
A coordinated international operation has led to the indictment, arrest, and sanctioning of several key actors affiliated with the LockBit ransomware group, marking a significant blow to the notorious cybercrime organization. These actions are part of an ongoing effort named “Operation Cronos,” involving law enforcement agencies across the United States, United Kingdom, Australia, Spain, and France.
The latest developments, announced on the seized LockBit websites on the dark web, were mostly the result of UK's National Crime Agency (NCA) compromise of LockBit's platform in February 2024, from where it retrieved troves of data helping in the identification of high-profile affiliates of the notorious ransomware program.
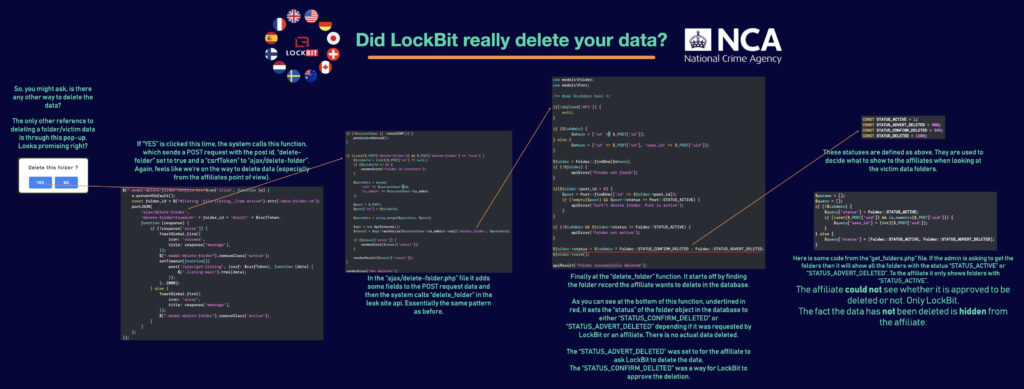
CyberInsider
Identification of ‘Beverley'
Aleksandr Ryzhenkov, a member of the Russian-based Evil Corp, has been unmasked as the LockBit affiliate known as “Beverley.” The U.S. Department of Justice has indicted Ryzhenkov for his involvement in the BitPaymer ransomware operations. He has been accused of creating over 60 LockBit ransomware builds and attempting to extort at least $100 million from victims through ransom demands. Ryzhenkov is also known by the alias “mx1r” and has ties to UNC2165, an extension of Evil Corp's network.
Ryzhenkov has been sanctioned by the U.S., U.K., and Australia for his role in facilitating cybercrimes through Evil Corp and LockBit. These developments were aided by data gathered in “Operation CRONOS,” an international effort to disrupt and dismantle the LockBit group and its affiliates.

Arrests in the UK and France
The NCA executed multiple search warrants across the U.K. in August 2024, arresting two individuals with suspected ties to LockBit. One individual was apprehended for potential violations of the Computer Misuse Act, blackmail, and money laundering. Another individual faced arrest solely on money laundering charges. These arrests were made possible through the analysis of data acquired during Operation Cronos, showcasing the operation's ongoing success in identifying real-world actors linked to the ransomware syndicate.
French authorities arrested a suspected LockBit developer while they were vacationing outside of Russia. Although details about this individual remain under wraps due to French legal constraints, the arrest underscores the growing international pressure on LockBit's inner circle. The developer faces serious charges as part of France's broader case against the LockBit organized crime group.
Disruption of infrastructure in Spain
In a separate but related move, Spanish law enforcement arrested a key suspect at Madrid Airport, who owned a Bullet Proof Hosting service — an essential part of LockBit's infrastructure. Nine servers used to facilitate LockBit operations were seized as part of the arrest, providing valuable information for further prosecution of core members and affiliates. The Spanish Guardia Civil's actions have significantly weakened LockBit's global network, targeting both its infrastructure and its support systems.
LockBit kneels down
Although other ransomware operations continue unabated, LockBit has taken a crucial hit by these operations, showing inability to return to previous activity levels despite its attempts.
“LockBit's reputation has been tarnished by the Operation Cronos disruption and their recovery attempts have been undermined as a result,” explain the authorities. “The financial impact of this disruption has not only impacted Dmitry Khoroshev, a.k.a. LockBitSupp, but has also deprived associated threat actors of their funds.”
LockBit, a ransomware-as-a-service (RaaS) operation, provided affiliates worldwide with access to tools and infrastructure to conduct cyberattacks. Between June 2022 and February 2024, LockBit's operations were expansive, targeting over 7,000 entities across countries like the U.S., U.K., France, Germany, and China, including more than 100 hospitals and healthcare organizations.
In a major turning point, the NCA compromised LockBit's network in February 2024, leading to a significant decrease in LockBit's activity. The unmasking of its leader, Dmitry Khoroshev (alias “LockBitSupp”), earlier this year by international forces marked the beginning of the threat group's end.







Leave a Reply