising, social media posts, and direct messages. Users should always ignore all these software distribution channels and head straight to the project's official webpage when looking to download software installers. For Android devices, that would be the Google Play store.
The appearance of Octo2 poses a major risk to mobile banking security across Europe. Given its sophisticated features and the impersonation of trusted services like NordVPN, it is highly likely that the malware will continue to spread, potentially expanding to new regions. ThreatFabric predicts that users in other parts of the world, including the United States and the Middle East, could soon be targeted.







Leave a Reply