
A fresh round of testing by the Electronic Frontier Foundation (EFF) and AV-Comparatives reveals significant disparities in how well Android antivirus apps detect stalkerware, with some popular products failing to identify nearly half of the tested spyware.
Conducted in August and September 2025, the evaluation shows that while some vendors have made progress, others still leave users vulnerable to digital surveillance and abuse.
Stalkerware, often marketed under the guise of parental control or employee monitoring tools, allows covert surveillance of a victim’s texts, calls, location, photos, and app usage. Its use is especially prevalent in cases of intimate partner abuse. Installation usually requires physical access to the device, after which the spyware hides itself, sends collected data to a remote server, and often resists uninstallation.
The companies behind these tools exploit legal gray areas where selling such software may be lawful in some jurisdictions, but installing it without a person’s consent is generally illegal. Vendors often include disclaimers suggesting the buyer must inform the device owner, but their software is explicitly designed for stealth. Previous breaches, including those affecting SpyX, Cocospy, and Spyic, have also exposed collected data to the public, adding a broader cybersecurity dimension to the issue.
Google Play Protect fails
The test, conducted jointly by digital rights group EFF and independent antivirus testing firm AV-Comparatives, evaluated 13 leading mobile security products against 17 real-world stalkerware samples. Malwarebytes emerged as the only solution to detect 100% of the test cases. Bitdefender, ESET, Kaspersky, and McAfee followed closely, each achieving a 94% detection rate.
In contrast, Google Play Protect, Android’s built-in security solution, detected just 53% of samples, the lowest score of all products tested. Trend Micro and G Data also underperformed, with detection rates of 59% and 65%, respectively.
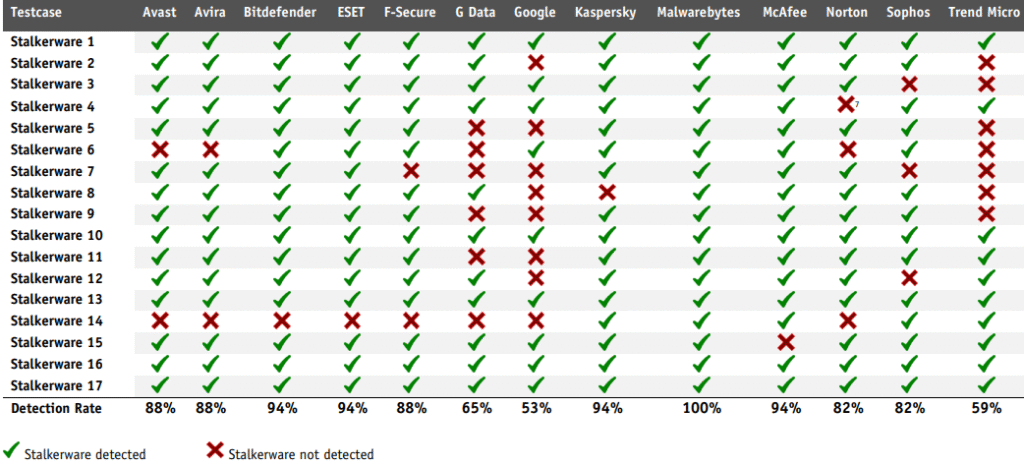
AV-Comparatives
The 2025 test reflects improved detection rates compared to similar tests in 2020 and 2021. However, AV-Comparatives warns that generic threat labeling and inadequate user notifications remain widespread, potentially leaving victims unaware of what kind of threat they’re facing, or how to safely respond.
Of the 17 apps tested in this round, many were found to be repackaged versions of the same underlying codebase, evidence of a shrinking but still persistent ecosystem. The researchers suggest this decline in diversity could be linked to regulatory pressure or the rise of physical trackers like Apple AirTags, which are increasingly used in stalking scenarios.
Crucially, the test did not simply measure whether stalkerware was detected, but also evaluated how each product reported threats. Clear, contextual warnings can help victims understand the danger, while generic alerts like “Potentially Unwanted Application” or “Threat Detected” fail to convey the severity of the risk. Only a few products explicitly labeled threats as stalkerware or explained their capabilities. Kaspersky was the only app tested to warn users that immediate removal could alert the abuser, a key safety consideration that remains overlooked by most vendors.
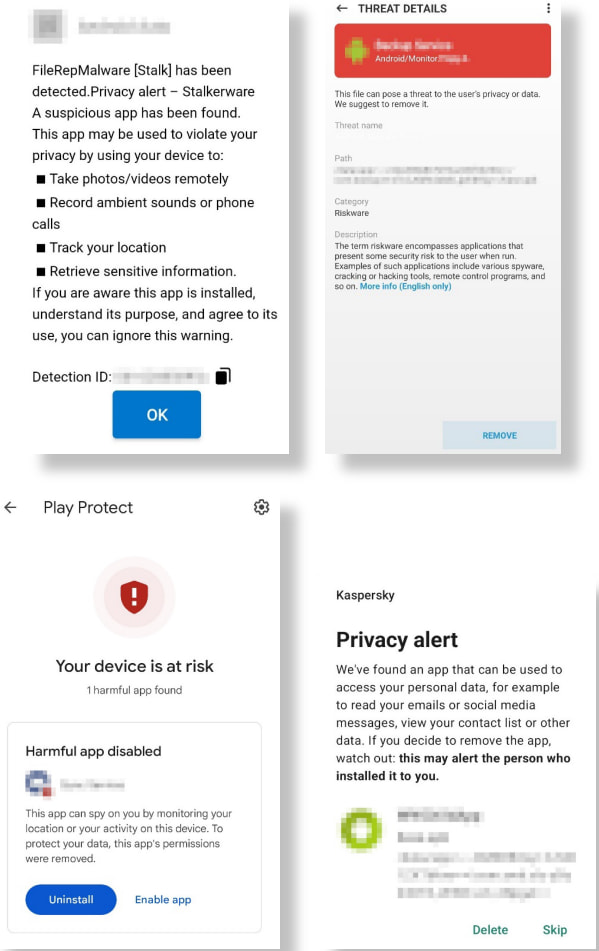
AV-Comparatives
While none of the apps removed stalkerware automatically (a positive, as this could provoke retaliation), the lack of secure notification channels, such as out-of-band alerts via email, poses another risk. In situations where the abuser monitors the victim’s screen activity, in-app alerts could inadvertently tip them off.
If you’re at risk of stalkerware attacks, consider using a mobile security app with proven detection capabilities, and do not rely on Android’s default Play Protect system.







Leave a Reply