
Kape Technologies is a growing player in the VPN industry and now owns four VPN providers. Given this entity's prominence in the privacy' security space, we felt the need to closely examine its history, past business activities, and involvement in the ad injection industry.
When you use a VPN service, you are putting a lot of trust in the VPN itself and the people running it. You trust that they are properly encrypting your traffic, securing their server network, infrastructure, and apps, and also not doing anything shady in the background. In a sense, you are choosing to trust a VPN service with your traffic instead of your internet service provider (ISP), which will not be able to see any activity with all traffic being encrypted through the VPN.
And while there are verified no logs VPN services that have been audited or passed real-world tests, there have also been a handful of VPNs that have given up logs to various entities. Additionally, we have seen security breaches, such as the recent WindScribe security incident where servers were left fully unencrypted — a fact that came to light only after their servers were seized by Ukrainian authorities. Needless to say, finding a VPN you can trust is crucial.
Note: And for anyone foolishly claiming that an ISP deserves your trust and is not tracking all your online activities, read this first. (Everyone needs a good VPN for basic digital privacy when ISPs collect everything.)
Now let's take a closer look at Kape Technologies.
Numerous publications discussing Crossrider and malware
Over the past few years, we have frequently connected Kape Technologies (formerly Crossrider) with malware distribution. Why did we do this? Well, there are numerous outlets and security experts that discussed the problems and removal techniques of Crossrider malware and adware.
Here are just three examples of this:
- this 2018 article from Malwarebytes
- this article from Symantec
- this 2019 article from Security Boulevard
Based on this information and other sources, we previously assumed that Crossrider was the creator of this malware. However, it's important to get the details exactly right, so let's dig deeper.
Crossrider created a development platform for browser extensions
Crossrider was founded all the way back in 2011, when there was no native extension interoperability between browsers. This meant that development for browsers was more time-consuming. Crossrider developed a platform to address this exact issue, as TechCrunch noted in a 2012 article:
Crossrider, which is coming out of beta today, aims to make things a bit easier for developers. The service offers a cross-platform development platform for Chrome, Firefox, Internet Explorer and Safari.
Developers who want to use the service, which is available for free, only have to write their code once and can then deploy their extensions across the supported browsers.
We also see developers praising Crossrider as a tool for developing browser extensions. Here are a few quotes:
Crossrider is, in layman terms, a wrapper around your JavaScript code with a consistent set of API methods.
–Amaslo.com
Crossrider also makes it easy to publish to chrome store as well and provides an easy way to sign your extension for executable downloads on windows.
–StackOverflow
Crossrider created monetization options that were used by ad injectors
Longtime readers of RestorePrivacy know that advertising and data collection go hand in hand, along with the abuse of privacy. And while it is true that Crossrider created a development platform, we must also point out that Crossrider offered monetization options that were used by major ad injectors.
What is an ad injector exactly?
A Forbes article from 2015 discussed the topic in more detail, where they noted the following:
[Ad injection] effectively intercepts users’ traffic to inject content, namely, those irritating adverts and popups that seem to come from nowhere. Media rightly jumped on the report, highlighting the companies named as the top ad injectors. What went unnoticed, until now, is that most of the searchable organisations involved in this potentially dangerous business are based in Israel. They also happen to have links to the nation’s military and its top signals intelligence agency, the Israeli equivalent of the NSA or GCHQ: Unit 8200, which works out of the Israel Defense Forces (IDF).
The report that Forbes noted above is this 2015 research paper that was co-authored by UC Berkeley, Google, and a handful of other organizations and individuals. The paper describes the ad injection industry as follows:
Today, web injection manifests in many forms, but fundamentally occurs when malicious and unwanted actors tamper directly with browser sessions for their own profit. In this work we illuminate the scope and negative impact of one of these forms, ad injection, in which users have ads imposed on them in addition to, or different from, those that websites originally sent them.
The research paper also describes Crossrider involvement in this industry:
Crossrider is a mobile, desktop, and extension development platform that enables drop-in monetization via major ad injectors. Crossrider provides its affiliate ID to ad injectors while separately tracking kick-backs to developers. The other top affiliates listed in Table III are all cross-browser extensions and plugins that impact Chrome, Firefox, and Internet Explorer.
We can see Table III from the research paper below. In it, we find that Crossrider listed as a \”Top Affiliate\” with different Ad Injection Libraries.
