
A USB attack named ChoiceJacking subverts protections on Android and iOS devices by using malicious chargers to spoof user consent dialogs and silently access sensitive data.
The attack bypasses long-standing defenses against JuiceJacking, rendering nearly all current USB data protection mechanisms ineffective.
ChoiceJacking was developed by researchers at the Graz University of Technology. Their work revives the once-mitigated threat of malicious charging stations by combining the capabilities of USB hosts and peripherals in a single attack chain.
Where JuiceJacking relied on trusting USB connections by default, modern systems require user interaction to authorize data access. ChoiceJacking breaks this model by injecting fake input events that simulate user approval, allowing the attack to proceed without any legitimate interaction.
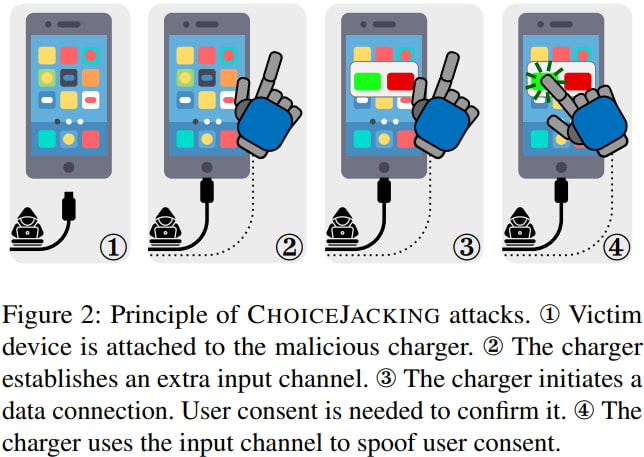
The researchers identified three attack techniques, all launched from a specially crafted charger that costs under $100 to build:
- AOAP Exploit: Misuses Android’s Open Accessory Protocol to inject input events during USB data negotiation. This enables the charger to confirm prompts for file access or debugging without user awareness.
- Input Queue Race Condition: Fills Android’s input event queue with crafted sequences that execute precisely when a user consent prompt appears, confirming the prompt automatically.
- Bluetooth HID Spoofing: Uses the charger to pair a hidden Bluetooth keyboard, which is then used to interact with the UI and approve USB connections. This method also works on iOS.
All three techniques exploit systemic flaws in the USB trust model, allowing a charger to switch roles between host and peripheral using USB Power Delivery, thereby enabling hybrid attacks that previous mitigations did not anticipate.
To increase stealth, the researchers introduced a power line side-channel (PLSC) that detects opportune moments to attack, such as during phone calls, when screens are off, or when users are distracted. The charger monitors power fluctuations to infer user activity and launches the attack when detection risk is lowest.
This mechanism was trained using machine learning models capable of distinguishing call activity and screen states based on real-time current data from the charger.
Devices affected by ChoiceJacking
Mobile OSes currently require user interaction to approve USB host connections (like file transfers or debugging), but they trust input devices and accessories by default. ChoiceJacking exploits this gap by emulating input devices to automate the approval process.
The researchers argue this trust model is flawed, especially with the rise of dual-role USB-C ports. Malicious hardware can now fluidly switch between host and device modes, enabling attack combinations that legacy mitigations cannot block.
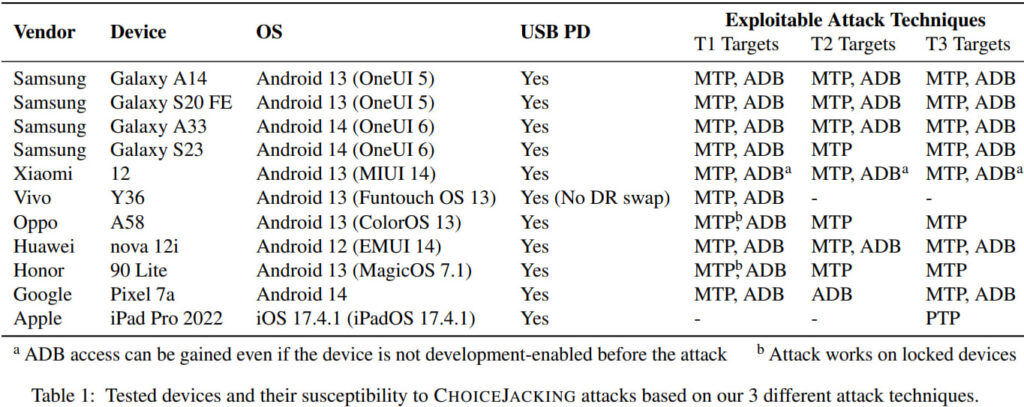
The team tested 11 devices from major vendors, and confirmed the following:
- Samsung: All tested devices were compromised in under 300ms.
- Xiaomi: ChoiceJacking gained full ADB access even on devices not previously set up for development.
- Oppo & Honor: Attacks succeeded even while the screen was locked.
- Google Pixel & Vivo: Attacks succeeded on AOSP builds with minimal modification.
- Apple (iPad Pro): Attackers could extract photos via PTP, though code execution was blocked due to authentication requirements.
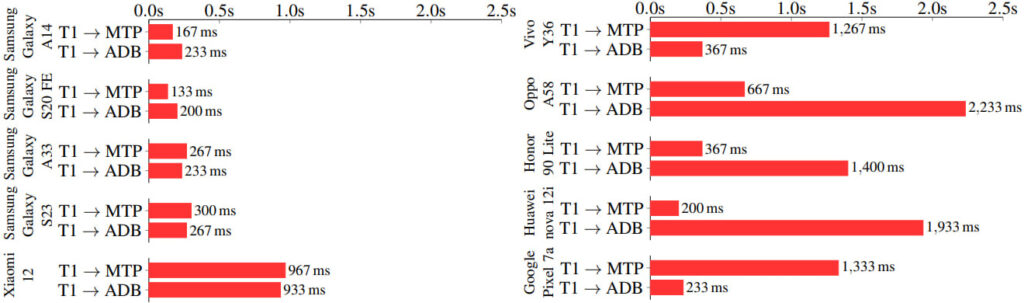
On average, file access was achieved in 333ms across Android devices. Full code execution was possible on unlocked, development-enabled devices in under 316ms.
The team disclosed 16 vendor-specific vulnerabilities, plus additional upstream issues to Google and Apple. All vendors but one acknowledged the findings. Google and Samsung have assigned CVEs (CVE-2024-43085, CVE-2024-20900), and mitigation efforts are ongoing.
Until security patches reach users, they are recommended to avoid connections to public USB charging stations, and enable ‘Lockdown Mode’ on iOS or ‘Advanced Security’ on Android that block USB attacks.







Leave a Reply