
Cloudflare has autonomously mitigated the largest recorded DDoS attack in Internet history, absorbing an unprecedented 22.2 terabits per second (Tbps) and 10.6 billion packets per second (Bpps) in malicious traffic.
The attack, which lasted just 40 seconds, marks a new peak in the escalating trend of hyper-volumetric denial-of-service operations targeting core infrastructure.
Cloudflare announced the incident on X, emphasizing that the traffic volume was twice as large as any previously recorded DDoS event. Cloudflare’s autonomous mitigation systems detected and neutralized the attack in real-time, preventing disruption to the targeted services.
While the company has not yet released attribution details, this attack follows a similar event earlier this month, where Cloudflare mitigated an 11.5 Tbps attack later linked to the AISURU botnet, a sophisticated DDoS and proxy network believed to control over 300,000 infected devices globally. Whether the new, larger attack is a continuation of AISURU’s activity or the emergence of a new botnet remains unclear.
The previous record-setting DDoS assault, which occurred in early September, was traced by XLab researchers to AISURU. The botnet leverages mass exploitation of routers and embedded systems to launch massive traffic floods, often including complex multi-vector payloads and proxy capabilities. AISURU’s infrastructure has been steadily evolving, with recent reports highlighting its transition toward monetized proxy services, alongside traditional DDoS protection.
Cloudflare, a San Francisco-based web infrastructure and security company, provides CDN, DNS, and DDoS protection to millions of internet properties, including some of the most high-traffic and politically sensitive sites globally. Its network routinely absorbs hundreds of smaller-scale DDoS attacks daily, but the sheer magnitude of this latest incident represents a new frontier in volumetric assault capability.
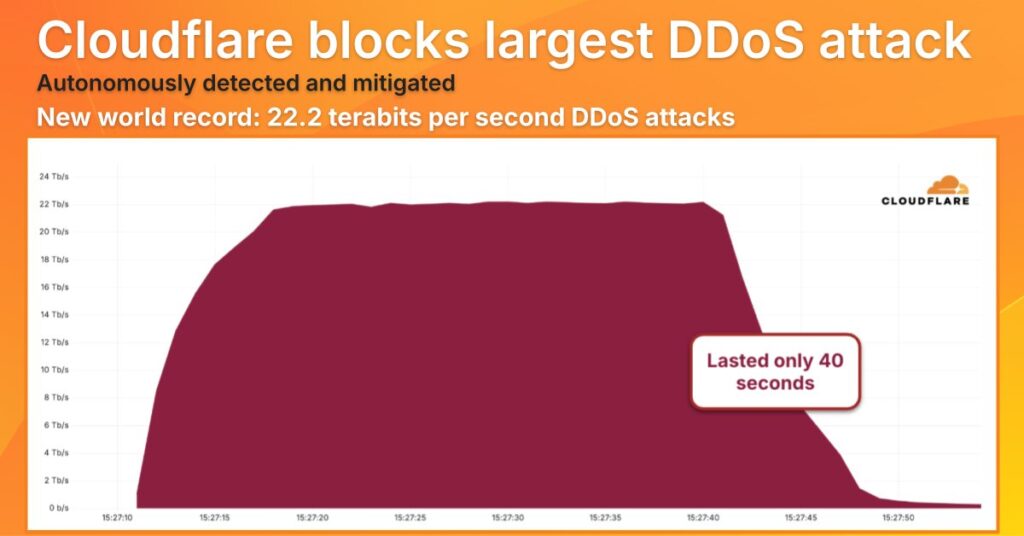
The attack curve shared by Cloudflare shows a sharp climb to over 22 Tbps, sustained for roughly 35 seconds before dropping abruptly, indicating a concentrated flood from highly coordinated infrastructure. While short-lived, the bandwidth required to launch such an attack far exceeds the capacity of most traditional mitigation providers, raising concerns about the growing weaponization of high-throughput residential or compromised enterprise devices.
Given AISURU’s known use of compromised routers from vendors such as Totolink, Cambium, Zyxel, and others, it remains plausible that the same network is behind this latest surge.
Users are advised to keep their router firmware updated, replace EoL devices with supported models, change the default admin credentials, and disable WAN access and remote administration unless explicitly needed.







Leave a Reply