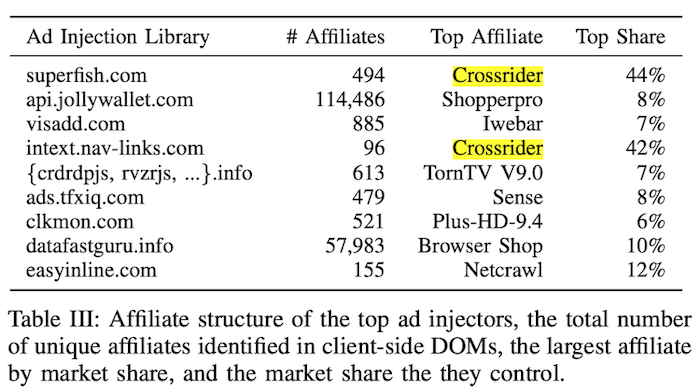
The exact relationship between the ad injectors and affiliates is complex.
In the context of Crossrider, it was the underlying tool that developers used to create extensions, rather than the owner of the extension itself or the monetization platform responsible for the ads.
Legitimate (non-malicious) apps were also made with Crossrider
While Crossrider did offer monetization options that were used by ad injectors, we should also point out that Crossrider's platform was also used for legitimate (non-invasive) purposes.
You can see this with the FC Barcelona official fan app, which was attributed to “Crossrider Advanced Technologies Ltd.”
Additionally, we see CNet and The Next Web writing about an app called Chat Undetected, which was also attributed to Crossrider.
Now let's examine how the Crossrider platform was also used for not-so-good activities.
Various third parties used Crossrider's platform for bad practices (malware)
While Crossrider created tools for software developers and ad injectors, these tools were also useful to bad actors.
We see a few examples of this on herdProtect, a malware scanning platform:
- mySupermarket Companion (flagged as malware) – “It is built using the Crossrider cross-browser extension platform. While the file utilizes the Crossrider framework and delivery services, it is not owned by Crossrider.”
- I Want This (flagged as adware) – “Crossrider is the owner of a platform that enables the creation of cross-browser extensions by developers but is not the owner of this detected application.”
We also see Brian Krebs, the renowned cybersecurity expert, further clarifying how the Crossrider platform was being used by third parties for malicious endeavors:
- “Last week, I wrote about LilyJade, a new computer worm that was spreading across Facebook accounts by abusing the free services offered by Crossrider, a platform that makes it simple to develop browser extensions that work seamlessly across browsers and operating systems.” (KrebsOnSecurity.com)
- “The purpose of this post is not to cause alarm about legitimate development platforms like Crossrider and Kango, or even to dissuade people from using Facebook. It’s also true that rogue browser plugins are hardly a new problem.” (KrebsOnSecurity.com)
A Crossrider employee also explained on StackOverflow how the company\'s tools were being exploited by bad actors:
We had some incidents in the past where developers had tried to write malicious extensions using our framework, but with our security co-operations with Google and Facebook we managed to mitigate them.
Following the news about Kape buying Private Internet Access, Andrew Lee, the PIA co-founder, explained Crossrider's business on a HackerNews thread as follows:
To be clear, in the past the company was known as CrossRider and provided a developer SDK that could be used to integrate with browsers. Unfortunately, CrossRider didn\'t do enough to prevent malware (like platforms these days and their fake news) and the platform was used by some bad people for bad purposes.
Kape was never directly involved in adware other than providing SDKs that let developers create positive and negative things.
Crossrider shuts down the platform and rebrands the business
In September 2016, Crossrider officially announced it was shutting down entirely, as you can see in this official tweet. Crossrider provided RestorePrivacy with further clarification about their decision to shut down operations in 2016:
The team saw that abuse of the platform was not showing signs of slowing down, and the very openness and flexibility that made the platform useful for developers also made it difficult to effectively combat abuse.
The following year, in 2017, we see that the business pivoted to an entirely different niche: online privacy and security. The purchase of CyberGhost in 2017 kicked off this strategy, followed by a name change to Kape Technologies shortly thereafter.
Additionally, we learned that Crossrider had a major personnel change to refresh the business with new leadership. The Crossrider co-founders, CEO Koby Menachemi and CTO Shmueli Ahdut, left the company, along with most of the original Crossrider team and its entire C-suite of executives.
Today, Kape is led by CEO Ido Ehrlichman, who was not part of Crossrider's original team. Kape is a global company that is headquartered in London and publicly traded on the London Stock Exchange.
