This guide tracks privacy issues with antivirus software and is periodically updated with new information.
It goes without saying that reliable antivirus software plays a crucial role in IT security. As malware continues to become more sophisticated and prolific (more than 450,000 malware samples are released every single day), home users and business owners alike need to have protection in place to stop these modern digital threats.
However, antivirus products are not immune to privacy problems. While the antivirus industry is ostensibly on the side of good, many antivirus products behave in a way that infringes on users’ privacy. Whether they intercept web traffic, sell browser history data, or allow backdoor access to government agencies, many antivirus products are guilty of jeopardizing the very thing they are designed to protect: your data.
Here are five ways antivirus software may interfere with your privacy.
1. Selling your data to third-party advertisers
To provide you with the protection you need to keep your system safe, your antivirus software needs to know a lot about you. It keeps an eye on the programs you open to ensure you’re not accidentally executing malicious software, and it monitors your web traffic to stop you accessing dodgy websites that might try to steal your login credentials. It might even automatically take suspicious files it finds on your computer and upload them to a database for further analysis. This means your antivirus software could collect and process an awful lot of your personal data if it wanted to.
With great power comes great responsibility.
While some antivirus providers are quite conscientious with their users’ data and only use it when absolutely necessary, others are much less scrupulous.

AVG – A few years ago AVG came under fire when the company announced changes to its privacy policy that would allow it to sell its users’ search and browser history data to third parties (i.e. advertisers) in order to monetize its free antivirus software. Of course, AVG isn’t the only antivirus company to monetize its users’ data.
Avast – Avast’s popular free android app sends personally identifiable information such as your age, gender and other apps installed on your device to third-party advertisers. As an AVG spokesperson explained to Wired, “Many companies do this type of collection every day and do not tell their users.”
From free VPN services to free antivirus, the old adage rings true: if you’re not paying for the service, you’re probably the product.
2. Decrypting encrypted web traffic
Most modern antivirus products include some sort of browser protection that prevents you from accessing known phishing and malware-hosting websites. However, doing so is easier said than done due to the fact that so much data is now transferred via Hypertext Transfer Protocol Secure (HTTPS).
HTTPS is the protocol your web browser uses when communicating with websites. The “S” in HTTPS stands for “secure” and indicates that the data being sent over your connection is encrypted, which protects you against man-in-the-middle attacks and spoofing attempts. Today, 93 percent of all websites opened in Google Chrome are loaded over HTTPS, up from 65 percent in 2015. If you want to know if a website uses HTTPS, simply check the URL or look for a padlock icon in the address bar.
The rapid adoption of HTTPS has helped to make the web a more secure place, but it has also introduced an interesting problem for antivirus companies. Normally when you visit an HTTPS website, your browser checks the website’s SSL certificate to verify its authenticity. If everything checks out, a secure connection is established, your website loads, and you can browse away to your heart’s content, secure in the knowledge that the website is legitimate.
But there’s just one problem. Because the connection is encrypted, there’s ultimately no way for antivirus software to know if the website you are trying to visit is safe or malicious.
Most antivirus products use HTTPS interception to overcome this issue. This involves installing a local proxy server that creates fake SSL certificates. When you visit an HTTPS website, your connection is routed through your antivirus’ proxy server, which creates a new SSL certificate and checks the safety of the site you’re trying to access. If your antivirus software judges the website to be safe, the site loads as normal. If the website is unsafe, the proxy will display a warning in your browser.
By redirecting your data through a proxy, your antivirus is decrypting the data you send on encrypted connections – data that is only meant to be visible to you and the HTTPS website.
There are a few ramifications here:
- Because your antivirus is faking SSL certificates, there’s no way to be 100 percent certain that the website displayed in your browser is the real deal. In late 2017, Google Project Zero researcher Tavis Ormandy discovered a major bug in Kaspersky’s software. In order to decrypt traffic for inspection, Kaspersky was presenting its own security certificates as a trusted authority, despite the fact that the certificates were only protected with a 32-bit key and could be brute forced within seconds. This meant that all 400 million Kaspersky users were critically vulnerable to attack until the company patched the flaw.
- Most antivirus products query the safety of a URL server side, which means the company could potentially track your browsing habits if they wanted to.
