
Cisco Talos researchers have identified a threat actor delivering a new variant of MedusaLocker ransomware known as “BabyLockerKZ.”
This financially motivated group, active since at least late 2022, initially targeted organizations across Europe, shifting their focus to South America by mid-2023. The new variant exhibits some unique features, setting it apart from other known strains of MedusaLocker, indicating a distinct evolutionary path.
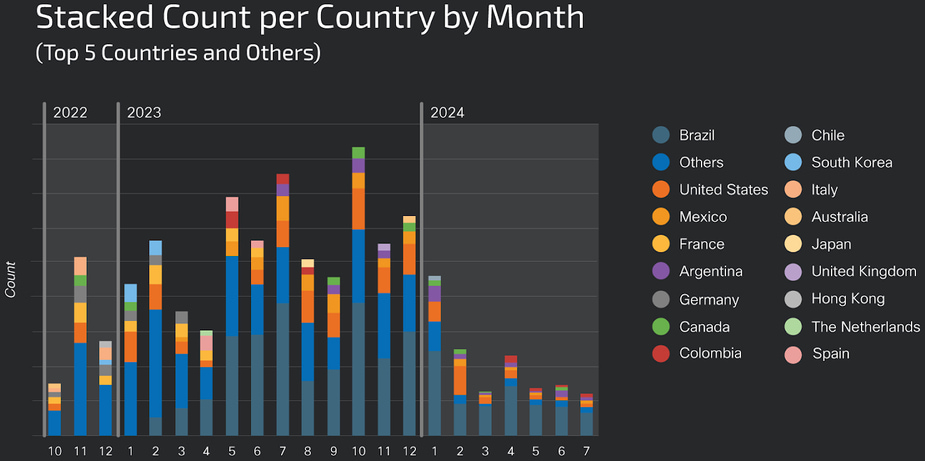
Measuring 200 breaches per month
The ransomware, BabyLockerKZ, is identified by a PDB path that contains the term “paid_memes,” a string also found in other tools used by the threat actor. Since late 2022, the attacker has primarily targeted organizations globally, with a significant uptick in European victims until early 2023, followed by a shift to South American countries such as Brazil, Mexico, Argentina, and Colombia. The attack volume doubled during this transition, with around 200 unique IPs compromised per month until the attacks decreased in early 2024.
Cisco Talos
The pattern of attacks suggests that the threat actor operates as either an Initial Access Broker (IAB) or a ransomware affiliate, employing sophisticated tactics, techniques, and procedures (TTPs) to achieve their financially motivated goals. BabyLockerKZ not only encrypts files but also sets unique autorun keys and uses multiple public and private keys stored in the Windows registry to secure its operation.
The BabyLockerKZ ransomware is a distinct variant of MedusaLocker and has some differentiating elements:
- The absence of mutex {8761ABBD-7F85-42EE-B272-A76179687C63}, which is seen in other MedusaLocker variants.
- The absence of the “MDSLK” registry key.
- Use of a unique set of registry keys labeled “PAIDMEMES,” both public and private.
The attackers use a range of publicly known and custom-built tools to facilitate their lateral movement and credential theft, leveraging “living-off-the-land” binaries (LoLBins) and other tools tailored by the same developer. The malware components are often stored in directories like Music, Pictures, or Documents on the compromised systems.
The toolset includes several utilities, such as:
- HRSword: Disables antivirus (AV) and endpoint detection and response (EDR) solutions.
- Advanced Port Scanner & Netscan: Tools for mapping internal networks and devices.
- ProcessHacker & PCHunter: For process monitoring and manipulation.
- Mimikatz: Extracts Windows credentials from memory.
One key tool used by this actor is called “Checker,” which contains the “paid_memes” string in its PDB path and bundles other publicly available applications like Remote Desktop Plus, PSEXEC, and Mimikatz. “Checker” comes with a GUI for managing credentials and allows lateral movement using multiple protocols, including SMB and WMI. It also facilitates “pass-the-hash” attacks, making it a pivotal component in the deployment of BabyLockerKZ.
Cisco Talos
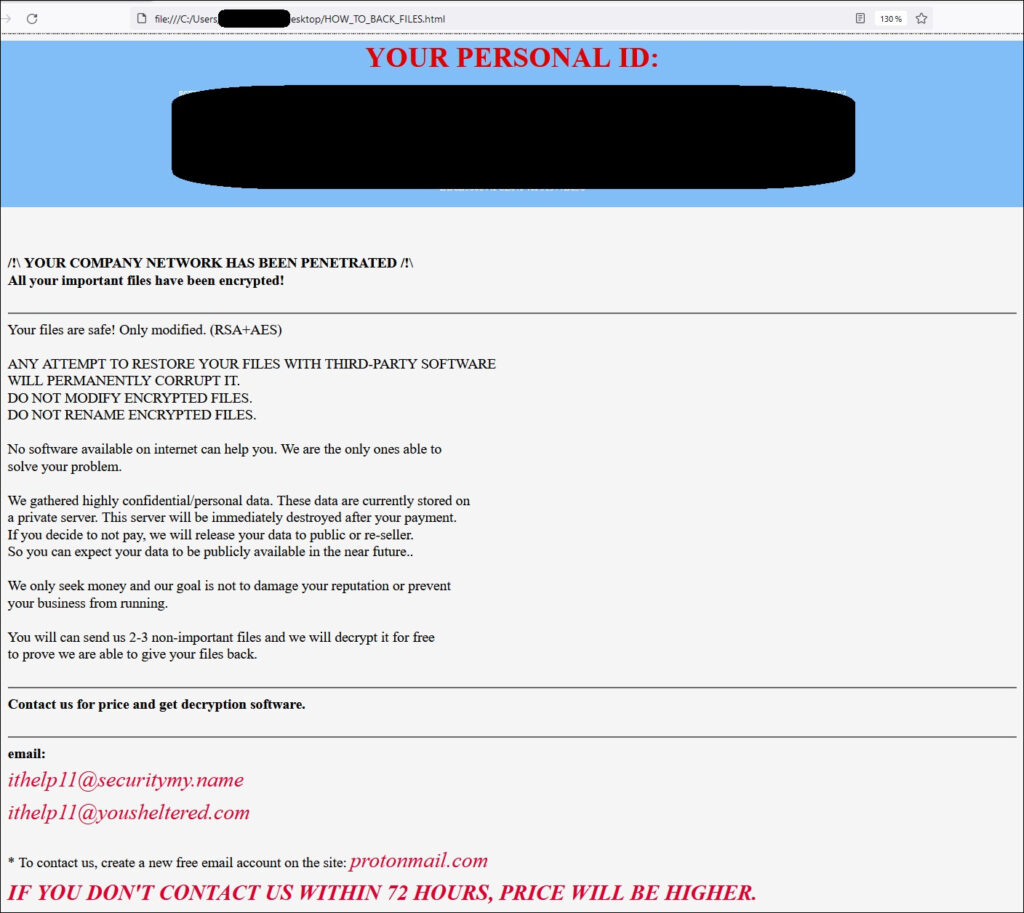
For the complete list of indicators of compromise and proposed mitigations, check the Cisco Talos report. A common sign of infection by BabyLockerKZ is the presence of registry keys with the “PAIDMEMES” identifier, like:
HKEY_USERS\%SID%\SOFTWARE\PAIDMEMES\PRIVATE
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\BabyLockerKZThe emergence of BabyLockerKZ demonstrates the continuous evolution of ransomware tactics and highlights the necessity for robust detection, response mechanisms, and security controls that address both known/documented and unknown threats.







Leave a Reply