
State-sponsored actors have been found exploiting multiple zero-day vulnerabilities in Cisco's network devices, targeting critical government networks through a sophisticated espionage campaign dubbed “ArcaneDoor.”
Cisco Talos uncovered this alarming breach in a report today, revealing a complex web of intrusions and malware implementations aimed at perimeter network devices—key gateways for data inflow and outflow within networks.
Attack details
The initial detection of suspicious activity was flagged early in 2024 by a vigilant customer using Cisco's Adaptive Security Appliances (ASA). This prompted a joint investigation by Cisco's Product Security Incident Response Team (PSIRT) and the Cisco Talos group.
The collaborative effort, supported by several external intelligence partners, spanned months, eventually identifying a previously unknown actor, now tracked as UAT4356 by Talos and STORM-1849 by the Microsoft Threat Intelligence Center. This actor employed advanced espionage techniques, demonstrating an in-depth understanding of targeted devices.
The hackers, recognized as sophisticated due to their state-backed nature, deployed two primary malware tools, “Line Runner” and “Line Dancer.” These tools were used to manipulate device configurations, capture and exfiltrate network traffic, and potentially move laterally within networks. The investigation revealed that the intruders had developed and tested these capabilities since at least July 2023, with significant activity between December 2023 and January 2024.
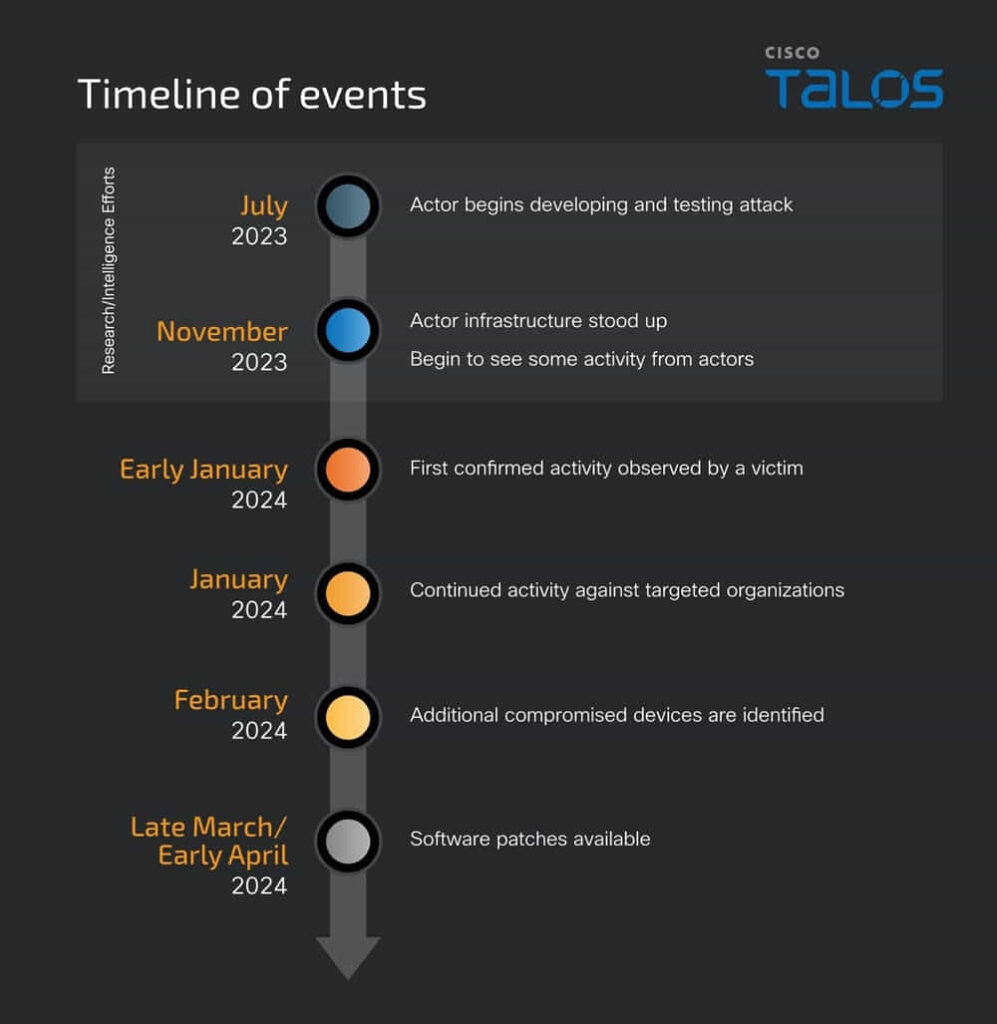
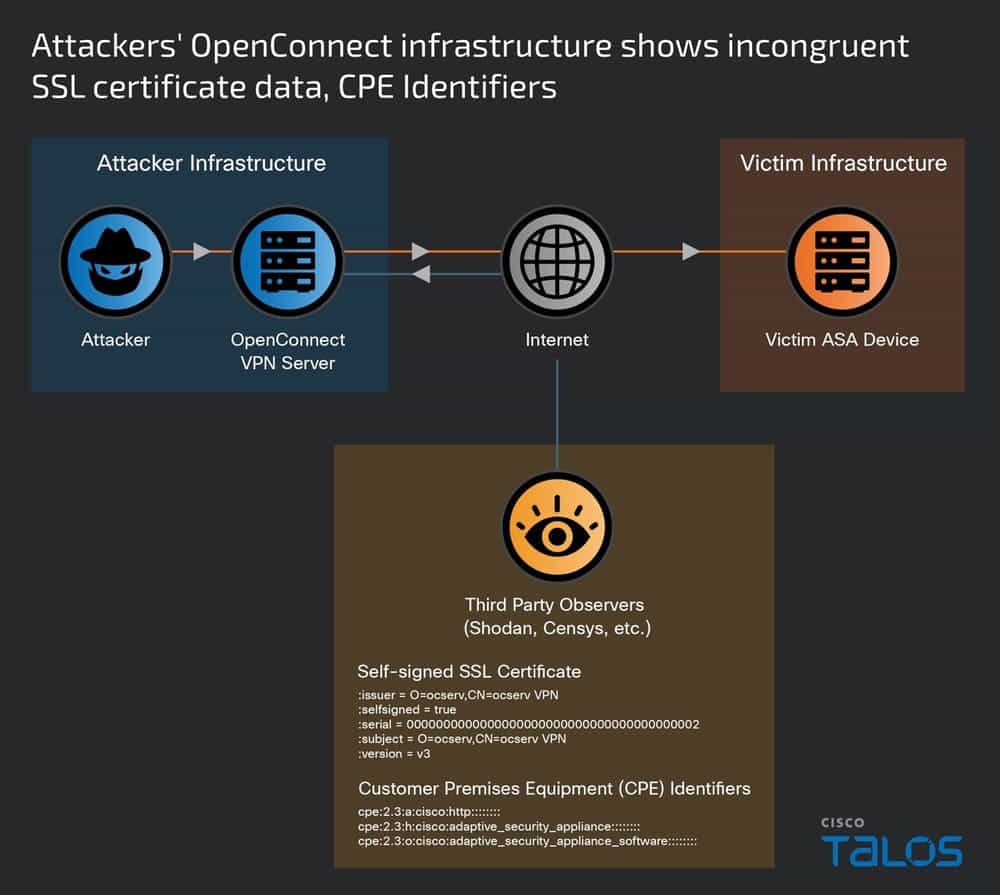
