
The Quad7 botnet, also known as the 7777 botnet, has been under investigation by Sekoia.io, revealing its reliance on compromised TP-Link routers to relay password-spraying attacks against Microsoft 365 accounts.
On October 19, 2023, independent researchers Gi7w0rm and Dunstable Toblerone published a blog post uncovering the Quad7 botnet associated with TCP port 7777 on compromised devices.
The botnet uses Socks5 proxies on these devices to conduct slow brute-force attacks against Microsoft 365 accounts globally.
Sekoia
In-depth investigation
The initial discovery prompted Sekoia.io to delve deeper into the Quad7 botnet. Sekoia.io detected Quad7's attacks on 0.11% of monitored Microsoft 365 accounts. The investigation revealed that Quad7 operators use compromised TP-Link routers to relay password spraying attacks, suggesting a focus on business email compromise (BEC) rather than advanced persistent threats (APT). However, the exact exploits used to compromise these routers remain unidentified, leaving room for further exploration.
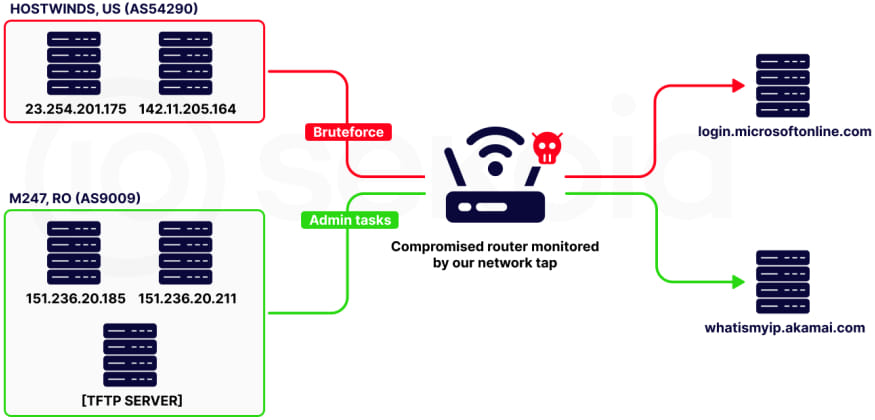
The investigation involved extensive monitoring of a TP-Link WR841N router, known for its vulnerability to Quad7. A Raspberry Pi connected via UART served as a network tap, allowing real-time forensic analysis. This setup enabled the identification of several suspicious activities, including brute force attempts and exploitation of known vulnerabilities.
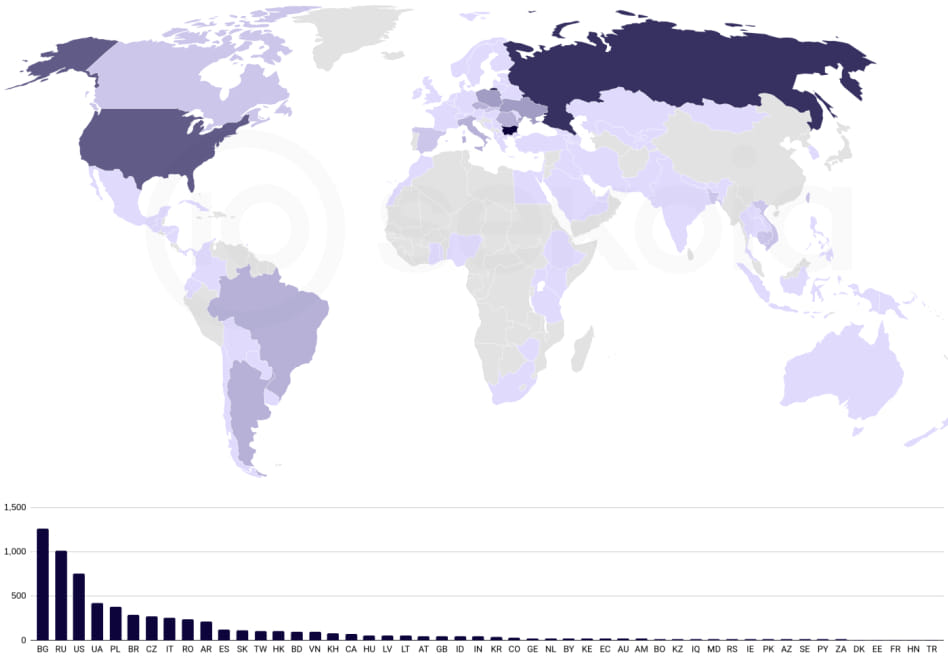
Despite the comprehensive monitoring, several aspects of Quad7's operations remain elusive. The botnet's geographical distribution, predominantly affecting Bulgaria, Russia, the US, and Ukraine, raises questions about its targeting strategy. Additionally, the botnet's infrastructure, characterized by insecure architecture, suggests potential for hijacking by other threat actors.
The Quad7 botnet primarily utilizes the Socks5 proxy for password-spraying attacks on Microsoft 365 accounts. Analysis of network captures revealed 912 connections to Microsoft's login services, indicating a systematic yet slow approach to brute force attacks. The attackers also utilized specific IP addresses and servers to check the proxy status and issue commands via the xlogin bind shell.
Sekoia
Defending against Quad7
Sekoia.io's efforts to identify victims in France led to the physical recovery of compromised routers, providing further insights into Quad7's operations.
Users should take the following measures to protect themselves from Quad7 and similar threats:
- Restrict remote administration of edge devices to specific IP addresses or disable web admin panels.
- Change default admin account passwords and use something strong and unique.
- Ensure the routers are updated with the latest firmware.
- Monitor authentication attempts from edge devices to internal servers.
- Deploy specific detection rules for Entra ID and Microsoft 365 logs to identify suspicious activities.







Leave a Reply