
Cybersecurity researchers from HUMAN’s Satori Threat Intelligence and Research team, in collaboration with Google, Trend Micro, and Shadowserver, have partially disrupted a massive fraud operation known as BADBOX 2.0.
The botnet, which evolved from the BADBOX malware discovered in 2023, is now the largest ever uncovered involving infected connected TV (CTV) devices. Researchers found that over 1 million consumer devices — primarily uncertified Android-based tablets, smart TVs, digital projectors, and other connected devices — were compromised, enabling a wide range of fraudulent activities.
HUMAN
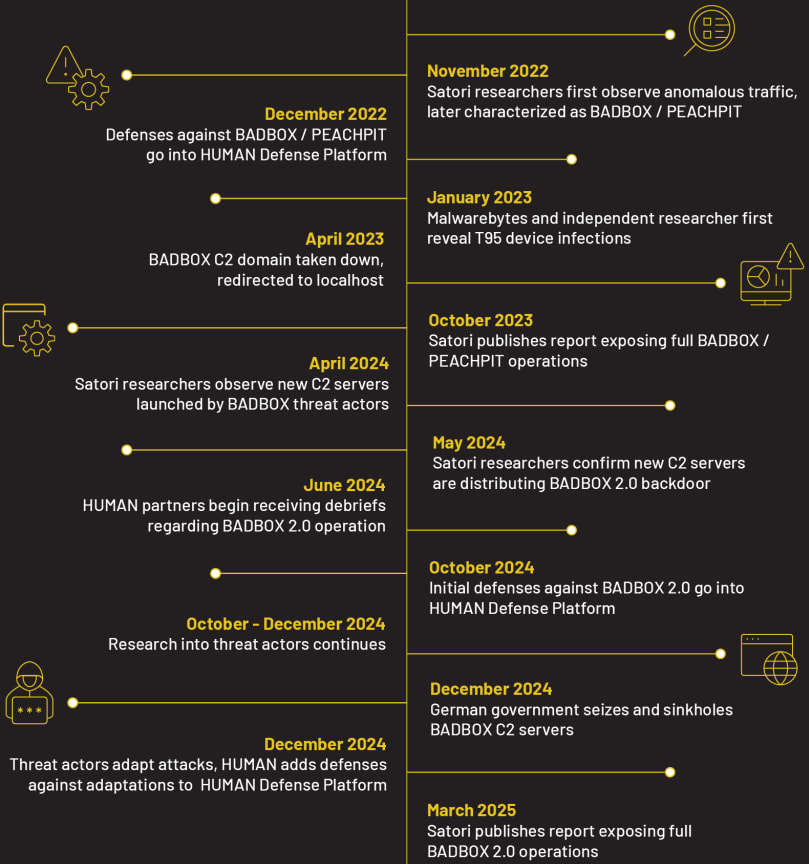
BADBOX 2.0 is an evolution of the original BADBOX botnet, which was partially dismantled in December 2024 when Germany’s Federal Office for Information Security (BSI) sinkholed key C2 servers, disabling 30,000 infected devices. However, despite these efforts, BADBOX expanded and was later found to have infected over 192,000 devices globally, according to Bitsight’s research in December 2024.
Unlike earlier versions, BADBOX 2.0 introduces a more sophisticated backdoor (BB2DOOR) that enables cybercriminals to push any payload to an infected device, increasing its adaptability and making mitigation more difficult.
