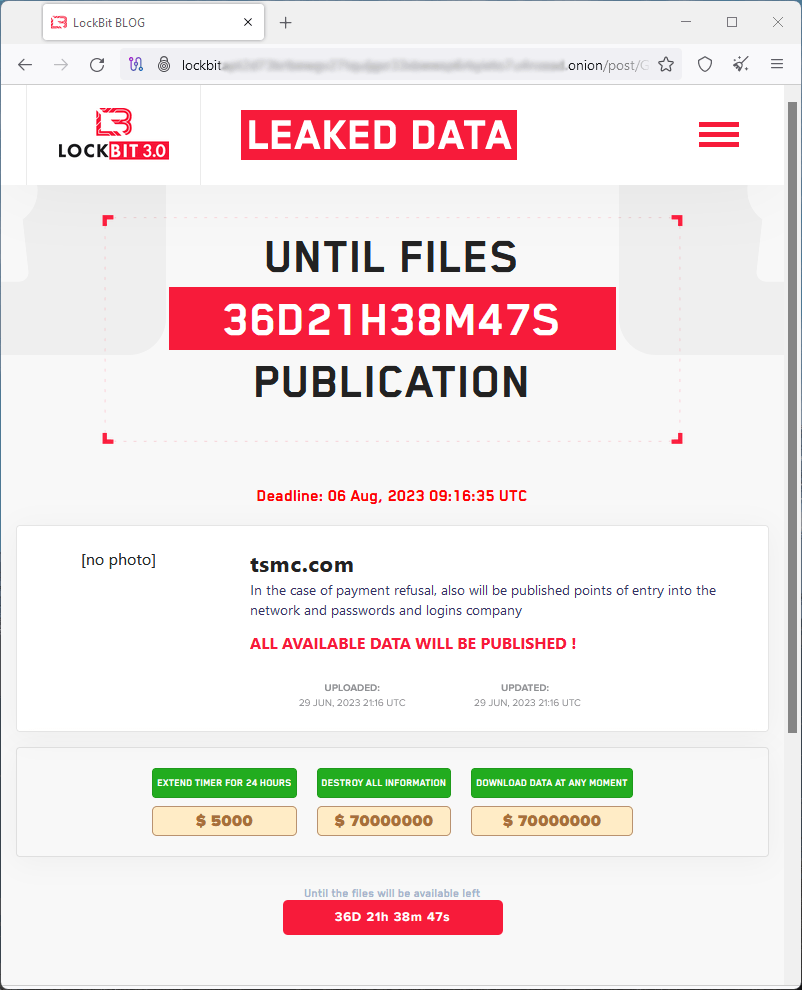
The LockBit ransomware gang has today announced TSMC (Taiwan Semiconductor Manufacturing Company) on its extortion site, demanding a ransom payment of $70 million.
TSMC is the world’s most important semiconductor manufacturing company, employing over 65,000 specialists and having an annual revenue of $57 billion.
The ransomware group, which currently operates the third major version of its ransomware-as-a-service (RaaS) platform, alleges that it has stolen files from the Taiwanese giant and threatens to publish them when the deadline is reached, on 06 August 2023.
LockBit threatens that if TSMC refuses to meet their demands, they will publish all files they stole from its systems, including “points of entry to the network” and “passwords and logins.” The ransom amount is also the price of the data, so anyone paying the same is offered to download it from LockBit’s servers. Also, the group offers 24-hour extensions for $5,000.
RestorePrivacy
TSMC Denies Breach
RestorePrivacy has contacted TSMC to request a comment on the allegations made by LockBit, and a spokesperson responded by telling us that the ransomware gang has attacked one of their hardware suppliers, Kinmax.
TSMC has recently been aware that one of our IT hardware suppliers experienced a cybersecurity incident which led to the leak of information pertinent to server initial setup and configuration. At TSMC, every hardware component undergoes a series of extensive checks and adjustments, including security configurations, before being installed into TSMC’s system. Upon review, this incident has not affected TSMC’s business operations, nor did it compromise any TSMC’s customer information. After the incident, TSMC has immediately terminated its data exchange with this concerned supplier in accordance with the Company’s security protocols and standard operating procedures. TSMC remains committed to enhancing the security awareness among its suppliers and making sure they comply with security standards. This cybersecurity incident is currently under investigation that involves a law enforcement agency.– TSMC spokesperson to RestorePrivacy
Presumably, LockBit misidentified its victim after seeing TSMC-related documents on the supplier’s breached systems or opted to claim TSMC on its extortion portal to raise media attention.
Furthermore, RestorePrivacy received a statement of the breached supplier, signed by Kinmax’s Vice President. The notice defines the date of the breach as 29 June 2023 and claims that the attackers stole installation and configuration instructions Kinmax sends to customers. Hence, it is unclear exactly what data LockBit might hold, and what their actual value is.

RestorePrivacy







It’s a great time to be in the business of credit monitoring and anti-ransomware security.
Just ask my friend Bob, who made a fortune selling his services to the corporations/victims of cyberattacks.
He says he loves his job, because he gets to help people and make money at the same time. He also says he has a lot of free time, because he doesn’t have to worry about getting hacked himself.
Bob uses a secret password that no one can guess: 123456. What a genius!
Great article Heinrich.
There appears to be a large contrast in the professionalism of how organisations handle communications surrounding breaches (attacks). Given the breach occurred on the date 29 June 2023 and for the organisations to be in a position to respond to RP by 30 June 2023 is impressive and maybe indicative that there is really nothing much to see in this event.
A significant compromise or breach of TSMC would really be the mother load, it wouldn’t be sold on dark web forums, it would be sold in embassies. A compromise / breach of TSMC would attract the full attention of Western three letter agencies and I don’t think we would come to know about it directly but in that event, the escalation may become quiet apparent.
G.L. all,