
The US Cybersecurity and Infrastructure Security Agency (CISA) has issued an Emergency Directive in response to the active exploitation of two zero-day vulnerabilities in Cisco ASA and FTD devices, one of which enables persistent compromise even after device reboot or firmware upgrade.
The directive follows the discovery of a sophisticated malware toolkit composed of a GRUB-stage bootkit dubbed RayInitiator and a memory-resident shellcode loader named LINE VIPER, both targeting Cisco Adaptive Security Appliances (ASA) 5500-X series firewalls and Secure Firewall Threat Defense (FTD) systems. The malware was uncovered during a joint investigation by CISA, Cisco’s Product Security Incident Response Team (PSIRT), and allied national cybersecurity centers, including the UK’s NCSC, which released a detailed technical analysis of the campaign.
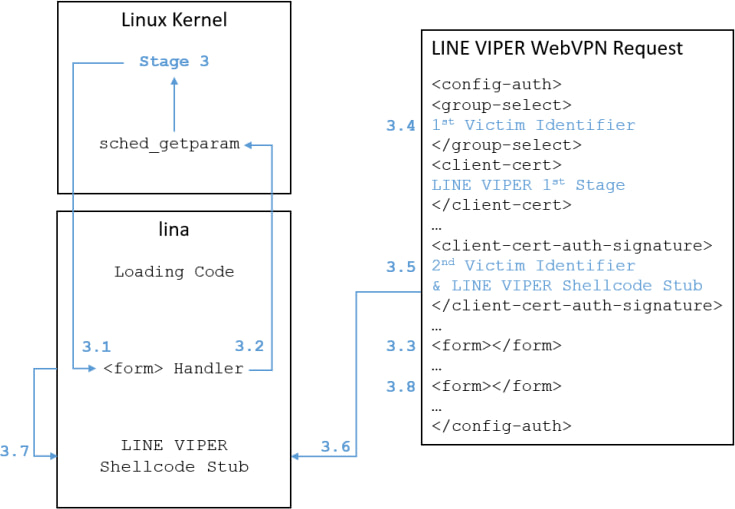
According to the NCSC’s malware analysis report, RayInitiator is a persistent multi-stage bootkit that hijacks the early boot process by patching the GRUB bootloader. It installs hooks in the Linux kernel and modifies the core ASA binary, lina, to stage and execute LINE VIPER. This infection chain enables attackers to maintain long-term access to devices even through firmware upgrades, effectively neutralizing standard remediation efforts.
LINE VIPER, the payload executed in memory, is a shellcode-based modular implant capable of:
- Executing privileged CLI commands
- Performing stealthy packet captures of protocols like RADIUS and LDAP
- Harvesting administrator CLI inputs
- Bypassing AAA mechanisms for actor-controlled devices
- Suppressing syslog messages to avoid detection
- Initiating forced or delayed reboots to disrupt forensic investigations
Tasking and exfiltration are performed covertly through HTTPS-based WebVPN authentication sessions or tunneled ICMP traffic, with AES-encrypted payloads keyed using RSA public keys unique to each victim. This encryption scheme ensures payload confidentiality even if traffic is intercepted.
NCSC
The vulnerabilities exploited to deploy this toolset are tracked as:
- CVE-2025-20333 (CVSS 9.9): A critical RCE in the WebVPN service allowing remote code execution as root on Cisco ASA and FTD devices with VPN features enabled.
- CVE-2025-20362 (CVSS 6.5): A medium-severity flaw permitting unauthenticated access to restricted endpoints on devices with WebVPN enabled.
Cisco confirmed active exploitation and has released patched firmware to address both issues. However, no workarounds are available, and the malware’s persistence mechanisms require more than just patching to fully eradicate infections.
Cisco’s Secure Firewall ASA 5500-X series, the prime targets, are either past or nearing their end-of-support date (September 30, 2025), making them particularly vulnerable due to the absence of secure boot and cryptographic validation in early firmware stages.
CISA mandates that federal agencies inventory all in-scope devices, collect forensic images for compromise assessment, disconnect end-of-support devices, and apply patches or upgrade supported systems by September 26, 2025, at 11:59 PM EST.







Leave a Reply