
Security analysts at Kaspersky have spotted an ongoing malware distribution campaign leveraging modified Tor Browser installers that siphon user browsing data and execute commands on their systems.
The unsigned installers hosted on a cloud service are promoted by an anonymity-focused YouTube channel that counts over 180,000 subscribers, while the particular video that pushes the malicious Tor build has 64,000 views.
The earliest infections were detected by Kaspersky's security products in March 2022, primarily focusing on Chinese users who seek unofficial Tor distribution channels due to a government ban on the anonymous browser.
Tor directs internet traffic through a volunteer overlay network, masking the user's IP address and maintaining browsing anonymity while helping bypass internet censorship, both crucial issues for Chinese netizens.
The malicious version promoted to these users looks identical to the genuine Tor Browser, but it's configured to record browsing history and log anything typed on website forms.
Below is a screenshot of the particular YouTube video.
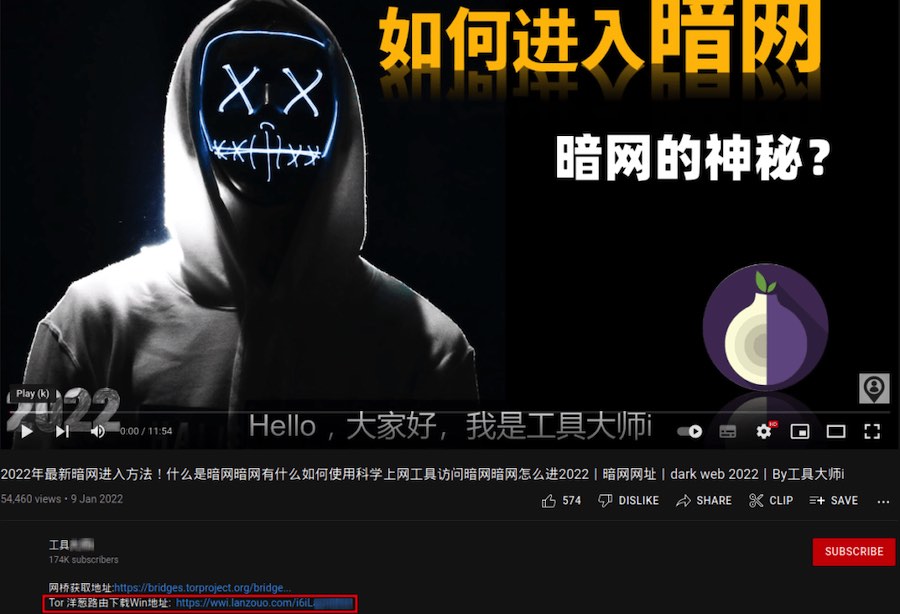
Additionally, the custom browser caches pages on the disk, stores extra session data from websites, and has auto-filling of login data enabled by default.
While these may seem like innocuous interventions to make using this custom version of Tor more comfortable, the fact that the malware phones to a command and control (C2) server with POST requests is a clear indication of its nefarious objectives.
Source: Kaspersky
Kaspersky's analysts found that if the victim is based in China, the C2 will send a second-stage DLL in response to the POST, which generates a unique host ID and attempts to retrieve the following information:
- GUID of the operating system disk volume
- Machine GUID
- Computer name
- Computer locale
- Current user name
- MAC addresses of network adapters
The collected information is exfiltrated in encrypted form to the C2 server, and then the malware pings it every two minutes, awaiting new commands.
The commands sent by the C2 may request retrieving a list of installed software or running processes, the Tor browsing history, Google Chrome's and Edge's browsing history, WeChat and QQ account IDs, and the SSIDs and MAC addresses of the victim's WiFi network.
Additionally, the malware supports arbitrary shell command execution using “cmd.exe”, while the execution results are encrypted and sent to the C2 in the next POST request.
The malware doesn't target user passwords, cryptocurrency wallet IDs and seed phrases, browser cookies, or credit cards. Instead, its operator appears more interested in unmasking the victim's identity and discovering more about their browsing activities.
Hence, it's likely that the authors of the custom Tor browser version are members of law enforcement or other state authorities, although Kaspersky hasn't collected enough evidence for confident attribution.
Reminder: Download from the official source only
This is a reminder of the importance of downloading software installers directly from the official project sites, in this case, that is torproject.org. This is particularly important when downloading a secure browser, browser add-ons, and other privacy tools.
For Chinese people not using a VPN, the domain is out of reach. However, if they source an installer from elsewhere, they can still examine the executable's digital signature to verify the publisher.







There are only two officially recognized browsers by The Tor Project: Tor Browser (Windows, Android) and Onion Browser (iOS). Everything else is not officially supported, hence you should avoid these kind of apps.
Reminder, don’t expect facts and reliable information on social media platforms like YouTube, Facebook, Instagram, TikTok, and Reddit. Use them for entertainment purposes only!
Hi RP Team,
A fantastic article!
This a concern!
I have heard the term DIY malware and this takes the cake.
There is more than enough information on this site for most people to keep themselves safe.
For me, this site is very trusted and I have learnt a lot from you.
I am very appreciative.
Myself I don’t need high opsec – I just want people to mind their own business.
When seeking solutions, myself, I don’t need TOR – a VPN is appropriate for me.
I have never been completely satisfied with my browser options either from the Chromium or FF perspective.
Though I won’t say they don’t both have some good distributions.
I spent some time independently investigating other web browsing platforms.
What I found were solutions where I could not trust the developers.
They were either providing solutions for affiliate marketers or looked a lot like crime.
So I didn’t even test them in a VM environment.
I believe there is a tension here and it is a big mess, there are so many parties to the situation;
And everyone is trying to stay networked.
Regards,
BoBeX