
ESET unveiled that despite major disruptions to its network and an arrest of a core operator, the Ebury malware, an OpenSSH backdoor and credential stealer, is far from inactive.
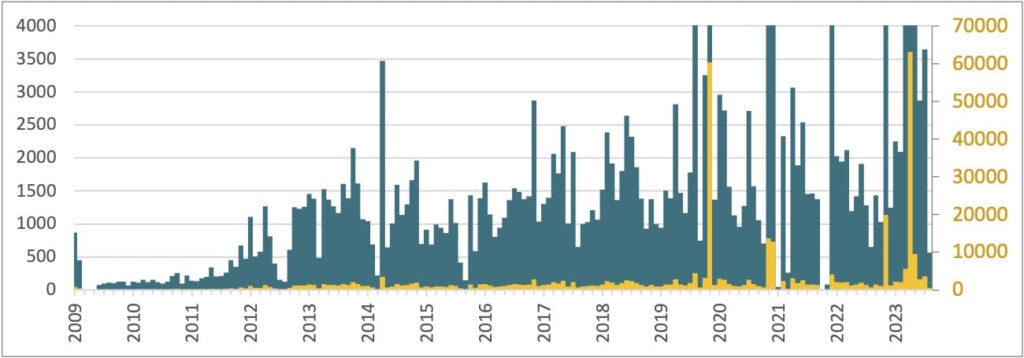
On the contrary, Ebury has adapted and continued to thrive, compromising approximately 400,000 servers globally to facilitate extensive financial theft through cryptocurrency and credit card fraud.
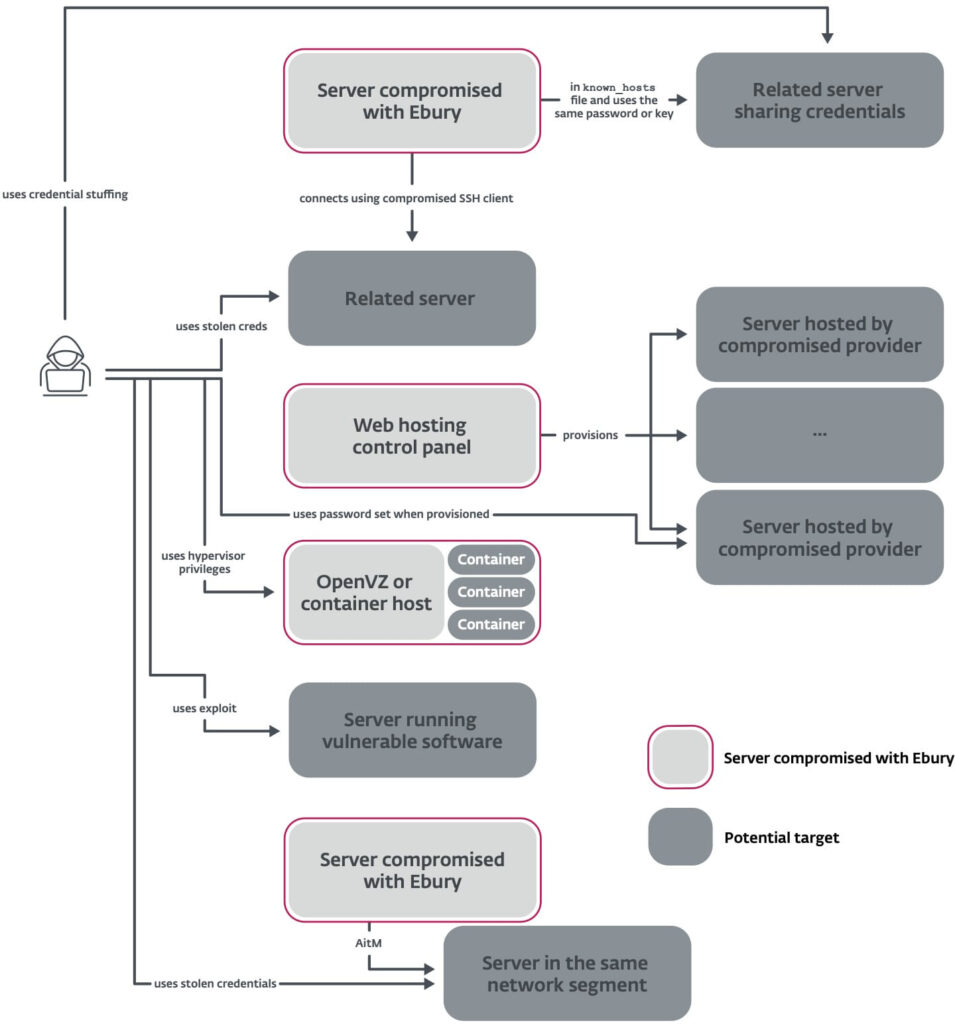
Ebury, which has been operational since at least 2009, manipulates Linux-based servers to steal credentials, facilitate cryptocurrency theft, and intercept financial transactions. Over the years, the malware has evolved, leveraging sophisticated techniques such as hypervisor-level attacks and the compromise of hosting providers to spread across systems.
