
ReversingLabs researchers have uncovered a sophisticated malware campaign targeting the NuGet package manager, leveraging homoglyphs and IL weaving to inject malicious code and deceive developers.
ReversingLabs began tracking the campaign in early August 2023. Initially, attackers exploited NuGet’s MSBuild integrations with obfuscated downloaders inserted into legitimate PE binary files using a .NET technique called Intermediary Language (IL) weaving.
By October 2023, the campaign included over 700 malicious packages. Early attacks employed simple PowerShell scripts for malicious downloaders, which were easily detectable due to unusual install scripts and absence of legitimate functionality. These scripts would connect to an attacker-controlled C2 server to fetch second-stage malware.
The attackers soon evolved their tactics, exploiting NuGet’s MSBuild integration to insert malicious code into build tasks inside *.targets files. This ensured that the malicious code was executed every time the project was built. The attackers also employed sophisticated techniques to make their packages appear legitimate, including typosquatting, using icons from trusted packages, and inflating download counts.
Patching .NET binaries
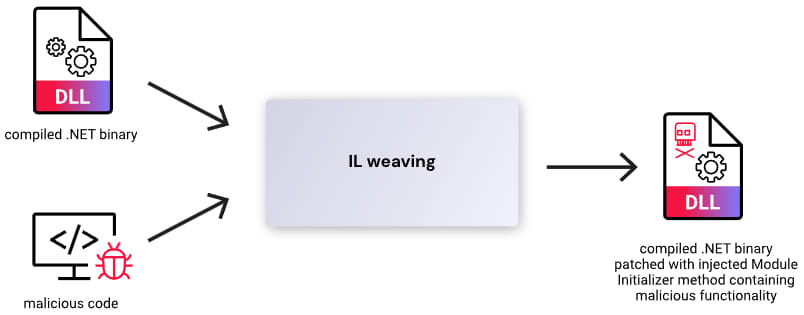
The campaign's latest phase involves the use of IL weaving to patch legitimate .NET binaries with malicious code. This method inserts a module initializer into a compiled binary, which is executed before any other code in the module. The attackers used tools like Mono.Cecil for MSIL (Microsoft Intermediate Language) compiling and decompiling, and Fody to simplify IL weaving.
ReversingLabs
The injected malicious code functions as a downloader for the SeroXen RAT, making the malware harder to detect compared to plaintext PowerShell scripts. The detection was further complicated because the malicious code was embedded in DLL files, which are not executed by default but called under specific circumstances.
Homoglyphs and typosquatting
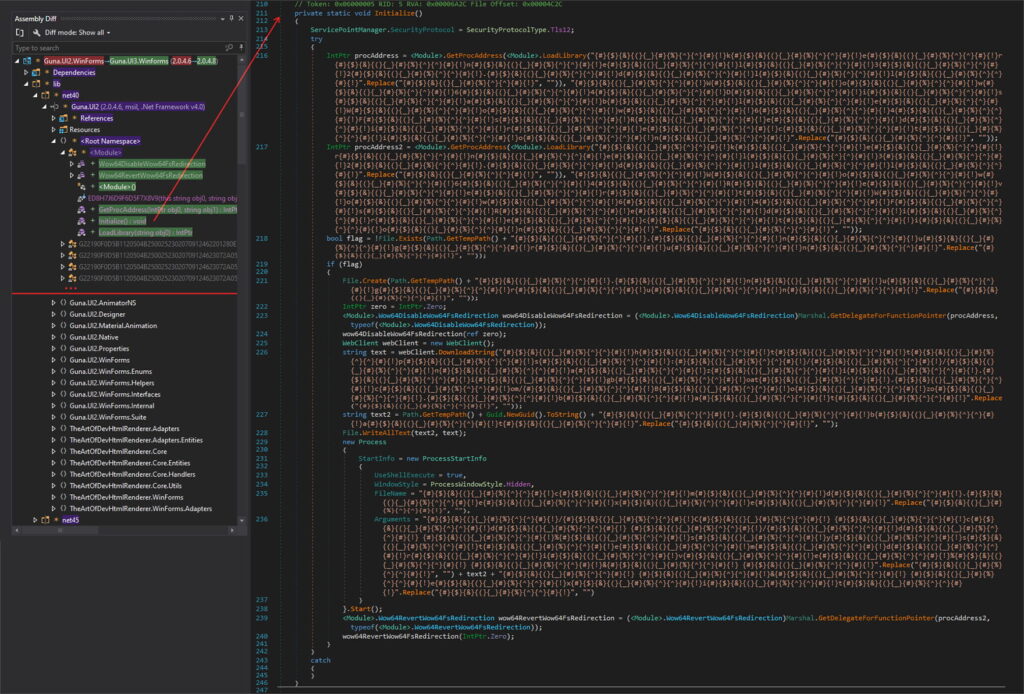
A notable technique used in this campaign involves exploiting homoglyphs—characters that look identical but have different digital identifiers. For example, the Latin “u” (\u0075) and Armenian “ս” (\u057D) appear identical to humans but are treated differently by computers. The attackers used these characters to create packages that mimicked reserved NuGet prefixes like “Guna.UI2.WinForms,” publishing them under names like “Gսոa.UI3.Wіnfօrms.”
This deception allowed the attackers to bypass NuGet’s security measures, which reserve certain prefixes for legitimate authors. ReversingLabs’ Spectra Assure platform was instrumental in identifying differences between the legitimate and malicious packages, revealing tampered .NET binaries with module initializers.
ReversingLabs
This campaign underscores the increasing sophistication of attacks on software supply chains. Malicious actors are continuously improving their techniques to evade detection, and defenders must evolve their strategies accordingly.






Leave a Reply