Kape's statement to RestorePrivacy
In our research for this article, Kape provided us with a statement to further clarify the past events and explain their reasoning to change their business strategy:
The Crossrider SDK and development platform was used by tens of thousands of independent developers to create cross-browser extensions, and unfortunately a small number of bad actors misused the platform to develop adware and malware. The team at the time attempted to combat the problem, including as a participant and supporter of the Clean Software Alliance, but ultimately decided to shut down Crossrider altogether in 2016 in the face of rising abuse.
Due to how the Crossrider platform worked, extensions by developers using the platform typically appeared linked to Crossrider in one way or another. This had the unfortunate effect of some of these extensions being incorrectly attributed to Crossrider itself, including by automated adware and malware scanning and removal tools. And while Crossrider itself didn’t exist anymore after 2016, developers who had developed or compiled their app using Crossrider prior to its shutdown were able to continue distributing their own apps by themselves.
Kape is now a leading privacy-first digital security software provider, with a fully refreshed team led by new CEO Ido Erlichman and informed by having identified a market need for privacy solutions to protect users’ data.
Conclusion: Why this is important
For years, we have been discussing Kape under the assumption that it was responsible for the malware being associated with Crossrider. The full story, however, is more nuanced.
For starters, it is clear that Crossrider provided a platform that was used by ad injectors.
However, it also appears that Crossrider's development platform was used by third parties to spread malware, and Crossrider was not responsible for this.
Getting the details correct is important because it helps people decide whether or not to trust a business that offers privacy tools. And with trust being a huge consideration, it\'s important to focus on verifiable facts.
Given everything we learned in our research, we can conclude that:
- Crossrider created a development platform, which was used for many different purposes (both good and bad).
- Crossrider offered monetization options with its platform and was used by major ad injectors.
- Third parties also used Crossrider's platform for malware distribution, but Crossrider was not the owner or creator of that malware.
- Crossrider completely shut down the program in 2016, changed out the company's leadership, and pivoted to the privacy and security niche.
- In 2018, Crossrider changed its name to Kape Technologies.
Now that Kape is a big player in the VPN industry, hopefully this article can help people who are considering whether or not to use Kape's products. These products now include ExpressVPN, Private Internet Access, CyberGhost, and ZenMate VPN.







Dear reader,
“Israeli-Cypriot businessman Sagi acquires Kape Technologies for $1.6 billion.” Source: Google search, Media.
According to the media reports, Sagi had strange business connections with Russian “business partners” 😉
“Former Malware Distributor Kape Technologies now owns ExpressVPN, CyberGhost, Private Internet Access, Zenmate, and a collection of VPN” – Source: Reddit.
Why are this man and his organization purchasing VPNs worldwide and what kind of malware is everyone talking about??
Well, I think it is something that looks like: Pegasus. And what is Pegasus?
Pegasus is a highly sophisticated program developed by the Israeli cyber-arms company called NSO Group. This spyware is licensed to various governmental agencies worldwide, which has resulted in it being used for cyber-espionage against targets of interest, such as politicians, activists, journalists, human rights activists and so on.
Pegasus is designed to be covertly and remotely installed on mobile phones running iOS and Android. By the way, Pegasus can also activate microphone and camera on your smartphone without you noticing it.
Pegasus is the desired software (or malware) of the dictators in this world, they love to buy it for the mass surveillance.
Question: Can the person who owns many VPN companies make a lot of money with users private data? and sell them to the governments? .. Answer: I do not know 😉
I don’t claim that everything I wrote is true, I just think it can be that way 😉
Read more: Pegasus and similar spyware and secret state surveillance (PDF)
[https://rm.coe.int/pegasus-and-similar-spyware-and-secret-state-surveillance/1680ac7f68]
“Crossrider completely shut down the program in 2016, changed out the company’s leadership, and pivoted to the privacy and security niche.” If so, getting rid of the former leadership and cleaning house could also be seen as removing some of the bad actors in the business. Since the acquisitions, I’ve heard of no abuses. Remember, NordVPN was hacked, but it’s not a reason to avoid the company; it’s a reason to investigate what happened and learn about whether and how it affected users. I’ll give Kape a chance before condemning them whole cloth.
Not just that but private internet access had a notoriously scummy ceo. Making that the first stop on their acquisition tour really cemented their untrustworthy reputation. I was getting ready to switch to expressvpn when I heard kape had acquired them. Now you couldn’t pay me to use it.