HUMAN
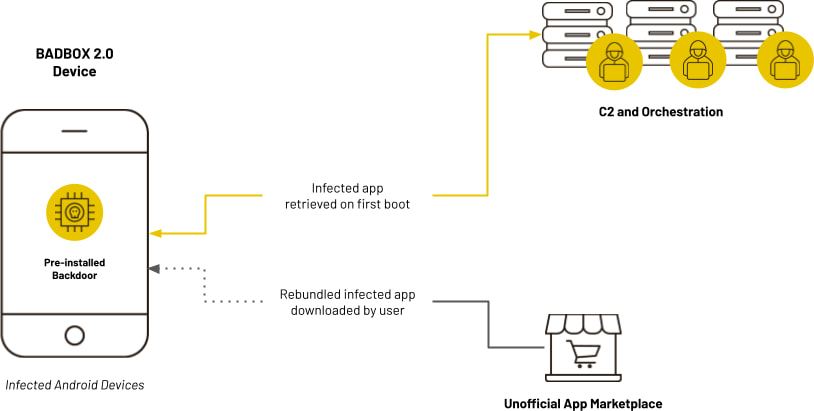
How BADBOX 2.0 works
The BADBOX 2.0 operation expands on the original BADBOX campaign by leveraging backdoors pre-installed on low-cost consumer electronics. These backdoors allow threat actors to remotely deploy malware modules and connect devices to a command-and-control (C2) infrastructure.
The infected devices were primarily Android Open Source Project (AOSP) devices, not certified by Google Play Protect, making them vulnerable to supply chain attacks. These devices communicate with C2 servers operated by distinct but cooperating cybercriminal groups, each specializing in different aspects of the attack, such as ad fraud, residential proxy services, and credential theft.
Once infected, a compromised device could perform a variety of fraudulent activities, including:
- Ad fraud – Serving hidden ads and launching hidden WebViews to generate fake ad revenue.
- Click fraud – Navigating low-quality domains and clicking on ads for financial gain.
- Residential proxy services – Selling access to the device’s IP address for account takeover (ATO), fake account creation, malware distribution, and DDoS attacks.
- One-time password (OTP) theft – Potentially intercepting or stealing OTPs for further exploitation.
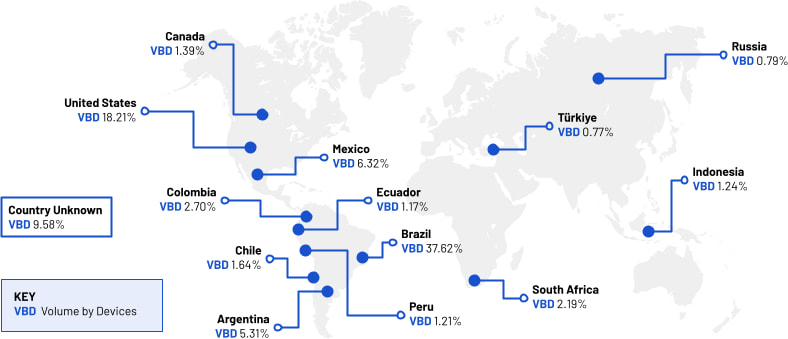
The malware’s reach was global, with traffic observed from 222 countries and territories. The affected devices were found in high concentrations in Brazil, the U.S., Mexico, Argentina, and Colombia.
HUMAN
Cybercriminals behind BADBOX 2.0
The investigation linked BADBOX 2.0 to at least four major cybercriminal groups, each playing a specific role:
- SalesTracker Group – Managed the C2 infrastructure and orchestrated the malware’s distribution.
- MoYu Group – Developed the BADBOX 2.0 backdoor and operated botnets of infected devices.
- Lemon Group – Focused on residential proxy services and ad fraud, using infected devices to drive fraudulent traffic to fake websites.
- LongTV – A Malaysia-based company whose apps were linked to a hidden ad fraud campaign.
These groups shared infrastructure, such as common C2 servers and botnet management tools, to maximize their monetization schemes.
Disrupting the botnet
Satori researchers worked with Google, Trend Micro, and other security firms to disrupt BADBOX 2.0’s infrastructure. Google took several measures, including blocking 24 malicious apps via Google Play Protect, which automatically warns users and prevents installation of BADBOX-related apps on Play Protect-certified devices. Google also removed fraudulent publisher accounts from the Google Ads ecosystem to cut off monetization streams.
While these actions reduced the botnet’s impact, the core issue of supply chain compromise remains unresolved, meaning new versions of BADBOX could emerge.
Given the risks associated with BADBOX 2.0 and similar threats, users should only buy Play Protect-certified devices manufactured by reputable brands directly associated with Google. Also, avoid installing apps from third-party app stores and flashing questionable firmware images that promise extended functionality.







Leave a Reply