
Microsoft has identified a new North Korean threat actor, Moonstone Sleet, employing both traditional and innovative methods for financial gain and cyber-espionage.
Active since early 2023, this group has targeted various sectors, including software development, education, and defense. Moonstone Sleet’s tactics involve setting up fake companies and job opportunities, distributing trojanized versions of legitimate tools, creating malicious games, and delivering custom ransomware.
Moonstone Sleet “gaming” tactics
Moonstone Sleet first appeared on Microsoft’s radar when its activities showed significant overlaps with those of Diamond Sleet, another North Korean group. Initially, the hackers reused Diamond Sleet’s malware and techniques but soon transitioned to its own infrastructure and methods, establishing itself as a distinct, well-resourced threat actor. This shift allowed Moonstone Sleet to conduct concurrent operations alongside Diamond Sleet, leveraging their shared tradecraft.
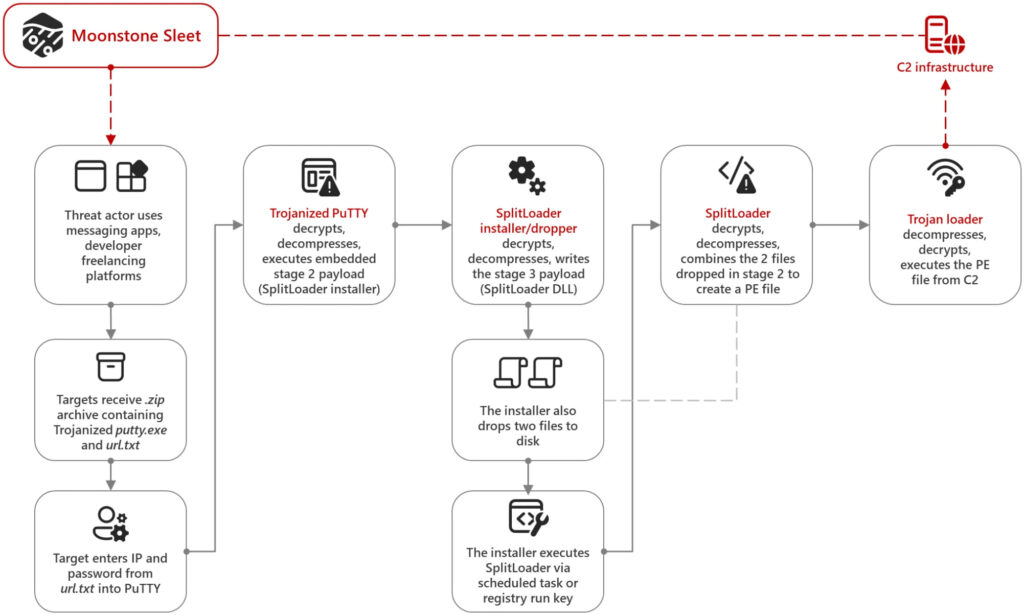
One notable technique employed by Moonstone Sleet involves distributing a trojanized version of PuTTY, an open-source terminal emulator. In early August 2023, Moonstone Sleet began delivering this malware through platforms like LinkedIn, Telegram, and developer freelancing sites. The trojanized PuTTY was often sent in a .zip archive containing putty.exe and a text file with an IP address and password. When the user entered these credentials into PuTTY, it decrypted and executed an embedded payload, leading to a multi-stage malware attack.
Microsoft
This attack sequence involved several stages, starting with the decryption of the stage 2 payload and culminating in a trojan loader that executed compressed and encrypted files from the command-and-control (C2) server.
Moonstone Sleet also targeted victims through malicious npm packages distributed via freelancing websites and professional networking platforms. These npm packages are connected to actor-controlled IP addresses to drop additional malicious payloads like SplitLoader. In one incident, a fake company used a malicious npm loader to steal credentials from the LSASS process, highlighting the group’s ability to exploit various vectors.
Another significant tactic involved a malicious tank game called DeTankWar, also referred to as DeFiTankWar, DeTankZone, or TankWarsZone. Since February 2024, Moonstone Sleet has used this game to infect devices.

Microsoft
The group masqueraded as game developers seeking investment or support, using fake companies like C.C. Waterfall to distribute the game. When users launched DeTankWar, it executed a custom malware loader called YouieLoad, which performed network and user discovery and collected browser data. For high-value targets, Moonstone Sleet conducted hands-on-keyboard attacks to further their espionage efforts.
Recent ransomware campaigns
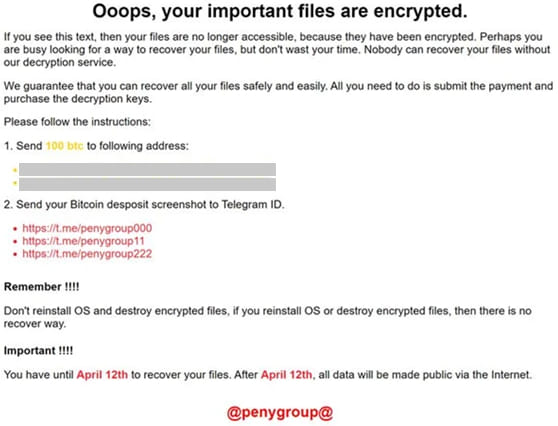
In April 2024, Moonstone Sleet introduced a new custom ransomware variant named FakePenny. This ransomware was deployed against a company previously compromised in February. FakePenny included a loader and an encryptor, with the ransom note closely resembling that of the notorious NotPetya malware. The ransom demand was $6.6 million in Bitcoin, a significant increase compared to previous North Korean ransomware demands.
Microsoft
To facilitate its operations, Moonstone Sleet created several fake companies, impersonating legitimate software development and IT services firms. Since January 2024, these fake companies, such as StarGlow Ventures and C.C. Waterfall, have targeted thousands of organizations with collaboration offers and job opportunities. These campaigns aimed to establish relationships that could be leveraged for malicious access or revenue generation.
Microsoft
In addition to fake companies, Moonstone Sleet sought legitimate employment in software development positions at various organizations. This strategy aligns with previous reports from the U.S. Department of Justice about North Korea’s use of skilled remote IT workers to generate revenue.
The threat group’s primary goals appear to be espionage and financial gain. It has targeted software companies, developers, and defense technology firms, stealing credentials, intellectual property, and deploying ransomware. The diversity of Moonstone Sleet’s tactics and its ability to conduct concurrent operations indicate that it is a well-resourced and sophisticated threat actor, very likely state-sponsored.
Microsoft recommends several defenses against Moonstone Sleet’s attacks, including the following:
- Utilize Microsoft Defender XDR and enable features like controlled folder access, tamper protection, and network protection.
- Follow credential theft prevention strategies and use EDR in block mode.
- Configure full automated mode for investigation and remediation in Microsoft Defender for Endpoint.
- Enable cloud-delivered protection for rapid response to new threats.
- Implement rules to block executable content from email and webmail and protect against credential theft from LSASS.
Microsoft says it continues to track Moonstone Sleet’s activities and will provide updates as new information becomes available. Organizations are urged to remain vigilant and implement the recommended defenses to protect against this emerging threat.







Leave a Reply