
A malware campaign by the threat group UNC6032 has been exploiting public excitement around AI video generators to distribute Python-based infostealers, backdoors, and downloaders.
According to a detailed report by Mandiant (Google), thousands of fake social media ads on Facebook and LinkedIn have been used to funnel victims toward fraudulent AI-themed websites, ultimately infecting systems worldwide.
Impersonating real AI brands
The investigation identified more than 30 malicious websites, often mimicking popular AI brands like Luma AI, Canva Dream Lab, and Kling AI. Ads promoting these sites reached over 2.3 million users in the EU alone, according to Meta’s Ad Library, though the exact number of infections remains unknown. Meta began removing many of these ads in 2024, even before Mandiant’s alert, while LinkedIn recorded tens of thousands of impressions through a handful of related campaigns. Google’s Threat Intelligence Group (GTIG) assesses UNC6032 to have a Vietnam nexus, with a target range spanning multiple industries and geographies.

Luma AI, one of the impersonated brands, is a genuine company offering cutting-edge text-to-video generation, drawing in creators, marketers, and designers. Fraudulent lookalike domains like lumalabsai[.]in exploit this reputation, offering users “free” AI video generation that ultimately leads to malware downloads. Clicking “Start Free Now” on these fake sites produces a fake loading sequence and serves a ZIP archive containing a hidden executable.
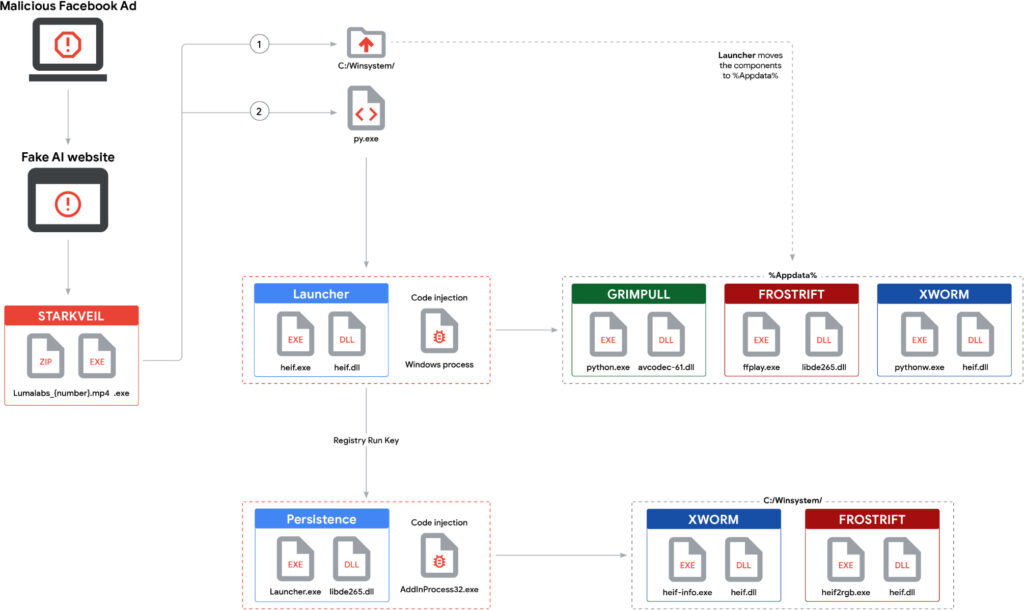
The malware chain begins with the STARKVEIL dropper, a Rust-based loader that uses Unicode Braille characters in filenames (such as Lumalabs_1926.mp4⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀.exe) to obscure the .exe extension. When executed, STARKVEIL extracts components into C:\winsystem\, and launches obfuscated Python scripts (COILHATCH) that decrypt multi-stage payloads. These payloads use DLL side-loading, process injection, and registry persistence to run three core modules:
- GRIMPULL: A .NET downloader with Tor-based C2 communications and advanced anti-VM checks, responsible for fetching and running additional payloads.
- XWORM: A .NET backdoor offering keylogging, screen capture, plugin management, and C2 interaction over TCP, with victim data exfiltration to Telegram.
- FROSTRIFT: Another .NET backdoor focusing on reconnaissance of installed applications, crypto wallets, and browser extensions, using GZIP-compressed Protobuf over SSL/TCP for C2 communication.
Together, these modules allow attackers to steal credentials, cookies, credit card data, and sensitive information from password managers, digital wallets, and authenticators. They use multiple C2 channels — Tor tunnels, Telegram API, and specific ports like 7789, 25699, and 56001 — to maintain robust, redundant communication.
Mandiant observed UNC6032’s infrastructure rapidly rotating domains to evade detection, with most ads short-lived and new ones appearing daily. The group’s payloads are functionally similar but employ varied obfuscation techniques, creating a flexible, persistent infection chain resilient to partial takedowns. Meta and LinkedIn’s transparency tools helped investigators estimate ad reach and campaign scope, but Mandiant suspects similar activity continues across other social media platforms.
To protect against this type of malware campaign, users and organizations should verify the legitimacy of AI tools before downloading, checking official websites and trusted sources, and avoid clicking on AI tool ads seen on social media, and instead navigate directly to known official domains.







Leave a Reply