
Microsoft has uncovered a large-scale malvertising campaign that compromised nearly one million devices worldwide, distributing information-stealing malware via GitHub.
The attack, detected in early December 2024, originated from illegal streaming websites that redirected users through multiple malicious domains before delivering payloads hosted on GitHub, Dropbox, and Discord.
Microsoft Threat Intelligence began tracking this campaign in December 2024 and attributed it to Storm-0408, a threat actor group known for phishing, SEO poisoning, and malvertising to distribute malware. The attack primarily targeted users accessing illegal streaming sites, which embedded malvertising redirectors within movie frames. These redirectors funneled users through a multi-layered attack chain, leading to malware-hosting repositories on GitHub and other platforms.
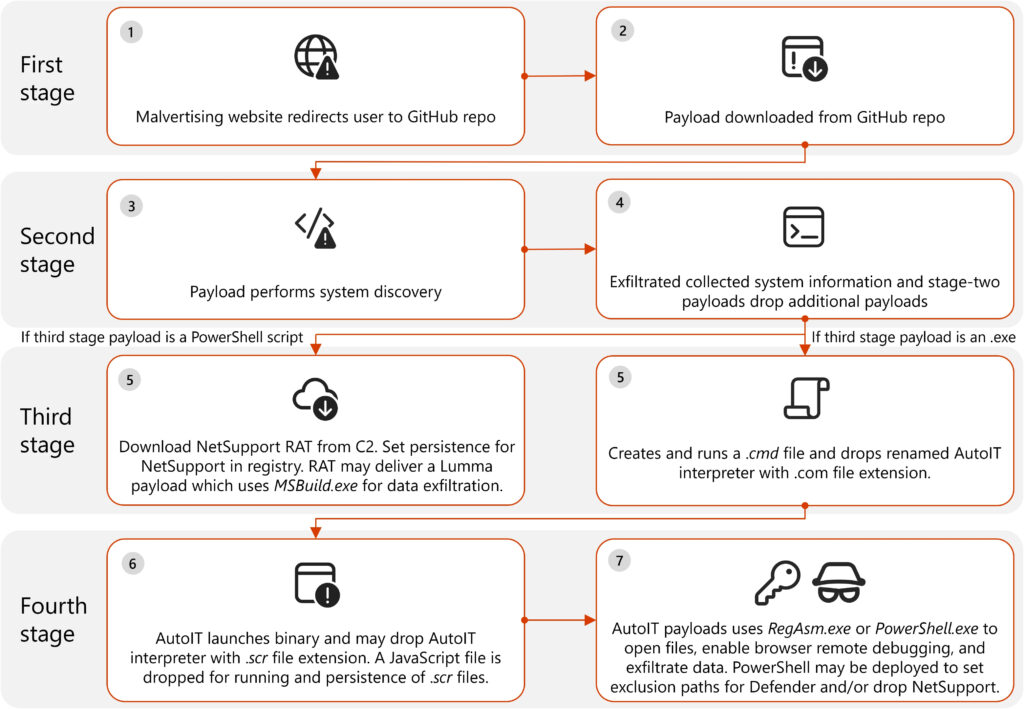
The attack followed a multi-stage infection process:
Initial Infection – The first-stage payload, downloaded from GitHub, Dropbox, or Discord, established a foothold on the victim's device. Many of these payloads were digitally signed with newly created certificates, which were later revoked by security firms.
System Reconnaissance – Second-stage payloads performed system discovery and exfiltrated device details (e.g., memory size, GPU, OS version, and screen resolution) to command-and-control (C2) servers via HTTP requests.
Malware Deployment – Based on the second-stage payload, third-stage malware was deployed, including Lumma Stealer, Doenerium, and NetSupport RAT, along with PowerShell and AutoIT scripts for persistence and defense evasion.
Data Exfiltration and Control – The final stage involved stealing browser credentials, monitoring user activity, and enabling remote debugging on browsers like Chrome and Edge to intercept sensitive data. Persistence was ensured through registry modifications, scheduled tasks, and startup folder shortcuts.
Microsoft
Malware hosted on GitHub
GitHub played a central role in hosting the first-stage payloads, which acted as droppers for additional malware. Microsoft reported multiple repositories being used to distribute these payloads, which were promptly taken down after detection. However, alternative payloads were also discovered on Dropbox and Discord, indicating a diversified hosting strategy by the attackers.
The malicious files were designed to evade detection, using living-off-the-land binaries and scripts (LOLBAS) like PowerShell.exe, MSBuild.exe, and RegAsm.exe. These were leveraged for code execution, persistence, and exfiltration of stolen credentials and other sensitive information.
The attack chain was complex, involving up to five redirection layers:
- Illegal Streaming Sites – Embedded iframes delivered malvertising redirectors.
- Malicious Redirector Domains – Intermediate redirectors filtered traffic.
- Malvertising Distributors – Redirected users to scam sites or fake downloads.
- Final Landing Pages – Delivered malware-hosting GitHub repositories.
Microsoft researchers determined that these redirects often led to fake software downloads, tricking users into installing info-stealers under the guise of legitimate applications.
With nearly one million devices affected, this attack underscores the growing threat posed by malvertising and cloud-hosted malware. While GitHub, Dropbox, and Discord have removed the malicious payloads, threat actors continue to exploit these platforms to distribute malware via new campaigns, channels, and accounts.







Leave a Reply