
An advisory released by CISA, in collaboration with the FBI, HHS, and MS-ISAC, highlights the escalating threat posed by the Black Basta ransomware, which has affected over 500 organizations worldwide, including critical infrastructure across 12 sectors.
The advisory outlines actionable steps for organizations to fortify their defenses against this potent cyber threat while also laying the threat group's tactics, techniques, and procedures (TTP) in detail.
Black Basta operations
Black Basta, a ransomware-as-a-service (RaaS) variant first identified in April 2022, has significantly disrupted operations globally, targeting sectors such as Healthcare and Public Health (HPH). The FBI investigations and third-party reports detail the ransomware's dual extortion tactic—encrypting victim data and threatening publication unless a ransom is paid. Notably, Black Basta does not specify ransom amounts in its initial notes; instead, it provides a unique code for victims to initiate contact via a .onion URL.
The advisory emphasizes the ransomware's reliance on phishing, exploiting known vulnerabilities (like ConnectWise CVE-2024-1709), and abuse of legitimate credentials for initial access. Black Basta actors employ various tools such as SoftPerfect network scanner and PowerShell for network scanning and disabling security measures. For lateral movement, tools like BITSAdmin, PsExec, and Cobalt Strike beacons are utilized.
To combat these threats, CISA strongly recommends immediate updates to operating systems and software, the implementation of phishing-resistant multi-factor authentication (MFA), and training for users to recognize phishing attempts. These actions are part of broader mitigation strategies aligned with the Cross-Sector Cybersecurity Performance Goals developed by CISA and NIST.
Victims are urged to report ransomware incidents to their local FBI field office or CISA and are advised against paying ransoms. Payment does not guarantee data recovery and may further encourage criminal activities.
Black Basta campaign exposed
In a related report by Rapid7, a novel social engineering campaign associated with Black Basta was identified, targeting multiple managed detection and response (MDR) customers. This campaign involves overwhelming users with spam emails followed by a phone call pretending to be from IT support, tricking users into downloading malicious software that facilitates unauthorized access.
Rapid7's analysis has not observed ransomware deployment directly but has linked the indicators of compromise to Black Basta based on previous engagements and open-source intelligence. The firm suggests robust measures, including baselining environments for installed remote monitoring and management solutions, application allowlisting, and user training to recognize and report suspicious activities.
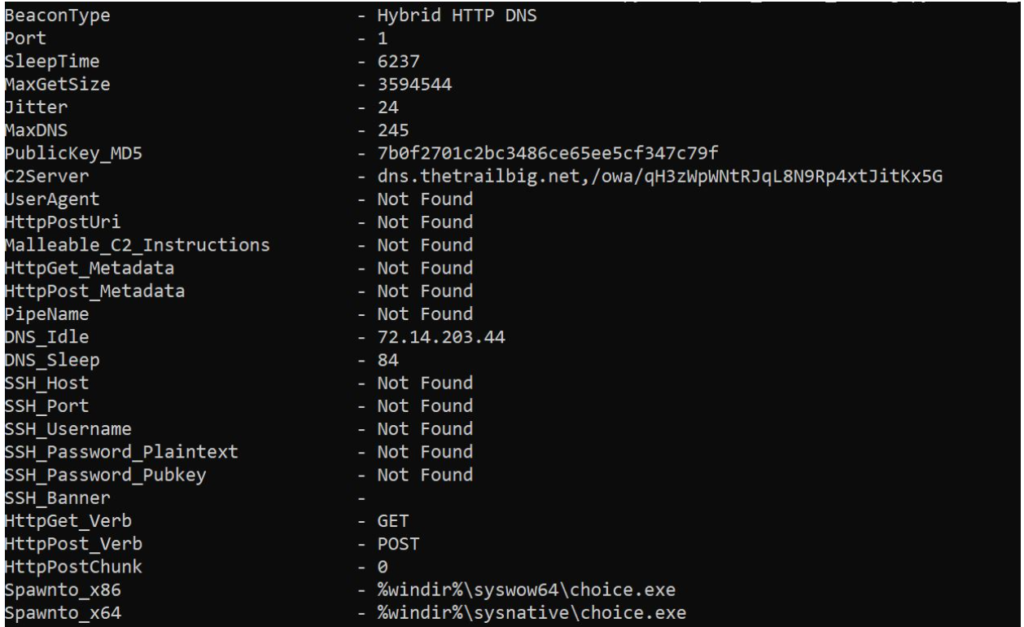
Rapid7
Both the CISA advisory and Rapid7 report underscore the necessity of heightened vigilance and proactive cybersecurity practices. Organizations across all sectors, especially critical infrastructure, are advised to review and enhance their security protocols in line with the recommendations to guard against the evolving threat landscape posed by ransomware actors like Black Basta.







Leave a Reply