
Trend Micro's threat hunting team has uncovered a new Linux variant of the Play ransomware, specifically targeting VMware ESXi environments, marking a significant shift in the group's tactics.
The discovery highlights the group's evolution since first being detected in June 2022. The Play ransomware group, previously noted for their double-extortion tactics and custom-built tools, is now expanding their reach to Linux platforms, increasing their potential victim pool and monetization opportunities.
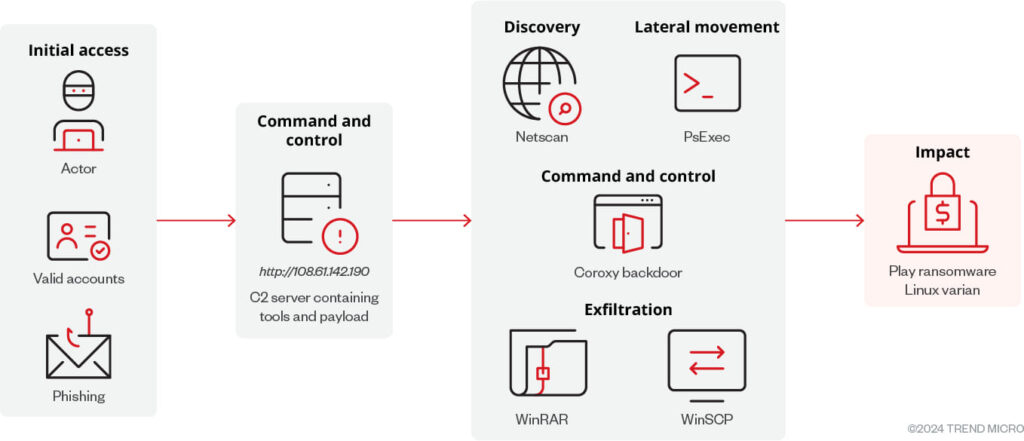
This new variant verifies its execution environment, targeting only ESXi systems before performing its encryption routines. Trend Micro researchers found it compressed with its Windows counterpart in a RAR file hosted on a suspicious URL. They note that the new variant has managed to evade detection on VirusTotal so far.
VMware ESXi environments are crucial for businesses due to their role in running multiple virtual machines that host critical applications and data. Compromising these environments can lead to significant operational disruptions, including the encryption of backups, which hampers data recovery efforts.
Trend Micro
Technical details
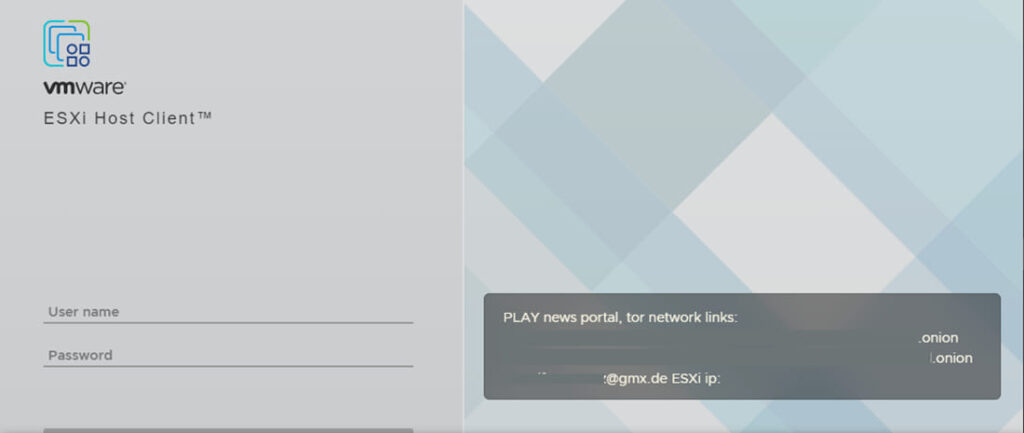
The Linux variant employs specific ESXi-related commands to disable virtual machines before encryption. Commands like vim-cmd and esxcli are used to power off VMs and set custom welcome messages on the ESXi host. Once operational, the ransomware proceeds to encrypt VM disk, configuration, and metadata files, appending the “.PLAY” extension to affected files and dropping a ransom note in the root directory.
Trend Micro
The Linux variant's command-line arguments are similar to those of its Windows counterpart, and it has functionalities to encrypt specific drives, folders, or network-shared resources.
Connection to Prolific Puma
Trend Micro's investigation also revealed connections between the Play ransomware group and the Prolific Puma group. Prolific Puma is known for providing infrastructure and services to other cybercriminals, utilizing domain generation algorithms (DGAs) for their operations. The IP addresses and domains associated with Play ransomware overlap with those used by Prolific Puma, suggesting a collaborative effort.
Mitigation strategies
To mitigate the risks posed by such ransomware attacks, organizations should implement the following best practices:
- Ensure ESXi environments and associated software are up to date.
- Apply security measures at the network level to protect vulnerable systems.
- Regularly audit and correct misconfigurations within ESXi environments.
- Use multifactor authentication and restrict administrative access.
- Limit the spread of ransomware by segregating critical systems.
- Disable unnecessary services and protocols, and implement strict firewall rules.
- Maintain and test secure backups stored offline.
The potential collaboration with groups like Prolific Puma amplifies Play ransomware's capabilities, making it imperative for organizations to bolster their defenses. Regular updates, robust access controls, and vigilant monitoring are crucial in mitigating the risk of ransomware attacks.







Leave a Reply