
Microsoft’s Digital Crimes Unit (DCU) has taken down 240 fraudulent websites tied to phishing operation ONNX, led by Egypt-based cybercriminal Abanoub Nady, known online as “MRxC0DER.” The action disrupts a widespread “Phishing-as-a-Service” (PhaaS) network that sold DIY phishing kits to threat actors worldwide. This operation facilitated cyberattacks across multiple sectors, with the financial services industry being particularly affected due to its sensitive nature.
A Look Inside ONNX
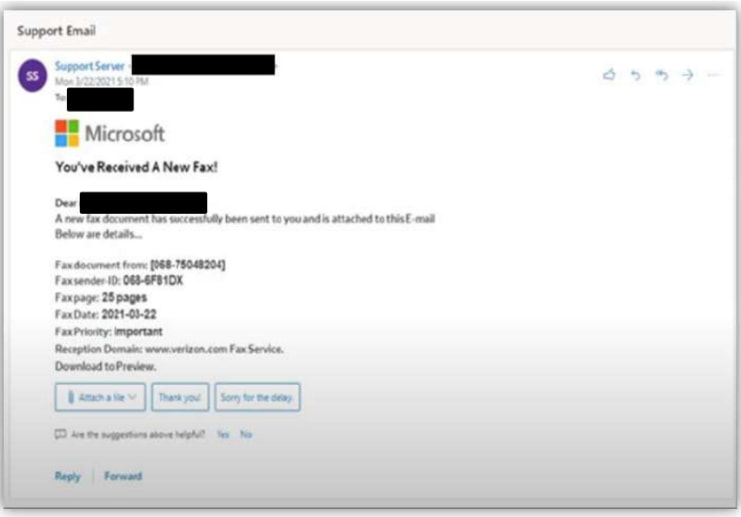
The fraudulent ONNX network was among the top five phishing kit providers by email volume in early 2024, according to Microsoft’s Digital Defense Report. These kits enabled cybercriminals to bypass advanced security measures such as Multifactor Authentication (MFA) by leveraging adversary-in-the-middle (AiTM) phishing techniques. AiTM attacks allow attackers to secretly intercept network communications, steal credentials, and manipulate authentication cookies. Microsoft has observed a 146% rise in AiTM attacks over the past year.
Microsoft
Nady’s operation also capitalized on emerging tactics like QR code phishing, or “quishing,” which uses embedded QR codes to direct victims to malicious domains. By September 2023, phishing attempts leveraging QR codes accounted for nearly 25% of all phishing emails observed by Microsoft analysts.
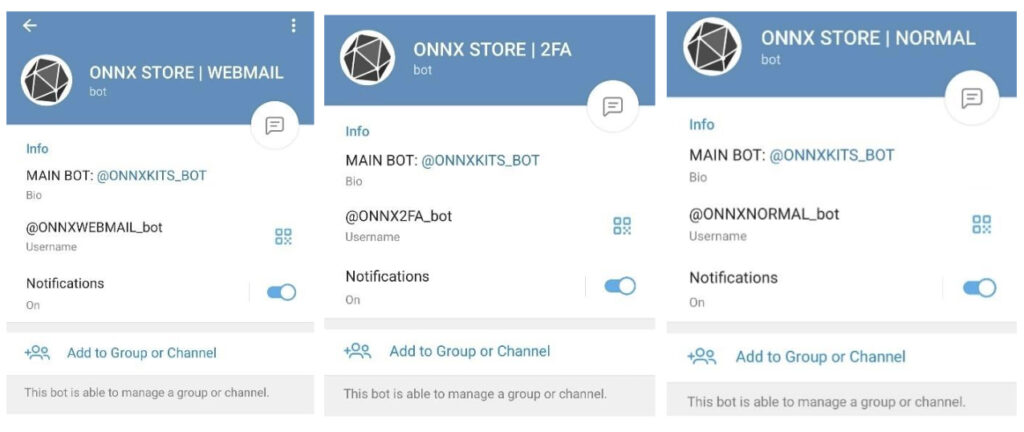
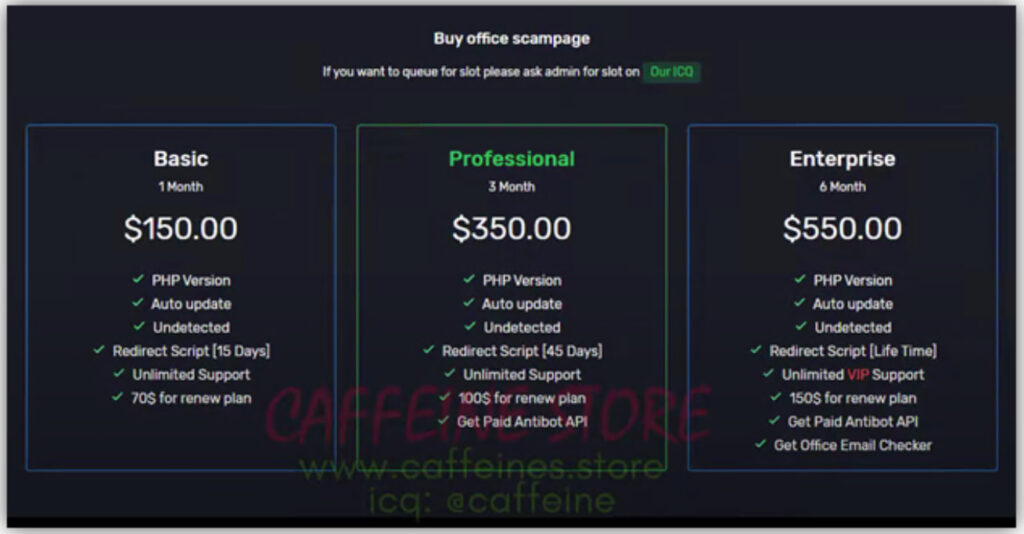
Operating since 2017, Nady’s fraudulent ONNX brand offered a subscription-based model for phishing tools, complete with tiered package — Basic, Professional, and Enterprise — with the highest tier offering “Unlimited VIP Support.” These kits were marketed primarily through Telegram channels and supported by instructional videos on social media, enabling purchasers to scale their phishing campaigns easily. Customers used the infrastructure provided by ONNX to conduct attacks, connecting purchased domains to ONNX systems to exploit victims globally.
Microsoft
The ONNX phishing kits played a significant role in the broader PhaaS industry, allowing even novice threat actors to launch attacks on Microsoft accounts and other targets. The financial consequences for victims, especially in the financial sector, were devastating, with many losing life savings to fraudulent schemes.
Microsoft
Extensive legal and collaborative efforts
Through a civil court order unsealed in the Eastern District of Virginia, Microsoft redirected the malicious infrastructure supporting the fraudulent ONNX operation to its control. This effectively severed access to the phishing systems for Nady and his customers, permanently halting their operations.
The crackdown was carried out in collaboration with the Linux Foundation (LF) Projects, LLC, which owns the legitimate ONNX trademark. Together, the organizations aim to combat the misuse of trusted brand names by cybercriminals to enhance the credibility of their operations. Publicly naming Nady serves as a deterrent to other cybercriminals seeking to exploit similar tactics.







Leave a Reply