
A newly uncovered cyber espionage campaign led by the Chinese state-sponsored hacking group Salt Typhoon (Red Mike) has compromised vulnerable Cisco devices worldwide, targeting telecommunications providers across multiple countries, including the United States, the United Kingdom, and South Africa.
The attack exploits two critical privilege escalation vulnerabilities, CVE-2023-20198 and CVE-2023-20273, found in Cisco IOS XE software, allowing the threat actors to establish persistent access and siphon sensitive data.
Salt Typhoon targeting Cisco devices
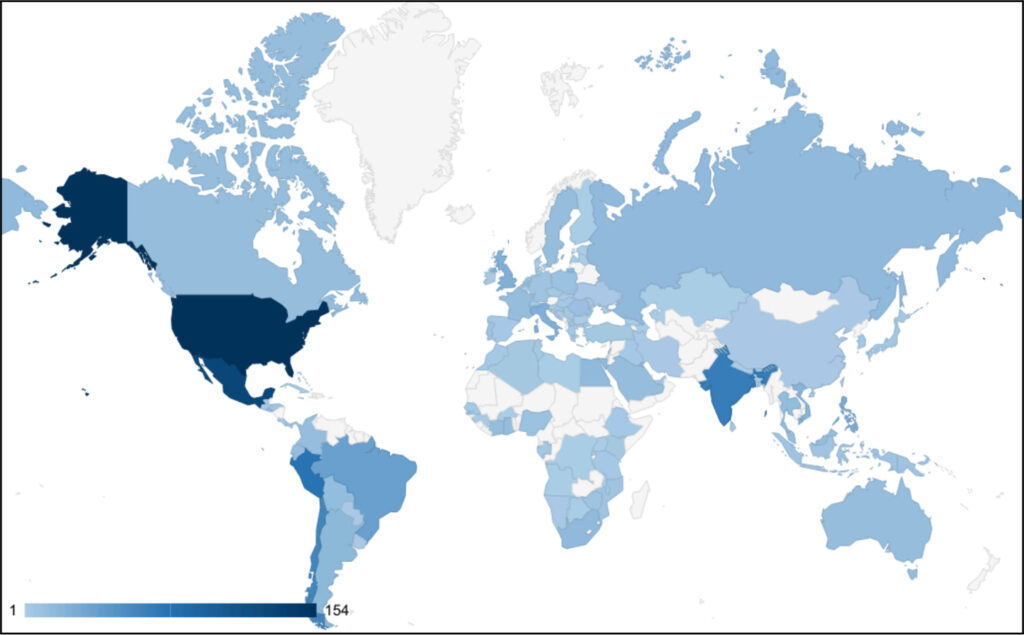
Between December 2024 and January 2025, cybersecurity researchers at Recorded Future‘s Insikt Group tracked Salt Typhoon's activities, identifying that the group had attempted to exploit over 1,000 Cisco devices globally.
The hackers primarily targeted network infrastructure belonging to telecommunications providers but also extended their focus to university networks in Argentina, Bangladesh, Indonesia, Malaysia, Mexico, the Netherlands, Thailand, the U.S., and Vietnam. Institutions such as UCLA and TU Delft were likely targeted due to their research in telecommunications, engineering, and technology.
Recorded Future
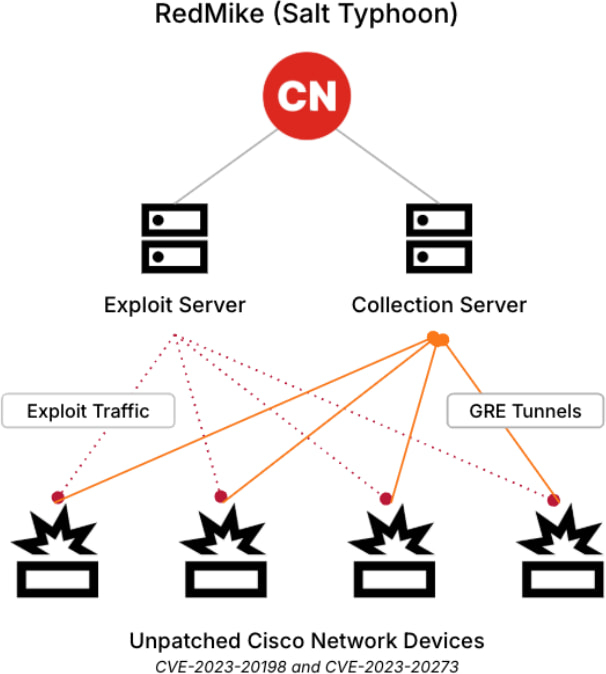
Salt Typhoon gains initial access by exploiting CVE-2023-20198, a flaw in the web user interface (UI) of Cisco IOS XE software, enabling them to create unauthorized privileged accounts. Once inside, they leverage CVE-2023-20273 to escalate privileges to root access, allowing them to manipulate device configurations.
The attackers then install a Generic Routing Encapsulation (GRE) tunnel, providing them with a persistent foothold for data exfiltration and covert network traffic monitoring.
Recorded Future
Strategic intelligence operations
Salt Typhoon's operations underscore a broader strategy by Chinese state-backed hackers to infiltrate critical infrastructure. Persistent access to telecommunications networks enables adversaries to eavesdrop on sensitive conversations, manipulate data traffic, and potentially disrupt communications during geopolitical crises. The group's previous targeting of U.S. lawful intercept programs and surveillance of U.S. political figures through telecom breaches further highlights the national security risks posed by these intrusions.
Among the confirmed victims are:
- A U.S.-based affiliate of a major U.K. telecommunications provider.
- A South African telecommunications company.
- A large Thai telecommunications provider.
- A U.S. internet service provider (ISP).
- An Italian ISP.
Additionally, in mid-December 2024, Salt Typhoon conducted reconnaissance against Myanmar-based telecom provider Mytel, likely scanning for vulnerabilities in its corporate infrastructure, including its mail servers.
Sanctions and response
Despite heightened awareness and U.S. sanctions against Salt Typhoon-linked Sichuan Juxinhe Network Technology Co., Ltd., the group continues its operations unabated.
The U.S. Department of the Treasury sanctioned the company on January 17, 2025, citing direct involvement in hacking U.S. telecommunications and internet service providers. Sichuan Juxinhe is allegedly linked to China's Ministry of State Security (MSS), reinforcing concerns over state-backed cyber operations targeting global infrastructure.
This escalation has further strained U.S.-China relations, with the Biden administration previously banning China Telecom's remaining operations in the U.S. as part of broader efforts to curb foreign cyber espionage.







A few months ago, when a vulnerability was discovered in the IPv6 protocol stack on Windows, my friend, who is a superfan of Linux, maliciously asked me, “How’s your company’s router?” In my company’s network design, I only kept some switches without routing capabilities and used Windows Server 2022 as the router to control communication between different subnets. I replied at the time, “I patched it the very morning the vulnerability was reported!” Now I can ask him—, “How are your large number of Linux routers that are never updated?”