- It increases the risk of phishing attacks and man-in-the-middle exploits.
A team of researchers even published a paper on the troubling security implications of HTTPS interception by popular antivirus companies, where they noted:
As a class, interception products [antivirus solutions that intercept HTTPS] drastically reduce connection security. Most concerningly, 62% of traffic that traverses a network middlebox has reduced security and 57% of middlebox connections have severe vulnerabilities. We investigated popular antivirus and corporate proxies, finding that nearly all reduce connection security and that many introduce vulnerabilities (e.g., fail to validate certificates). While the security community has long known that security products intercept connections, we have largely ignored the issue, believing that only a small fraction of connections are affected. However, we find that interception has become startlingly widespread and with worrying consequences.
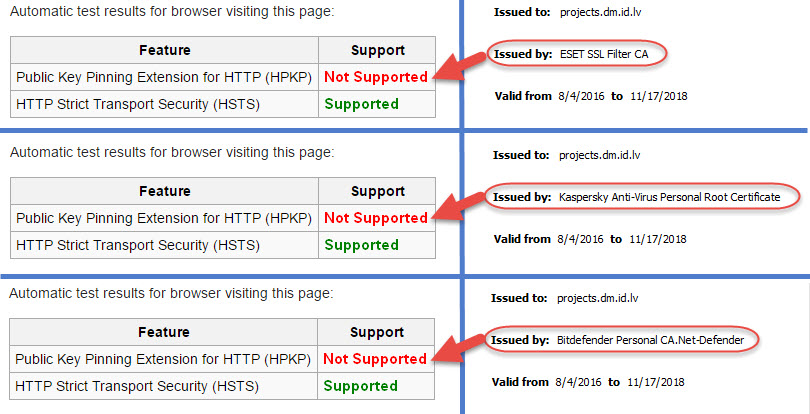
VPN.ac examined the issue as well and discovered that antivirus suites carrying out HTTPS interception also break HTTP Public Key Pinning (HPKP):
HPKP is a technology enabling website operators to “remember” the public keys of SSL certificates in browsers, enforcing the use of specific public keys for specific websites. This reduces the risk of MiTM attacks using rogue/non authorized SSL certificates. But HTTPS scanning and HPKP can't work together, therefore if a website has HPKP enabled, when you access it the support for HPKP for that site will be disabled in the browser.
VPN.ac found this to be the case with ESET, Kaspersky, and Bitdefender:
Tip: Avoid antivirus software that utilizes HTTPS interception/scanning, or just disable this “feature” within your antivirus.
3. Installing potentially unwanted programs on your computer
Even if your antivirus doesn’t pose a direct threat to your privacy, it may come bundled with software that does. As the name suggests, potentially unwanted programs, or PUPs for short, are applications that you may not want on your computer for various reasons.
While they’re technically not malicious, they usually change the user experience in some way that is undesirable, whether that’s displaying advertisements, switching your default search engine, or hogging system resources.
Many free antivirus products come with PUPs such as browser toolbars, adware, and plugins that you may inadvertently allow to be installed while quickly clicking through the installation process.
For example, free versions of Avast and Comodo try to install their own Chromium-based web browsers, which you may or may not want on your computer. Meanwhile, AVG AntiVirus Free automatically installs SafePrice, a browser extension that claims to be able to help you find the best prices while shopping online. Unfortunately, it can also read and change all your data on the websites you visit.
A few years back Emsisoft found that most free antivirus suites were bundled with PUPs. Here were the culprits:
- Comodo AV Free
- Avast Free
- Panda AV Free
- AdAware Free
- Avira Free
- ZoneAlarm Free Antivirus + Firewall
- AVG Free
PUPs aren’t inherently malicious, but they can seriously encroach on your privacy. Some PUPs will track your search history or browser behavior and sell the data to third parties, while others may compromise your system’s security, affect system performance, and hinder productivity. Keep unwanted applications off of your computer by carefully reading installation options during the setup process and only install the software and features that you need.
4. Cooperating with governments
It’s theoretically possible that antivirus software could be leveraged to help government agencies collect information on users. Most security software has very high access privileges and can see everything that’s stored on a computer, which is necessary in order for the software to keep the system to safe. It’s easy to see how this power could be used by nefarious parties to spy on individuals, businesses, and governments.
