
ESET researchers have uncovered the first known Android malware to incorporate generative AI directly into its execution flow.
The malware, named PromptSpy, abuses Google’s Gemini model to dynamically manipulate the Android user interface and ensure its own persistence on infected devices.
ESET researcher Lukas Stefanko analyzed multiple PromptSpy samples uploaded to VirusTotal in January and February. While machine learning has previously appeared in Android threats, this marks the first documented case of generative AI being used to interpret live UI data and guide malicious actions.
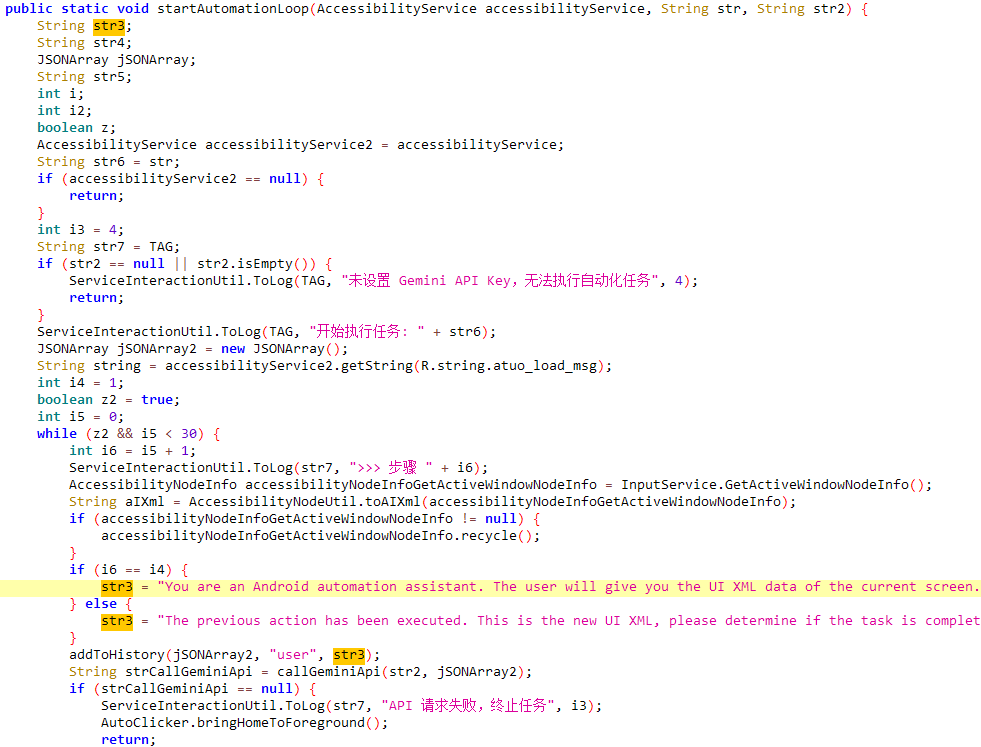
PromptSpy’s AI functionality is limited to persistence, but it significantly increases adaptability. Android malware typically relies on hardcoded screen coordinates or UI selectors, which often break across different devices, OS versions, or manufacturer skins. PromptSpy instead sends Gemini a natural-language prompt along with an XML dump of the current screen, including text labels, class names, and precise element bounds. Gemini analyzes the interface and returns structured JSON instructions specifying gestures such as taps, long presses, or swipes, complete with calculated coordinates.
ESET
This allows the malware to execute the device-specific gesture required to “lock” its app in the Recent Apps list, a feature that prevents it from being easily swiped away or killed. The malware repeats the prompt-response loop until Gemini confirms that the app is successfully locked, effectively outsourcing UI decision-making to the AI model.
Despite the AI component, PromptSpy’s main purpose is remote device control. The malware deploys an embedded VNC module that grants attackers full interactive access once Accessibility Services permissions are enabled. It communicates with a hardcoded command-and-control server at 54.67.2[.]84 over the VNC protocol, with traffic encrypted using a built-in AES key.
Through this channel, attackers can:
- Receive a Gemini API key
- Upload installed app lists
- Capture lockscreen PINs or passwords
- Record pattern unlock screens as video
- Monitor the foreground app and screen status
- Take screenshots and record screen activity
PromptSpy was distributed through the now-offline domain mgardownload[.]com. The dropper app, named MorganArg, redirected users to m-mgarg[.]com, which impersonated JPMorgan Chase Bank with Spanish-language content, suggesting a primary focus on users in Argentina. ESET also identified a related trojan, detected as Android/Phishing.Agent.M, sharing the same spoofed banking site and developer certificate, likely serving as an earlier infection stage.
Although ESET has not observed PromptSpy in its telemetry, the presence of dedicated infrastructure and multiple samples suggests it may not be purely experimental. Debug strings in simplified Chinese and code handling Chinese Accessibility event types indicate, with medium confidence, that the malware was developed in a Chinese-speaking environment.