Two critical vulnerabilities were central to the attack—CVE-2024-20353 and CVE-2024-20359. These vulnerabilities allowed the attackers to implant custom malware and execute unauthorized commands across the compromised devices. Notably, the initial access vector for these intrusions remains unidentified, highlighting the stealth and sophistication of the attack methods.
Malware functionality
In the latest stages of the ArcaneDoor attacks, the threat actors deployed two malware families.
The first is “Line Dancer,” a memory-resident shellcode interpreter that enabled arbitrary shellcode execution without direct authentication, by manipulating the host-scan-reply field used in SSL VPN and IPsec IKEv2 VPN configurations.
The second is named “Line Runner” and is a persistent backdoor that utilizes the ASA's legacy script handling to maintain its presence through reboots and system upgrades.
The forensic analysis of the compromised devices presented significant challenges. The attackers had employed anti-forensic measures like hooking into and disabling the ASA's crash dump process and altering authentication mechanisms, complicating the collection of evidence and thwarting traditional forensic efforts.
Defense recommendations
Cisco has released patches for the identified vulnerabilities and detailed security advisories to help mitigate these threats. Organizations are advised to apply these updates promptly, ensure devices are properly patched, and maintain robust monitoring and authentication controls.
Special attention should be given to network devices, regardless of the manufacturer, as the threat actors have shown interest in a range of network equipment providers.
The sophisticated nature of the attack highlights the evolving capabilities of state-sponsored actors and the continuous threat they pose to global information security.







Leave a Reply