Since 2023, the Chinese state-backed Advanced Persistent Threat (APT) group Salt Typhoon has conducted extensive cyber-espionage campaigns targeting critical industries globally. Leveraging new backdoors such as GHOSTSPIDER, SNAPPYBEE, and MASOL RAT, the group has infiltrated over 20 organizations across industries like telecommunications, technology, and government, aiming to exfiltrate sensitive information and maintain persistent access.
Salt Typhoon’s campaigns align with broader espionage patterns attributed to Chinese state-sponsored hacking groups. These groups focus on intercepting sensitive communications and exploiting telecom infrastructure to gather intelligence. Recent attacks on U.S. and Southeast Asian telecom providers highlight a trend of targeting critical communications systems to facilitate state-level intelligence collection.
For example, a T-Mobile breach in November 2024, while intercepted early, bore hallmarks of reconnaissance operations aiming to penetrate deeper network layers—a tactic associated with Salt Typhoon and Earth Estries.
Discovery and operations
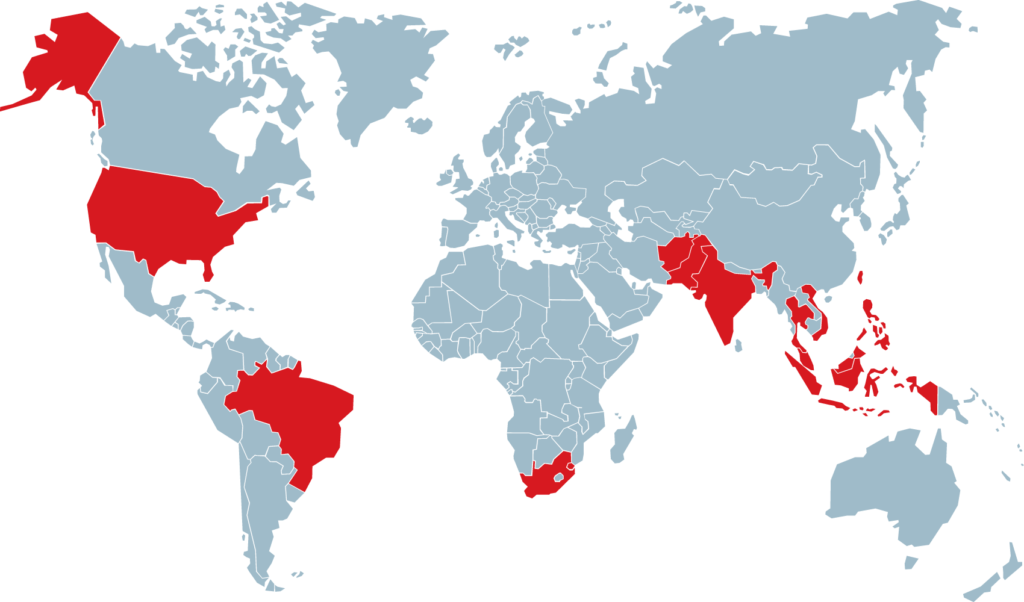
The Salt Typhoon group was identified through a detailed investigation by Trend Micro, who tracks them as ‘Earth Estries.’ The group has been active since at least 2020 but escalated its operations in mid-2022. Its targets span the United States, Southeast Asia, South Africa, the Middle East, and South America, with a strong focus on telecommunications providers and government entities.
The group exploits vulnerabilities in public-facing servers, including Ivanti Connect Secure VPN (CVE-2023-46805), Fortinet FortiClient EMS (CVE-2023-48788), Sophos Firewall (CVE-2022-3236), and Microsoft's ProxyLogon vulnerabilities. After gaining access, Earth Estries employs living-off-the-land binaries (LOLBINs) like WMIC.exe and PSEXEC.exe to move laterally across networks, deploy malware, and establish long-term espionage footholds.
Trend Micro
Target profile and tactics
Salt Typhoon has targeted organizations across industries, including:
- Telecommunications: Southeast Asian companies are among the primary victims, with attackers compromising edge devices and moving into cloud environments.
- Government: Agencies in regions such as Taiwan, Thailand, the Philippines, and Afghanistan have been infiltrated, focusing on data related to military and policy decisions.
- Non-Governmental Organizations (NGOs): Attackers also target entities working with U.S. federal and military operations.
- Private Industry: Sectors like chemical manufacturing, technology, and consulting have seen breaches aimed at gathering industrial intelligence.