Kaspersky Lab, a Russia-based cybersecurity company whose products account for about 5.5 percent of antivirus software products worldwide, was embroiled in a major privacy scandal a couple of years ago. According to the Washington Post, Kaspersky software used a tool that was primarily for protecting users’ computers, but also could be manipulated to collect information not related to malware. Kaspersky is the only major antivirus company that routes its data through Russian Internet service providers, which are subject to Russia’s surveillance system.
In September 2017, the U.S. government banned federal agencies from using Kaspersky Labs software following allegations about cooperation between Kaspersky and Russian intelligence agencies. Shortly after, the FBI began pressuring retailers in the private sector to stop selling Kaspersky products, and the British government issued a warning to government departments about the security risks of using Kaspersky software.

Of course, it would be naive to think this issue is limited to Russian software. Similar concerns have been raised recently about Huawei equipment with “hidden backdoors” installed.
“Antivirus is the ultimate back door,” explained Blake Darché, a former N.S.A. operator and co-founder of Area 1 Security, as quoted by The New York Times. “It provides consistent, reliable and remote access that can be used for any purpose, from launching a destructive attack to conducting espionage on thousands or even millions of users.”
5. Undermining security and giving hackers access to private data
Sometimes, security software does the opposite of its desired intent by undermining your security.
One such case occurred with the Royal Bank of Scotland (RBS), which was offering Thor Foresight Enterprise to its business banking customers. In March 2019, Pen Test Partners discovered an “extremely serious” security flaw with the software that left RBS customers vulnerable:
Security Researcher Ken Munro told the BBC: “We were able to gain access to a victim's computer very easily. Attackers could have had complete control of that person's emails, internet history and bank details.”
“To do this we had to intercept the user's internet traffic but that is quite simple to do when you consider the unsecured public wi-fi out there, and it's often all too easy to compromise home wi-fi set ups.
“Heimdal Thor is security software that runs at a high level of privilege on a user's machine. It's essential that it is held to the highest possible standards. We feel they have fallen far short.”
While Heimdal was quick to patch the vulnerability within a few days, it does raise an interesting point. That is when your security software is actually undermining your security.
Choose your antivirus software wisely
In the best case scenario, antivirus companies use your data responsibly to refine their products and provide you with the best malware protection possible.
In the worst case scenario, they sell your data to third-party advertisers, install annoying software on your system, and cooperate with government agencies to spy on your personal information.
So, how do you sort the best from the rest?
- Pay for your antivirus software. Most free antivirus products will be far more liberal with your data than premium software as the company ultimately needs to monetize their services in some way.
- Read the end user license agreement. Know what you’re getting yourself into before you install the product. Take a moment to read the license agreement and/or the company’s privacy policy to find out what the organization intends to do with your data.
- Read installation options: It’s easy to blindly click through “Next” when installing new software. This can result in the installation of browser toolbars, adware, and all sorts of other PUPs, which can encroach on your privacy in various ways.
- Customize privacy settings. Some antivirus software will allow you to customize privacy settings such as usage statistics, browsing behavior, and whether to upload malicious files for analysis. Adjust these settings to maximize your privacy.
- Read AV reports. Some independent analysts release reports on how antivirus companies handle your data. Take the time to read these reports and reviews to get a better understanding of a company’s reputation and how it handles privacy matters.
It's important to note that this article isn’t a rallying call to abandon all antivirus software in the name of privacy, because there are some good players out there.
Antivirus software is an essential part of modern IT security and plays a critical role in protecting your data against malware, phishing, and a plethora of other digital attacks that pose a real threat to everyday users.
While some antivirus providers are invasive and should be avoided, there are still some companies that strive to protect their users’ privacy. Emsisoft, for example, has earned itself a reputation for providing reliable protection without compromising its users’ privacy. ClamAV is another privacy-friendly option that is completely open source.
So do your homework, weigh up your options carefully and remember that not all antivirus solutions are created equal when it comes to respecting your privacy.
This antivirus privacy guide was last updated on January 29, 2025.

Good Site