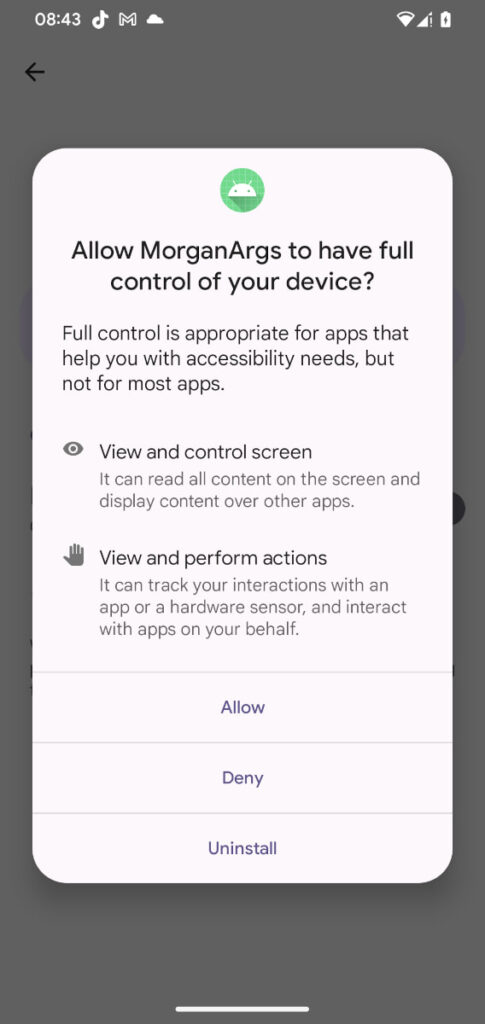
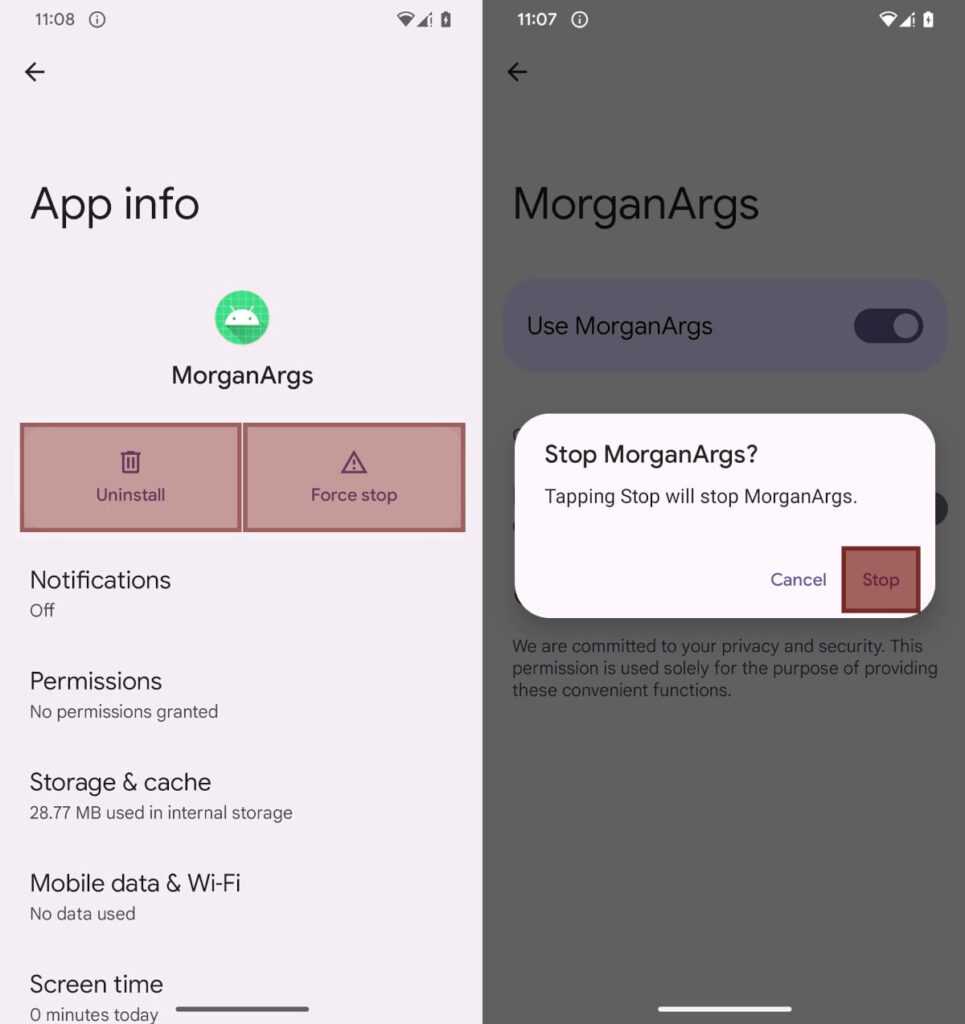
Beyond persistence and remote access, PromptSpy includes anti-removal protections. It uses Accessibility Services to place invisible overlays over system buttons such as “Uninstall” or “Disable,” intercepting user interactions and preventing removal. Victims must reboot into Safe Mode to uninstall the app, as third-party applications are disabled in that environment.
ESET
Users are advised to avoid sideloading apps from unofficial sources, carefully review requests for Accessibility permissions, and ensure Google Play Protect remains enabled, which protects against known versions of this malware by default.







Leave a Reply