
Security researchers from Kobe University have uncovered a critical vulnerability in the automatic pairing features of commercial Bluetooth devices, enabling attackers to silently hijack connections and impersonate trusted devices without any user interaction.
Dubbed “Stealtooth,” the attack can overwrite Bluetooth link keys and even perform man-in-the-middle (MitM) interceptions using only off-the-shelf hardware.
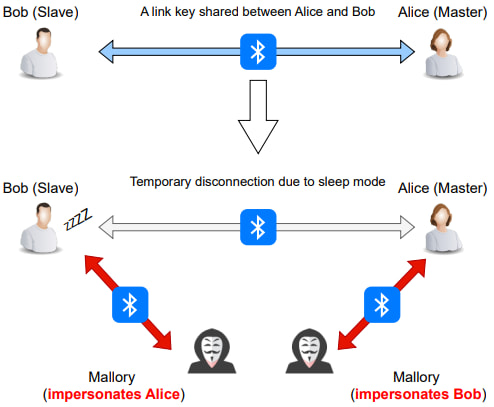
The attack was developed and demonstrated by Japanese researchers, exposing a major oversight in how many Bluetooth audio devices, such as headphones and speakers, manage automatic reconnections. Specifically, when these devices cannot find a previously paired device, they silently enter pairing mode, allowing an attacker to step in and overwrite the link key used to authenticate future sessions.
arxiv.org
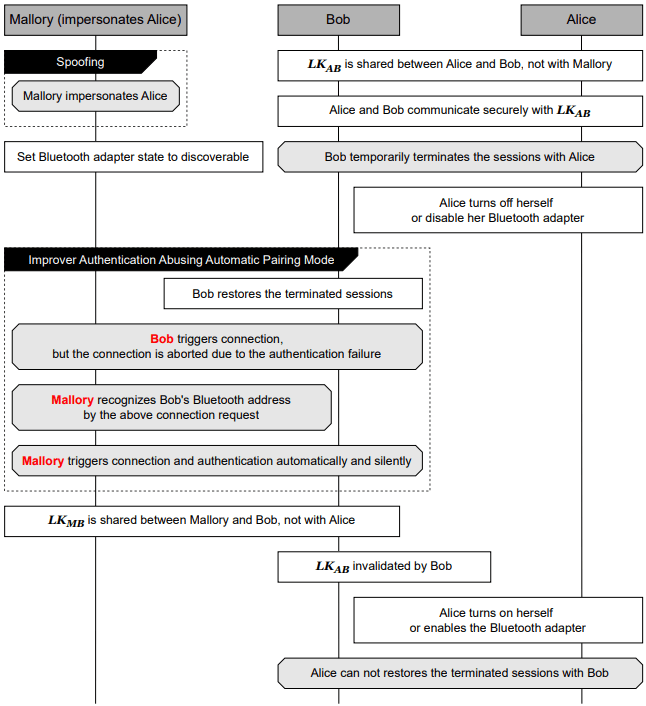
To execute Stealtooth, an attacker impersonates a previously paired device by spoofing its Bluetooth name and MAC address. If the legitimate device is powered off or out of range, the target device (e.g., a headset) may automatically attempt to reconnect and, failing that, pair with the attacker, without alerting the user or requiring any input. This link key overwrite locks out the legitimate device and gives the attacker full control over the connection.
arxiv.org
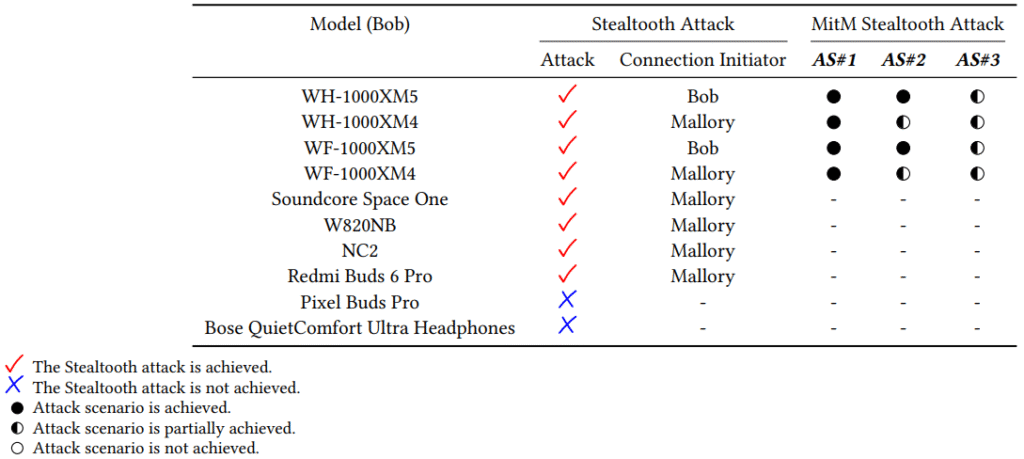
The vulnerability was tested on 10 commercial Bluetooth audio devices, including models from Sony, Anker, Xiaomi, Google, and Bose. Eight of the ten were vulnerable to the Stealtooth attack. In four of those cases, the researchers escalated the attack into a full MitM setup, intercepting and tampering with audio data using an extended technique called “MitM Stealtooth,” which combines Stealtooth with another attack called Breaktooth. This technique abuses Bluetooth's sleep mode to hijack sessions during temporary disconnections without any need for jamming or user action.
For the MitM attack, the team implemented custom tools based on BlueZ and PulseAudio, running on Raspberry Pi 4 devices to impersonate the victim devices. These tools were capable of capturing, relaying, or altering audio streams over the A2DP profile, demonstrating both eavesdropping and data injection in real-world conditions.
Among the tested devices, Sony's WH-1000XM5 and WF-1000XM5 were notably vulnerable to both the Stealtooth and MitM Stealtooth attacks. The Google Pixel Buds Pro and Bose QuietComfort Ultra, by contrast, resisted all attack scenarios.
arxiv.org
What makes Stealtooth particularly dangerous is its stealth: users receive no pairing notifications, and attackers require no privileged access or protocol manipulation. This low barrier to entry significantly expands the threat model for Bluetooth, especially in public or semi-private spaces where attackers can operate within range.
Mitigating this threat is the responsibility of manufacturers of Bluetooth devices, who should enforce user-visible notifications whenever a device enters automatic pairing mode or accepts a new pairing. Also, the Bluetooth standard should introduce mechanisms to cryptographically validate pairing legitimacy and restrict link key replacement without proper verification.
The researchers responsibly disclosed their findings to affected vendors. Sony has already released patches for several impacted models, so users should upgrade their firmware to the latest version to benefit from these security fixes.





Leave a Reply