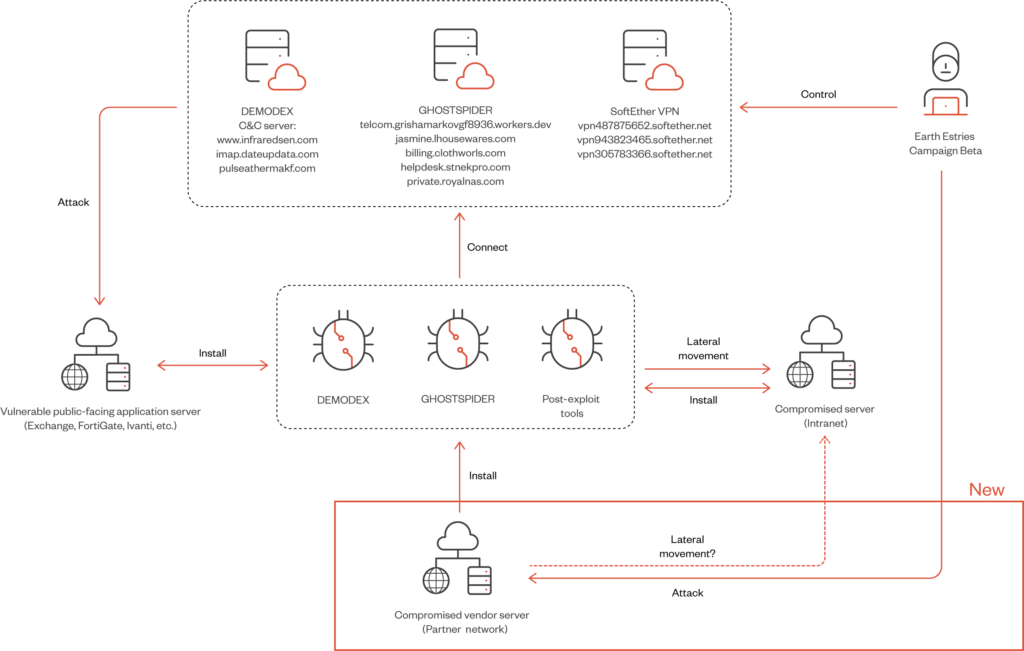
The attackers are well-coordinated, with distinct teams managing campaigns and infrastructure. Their command-and-control (C&C) systems are sophisticated, with unique configurations to avoid detection. Overlaps in tactics and tools, including shared malware like SNAPPYBEE, suggest that Earth Estries may benefit from malware-as-a-service (MaaS) offerings common among Chinese APTs.
Trend Micro
Custom backdoors and rootkits
Earth Estries employs a sophisticated and diverse set of tools, highlighting their technical prowess and adaptability in cyber-espionage operations. Their arsenal includes a combination of proprietary backdoors, rootkits, and modular malware, each designed for specific purposes in long-term infiltration campaigns.
GHOSTSPIDER:
A newly discovered backdoor, GHOSTSPIDER is a multi-modular malware that adapts to the target’s environment. Its architecture allows for dynamic deployment of individual modules, reducing its footprint and complicating detection. GHOSTSPIDER uses encrypted communications with its command-and-control (C&C) servers, employing a custom protocol secured by Transport Layer Security (TLS). This ensures stealth and reliable exfiltration of data. The backdoor’s modular design also enables attackers to update or deploy new functionalities as required, making it an evolving threat.
SNAPPYBEE (Deed RAT):
SNAPPYBEE, a modular backdoor frequently shared among Chinese APT groups, facilitates data collection, exfiltration, and persistence. Its compatibility with various operational contexts underscores Earth Estries’ collaborative ties with other threat actors, likely leveraging shared tools from malware-as-a-service (MaaS) platforms. SNAPPYBEE’s deployment often relies on DLL hijacking techniques to load malicious payloads stealthily.
MASOL RAT:
This cross-platform backdoor targets Linux servers, focusing on Southeast Asian government networks. Initially discovered in 2020, its recent resurgence in Earth Estries’ operations demonstrates the group’s commitment to maintaining access to critical systems over years. MASOL RAT includes encrypted payload delivery mechanisms, enabling it to evade traditional network monitoring tools.
DEMODEX Rootkit:
DEMODEX represents Earth Estries’ emphasis on stealth. This rootkit incorporates anti-analysis techniques like control flow flattening to obfuscate its code and evade detection. It is frequently deployed through LOLBINs (living-off-the-land binaries) such as WMIC.exe and PSEXEC.exe. The rootkit is often used in vendor networks to exploit trust relationships and gain deeper access into targeted systems.
Living-Off-The-Land Binaries (LOLBINs):
Beyond custom malware, Earth Estries heavily relies on native tools such as PowerShell, WMIC.exe, and PSEXEC.exe for lateral movement and privilege escalation. These LOLBINs blend into legitimate system operations, making them harder for traditional antivirus tools to detect.
This arsenal demonstrates Salt Typhoon’s ability to maintain stealth and persistence while tailoring their tools to specific targets. The group’s reliance on shared and proprietary malware, combined with sophisticated operational methods, signals their high level of coordination and resource access within the larger ecosystem of state-backed cyber-espionage.







Leave a Reply