
The Windows client of CyberGhost VPN older than version 8.3.10.10015 is vulnerable to a flaw that could allow attackers to perform command line injection and escalate their privileges on the impacted system.
According to a report by the security researcher who discovered the flaw, a specially crafted JSON payload sent to the CyberGhost RPC service during the launch of the OpenVPN process can lead to complete system compromise.
Users of the popular VPN software are recommended to upgrade to client version 8.3.10.10015 or later, released on February 24, 2023, to address the problem.
Vulnerability Details
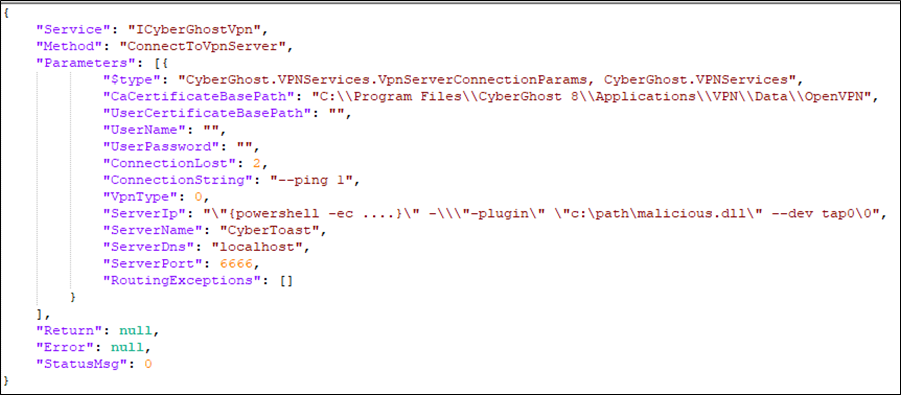
The CyberGhost VPN client vulnerability (CVE-2023-30237) is an elevation of privilege issue that allowed attackers to inject malicious command lines using a crafted JSON payload.
By exploiting the RPC service, which was intended to only accept requests from the same process, attackers could bypass the process origin check, manipulate the communication protocol, and gain complete system control through OpenVPN’s plugin feature.
The “Pen Test Partners” researchers explain that despite CyberGhost’s developers implementing various protections, such as ensuring the named pipe isn’t accessible over the network and correctly configuring JsonSerializer to prevent arbitrary .NET type creation, it is still possible to exploit the vulnerability by cleverly crafting the payload and manipulating command line arguments, leading to successfully bypassing existing protections.
The point of failure lies in the developers overlooking some nuances of the CommandLineToArgvW API while constructing the command line string argument. By exploiting this oversight, the researchers could craft a payload that embeds a malicious command in the ServerIp field.
Pen Test Partners
Negative Disclosure Experience
The flaw was reported to CyberGhost VPN upon discovery on January 3, 2023, and a response by the product owner, Kape Technologies, urged the researcher to submit the report to the firm’s Bugcrowd platform, where it runs a bug bounty and vulnerability disclosure program.
The researcher reports that the experience following this avenue was cumbersome and time-wasting, and his initiative to share technical details over email with Kape resulted in Bugcrowd penalizing him for demonstrating unprofessional behavior and violating their Code of Conduct for making “Out of Band Contact” with the software vendor.
After several additional rounds of communication with both Kape and Bugcrowd, the platform deducted the “code of conduct point” allotted previously as a penalty and apologized.
Kape Technologies owns various top digital security and privacy products, such as ExpressVPN, CyberGhost, Private Internet Access, ZenMate, and Intego. Unfortunately, it’s concerning that a security researcher must use external platforms to submit a crucial security report. This process can lead to wasted time and put millions of users at risk of malicious exploitation.
RestorePrivacy has reached out to CyberGhost VPN for a comment on the above but has not heard back by the time of publication.
Update: CyberGhost provided RestorePrivacy with a verbose comment, below:
We’d like to highlight that the blog post published by PenTestPartners is not representative of CyberGhost’s operating procedures, nor our general experience with BugCrowd. We launched CyberGhost’s bug bounty program in 2022 to build on our existing commitment to transparency and to work with the privacy and security community and with our customers to make our service even more secure. We believe collaboration in the cybersecurity community is critical to ensure security and privacy on the internet. As an example, we recently collaborated with a researcher via BugCrowd who identified 2 weaknesses in our CyberGhost Linux application, and worked with him to publish his findings. You can find more information in the link below. The BugCrowd disclosures are linked at the bottom: https://mmmds.pl/cyberghostvpn-mitm-rce-lpe/
The PenTestPartners blog post describes an unfortunate, isolated incident with BugCrowd and is not reflective of either CyberGhost’s or BugCrowd’s standards. The researcher had initially submitted a previous issue via BugCrowd which was looked into and found to be invalid. The researcher then made a further vulnerability disclosure but because their previous issue had not been accepted via BugCrowd, this time they tried to circumvent BugCrowd’s disclosure process. As a result, some challenges were encountered during the communication process. Once the communications issues were resolved and we had received the disclosure from the researcher we worked quickly to address it and a fix was applied swiftly.
We launched CyberGhost’s bug bounty program in 2022 to build upon our excellent transparency record, and vulnerability disclosures submitted in good faith play a key part in helping us to drive forward our commitment to security. Engaging with a public bug bounty program enables us to work with the wider security community to react to new threats and deliver excellence in this field.
CyberGhost’s bug bounty program is just one of the reasons users can be confident that they are using a secure, trustworthy VPN service. CyberGhost’s customers can also rest assured that absolutely no logs are kept of any customers’ activities; and any requests that are received are published in their quarterly transparency reports, alongside confirmation that they have never had any data available to share. Last year CyberGhost’s infrastructure underwent an independent audit by Deloitte, which provided further confirmation of CyberGhost’s No Logs Policy, proving that server configurations align with internal privacy policies and do not identify users or pinpoint their activities.– CyberGhost







Could we get a review on something like this…?
https://www.expressvpn.com/aircove
I never liked Cyber Ghost VPN. And I disapprove of some of the practices of Kape Technology like buying VPN review websites and ranking their VPNs higher. Cyber Ghost might be good for unblocking streaming websites and cheap but it is not a fast VPN and is inferior to the likes of Surfshark and Nord VPN.
Another one of Kape’s crap. Never trusted these guys.
You pay for what you get . If you want a VPN that does what it does correctly , dont cheap out . If you used CyberGhost for torrenting only , I would not worry too much . They know what you are there for and security isnt a life or death matter .
Not always, you may pay more and get less.
You can get a few good free VPNs like Windscribe that do the job nicely for most people. And there are other non-free VPNs which offer fair value. Cyberghost has always been iffy to me.