
Google has expanded its Android 16 Advanced Protection Program to bring stronger, Chrome-specific security enhancements to high-risk users, including journalists, public officials, and activists.
The new capabilities, available starting with Chrome 137, tighten web protections at the browser level by default, further hardening devices already enrolled in Advanced Protection.
The enhancements were detailed in a blog post by Chrome’s Security Team, and follow the broader introduction of system-level Advanced Protection announced back in May 2025. While the program initially focused on securing Android devices from physical and app-layer threats, the latest update shifts focus to the browser layer, offering safeguards that defend against sophisticated web-based exploitation techniques.
Advanced Protection on Chrome for Android integrates three key security mechanisms:
- Always Use Secure Connections: This setting enforces HTTPS across all websites and prompts the user before allowing any connection over plaintext HTTP. This minimizes exposure to man-in-the-middle attacks and web-based injection techniques, especially on insecure networks like public Wi-Fi. Chrome had already begun rolling this out quietly for Incognito Mode and select scenarios since version 127 in June 2024. Now, it's enabled by default under Advanced Protection across all browsing contexts.
- Full Site Isolation: On Android devices with 4GB of RAM or more, Chrome now runs each website in its own process, matching the desktop-grade Site Isolation model. This change means that even if a malicious site successfully exploits a rendering bug, it cannot access data from other sites without breaching a second layer of isolation. Previously, this level of isolation on Android only applied when a user logged into or submitted a form on a site.
- Reduced JavaScript Attack Surface: Advanced Protection disables V8’s high-level JavaScript optimizers in Chrome, eliminating a major source of browser exploits. While these optimizations improve performance, they have historically accounted for around half of all exploited V8 bugs. Chrome users enrolled in Advanced Protection now sacrifice some performance for a significant gain in exploit resistance.
What is Advanced Protection?
Google’s Advanced Protection Program was originally launched to provide elite-tier security to individuals most likely to be targeted by sophisticated attackers. In Android 16, it evolved into a system-level toggle that applies stronger protections across the OS, including tamper-proof intrusion logging, restricted USB access, and forced use of Play Protect.
Advanced Protection is available to any Android 16 user with Chrome 137+ but is especially recommended for those in high-risk roles. It requires enrollment in Google’s broader Advanced Protection Program, which mandates the use of phishing-resistant two-factor authentication and automatically applies device-level protections.
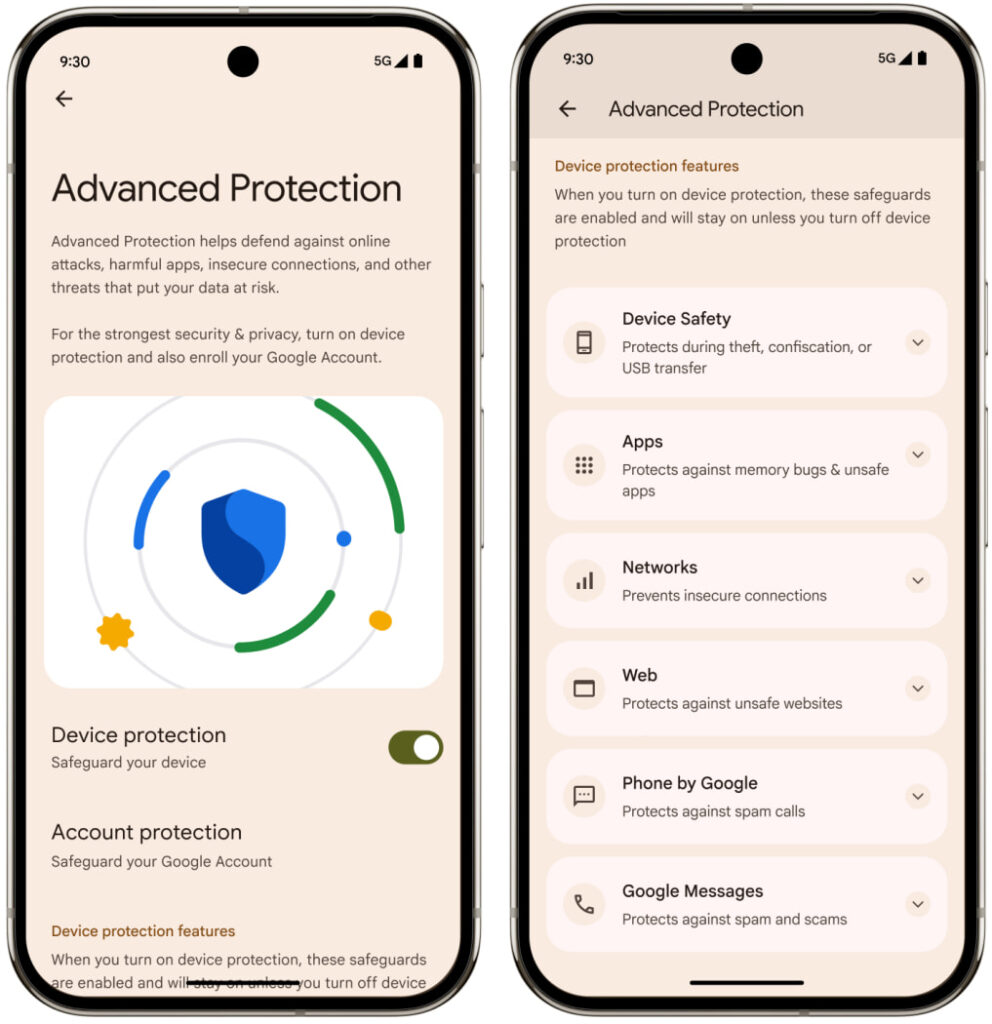
Chrome’s new enhancements further expand this defense model to the browser layer, which remains a common vector for targeted attacks.
While these protections are automatically applied under Advanced Protection, Google has also made each feature configurable for enterprises and tech-savvy users.
At-risk users are strongly encouraged to enable Advanced Protection through their Google Account, which will cascade the system-level and Chrome-specific defenses to any supported Android 16 device. Enterprises managing fleets of mobile devices should review Chrome’s updated enterprise policies to selectively enable the strongest settings for high-risk personnel.
For everyone else, enabling HTTPS-Only Mode and JavaScript hardening can offer substantial security benefits, especially when traveling or accessing sensitive content over potentially compromised networks.







No