ESET
Notably, Ebury's reach extended significantly due to a major U.S.-based hosting provider breach in 2019, which resulted in around 2,500 physical and 60,000 virtual servers being compromised.
ESET
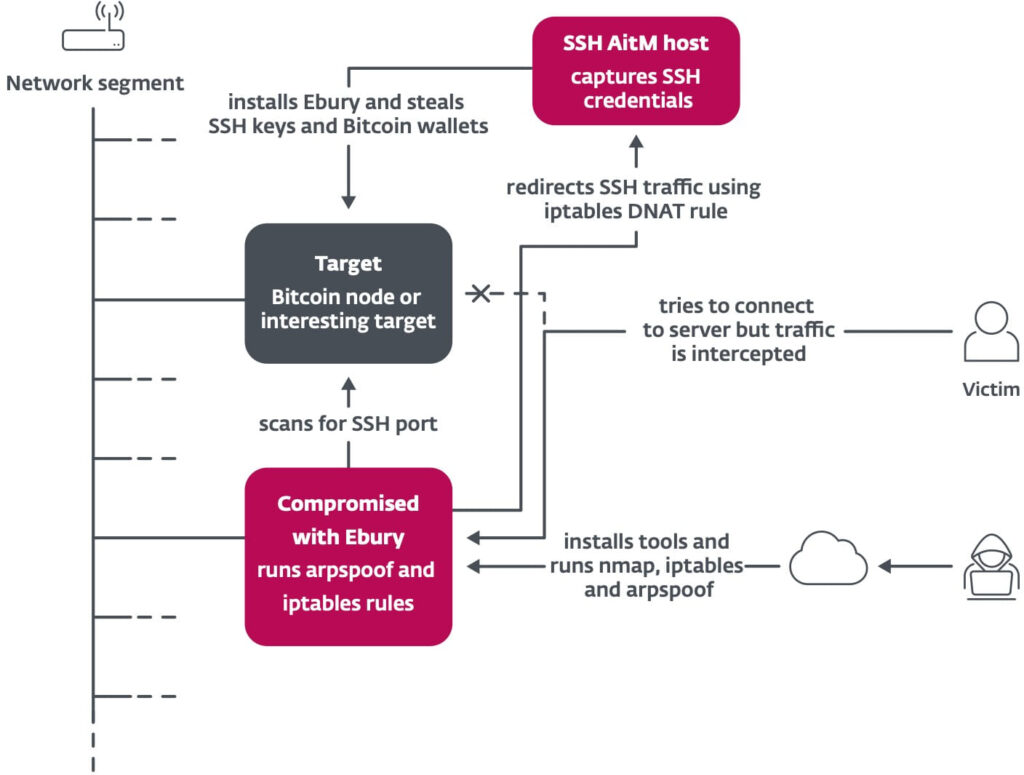
The attackers behind Ebury have also developed and deployed several auxiliary malware families. These include malicious Apache and Nginx modules and a Linux kernel module, which engage in activities like web traffic redirection, spam distribution, and sensitive data exfiltration. The malware notably masks its network traffic to evade detection and administers payloads without alerting system administrators.
ESET
Ebury follows diverse monetization strategies, including:
- Captures financial data like credit card details and cryptocurrency wallets from compromised servers.
- Collects and sells credentials, especially SSH keys, on the dark web or uses them to compromise more systems.
- Redirects web traffic to fraudulent or malicious sites for advertising fraud or to spread more malware.
- Uses compromised servers to host botnets, phishing sites, or act as distribution points for other malware.
- Uses affected servers to proxy traffic for spamming or other illegal activities, helping cybercriminals anonymize their operations.
Victims of Ebury range widely from small enterprises to large ISPs, with no specific industry being more targeted than others. ESET's whitepaper presents on the methodologies used for the malware's propagation and maintenance, including the exploitation of zero-day vulnerabilities and credential-stuffing attacks.
In terms of defense, the cybersecurity firm recommends actions such as the utilization of multifactor authentication (MFA) for SSH access, stringent monitoring for signs of compromise, and adherence to comprehensive server management practices. Given the sophisticated nature of the attacks, ESET advises that recovery from Ebury infections often requires a complete system reinstallation to ensure all remnants of the malware are eradicated.
As of ESET’s latest estimate, about 100,000 servers globally are currently infected with the Ebury malware. This figure highlights the widespread impact of this malware across various networks and the significant challenge it poses for cybersecurity efforts.







Leave a Reply