
ProtonMail is widely touted as the most secure and private email service in the world. Having tested and reviewed the service ourselves, we have been recommending ProtonMail for years. However, the company behind ProtonMail is now in hot water — and at least one of its users has been arrested.
What happened exactly?
Last weekend, news blew up about ProtonMail logging one of its users and providing IP address logs to French authorities. The ProtonMail user was subsequently arrested in France.
Note: ProtonMail has provided us with more clarification, stating that the location and identity of the suspect were already known to the police. The logs that ProtonMail provided helped the police to further build a case against the person, ultimately leading to his arrest.
The news gained traction first on Twitter, with various media outlets also picking up the story. The key evidence of what transpired behind closed doors was a court document detailing how ProtonMail provided IP address logs of its user to French authorities.
The backlash has been swift. But should we jump to condemn ProtonMail or is this type of situation inevitable with privacy services? Let's examine how ProtonMail responded to the situation and put it into context by comparing it to other cases where email and VPN services provided logs to authorities — as well as cases when they did not.
ProtonMail touts Swiss jurisdiction and privacy protection
We place a lot of trust in privacy services to do what they actually say. In the case of ProtonMail, they have boldly touted their privacy and security credentials for years. Not only have they claimed to not keep any IP logs by default, but they also regularly tout their Swiss jurisdiction, which allegedly confers legal independence.
Here is how ProtonMail advertises itself and its Switzerland jurisdiction.

So now let's compare the reality of this situation with ProtonMail's claims. We have learned that:
- Switzerland jurisdiction does not mean very much. Governments can simply go through a Swiss court and then ProtonMail will start logging any user that is requested by the court.
- The “extremely limited user information” is enough to find and arrest a ProtonMail user, with IP address and device info data.
It is also interesting how ProtonMail responded to this situation and the subsequent website revisions.
ProtonMail scrubs “we do not keep any IP logs” from its website… after IP logging incident
When a privacy service's claims do not line up with reality, trust is eroded and potentially lost forever. While trust is very subjective, ProtonMail's logging activities and subsequent website revisions have certainly raised some eyebrows.
Using the Wayback Machine, we can see that ProtonMail did some editing to its website in the wake of this logging incident.
Before the logging scandal:
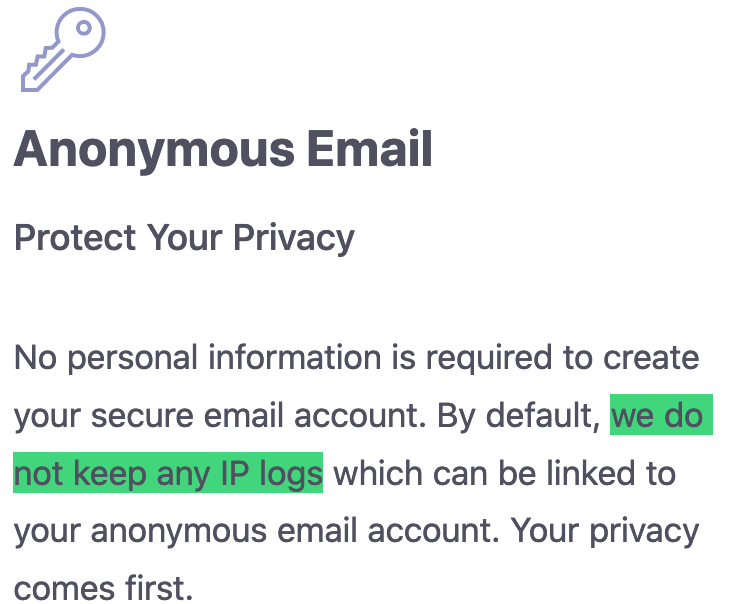
In the image above, you can see that the “we do not keep any IP logs” claim is prefaced with the “By default” at the beginning. Now, after the logging fiasco, the reference to not keeping IP logs is gone.
After the logging scandal:
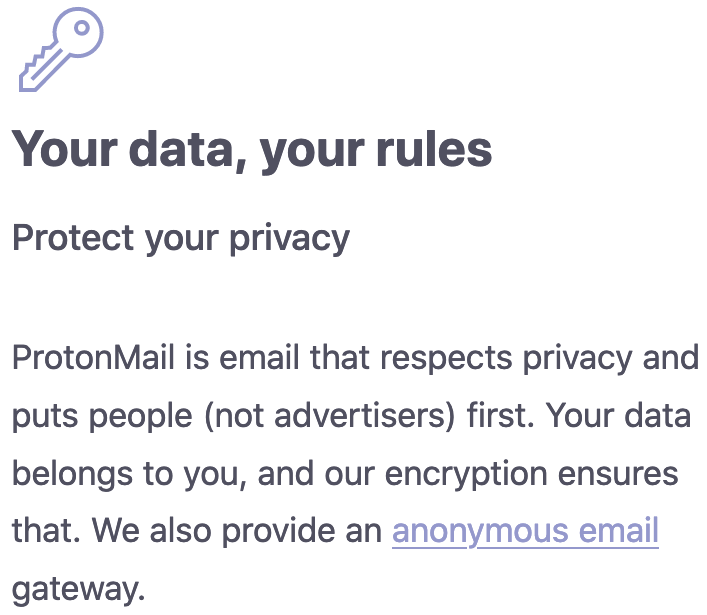
Gone is the claim, “we do not keep any IP logs which can be linked to your anonymous email account.”
In ProtonMail's defense, it does not seem like anything changed. Technically, they probably did not keep any IP logs by default — but that is the key distinction. With just one quick request through a Swiss court, however, an outside government or agency could quickly get all the logs they needed to find and arrest the ProtonMail user they're looking for. Case closed.
You can read ProtonMail's response to the situation here.
Not the first time ProtonMail has logged users
We should also point out that ProtonMail has logged users in the past when ordered to be a Switzerland court. This is detailed on the Transparency Report here.

ProtonMail's Transparency Report shows numerous cases where they have complied with various court requests for user data.
And similar to the current logging case, ProtonMail did some major site revisions by changing the wording of the Transparency Report after some other cases came to light. This was first noted by Martin Steiger in Switzerland here.
Other email provider's that have bowed down to logging demands
Before you rush to condemn ProtonMail, you should understand the situation a bit more with some background information. For one, this is nothing new. We have been keeping a close eye on the privacy space for years now, and this is not the first time something like this has happened.
Riseup logs user data for US authorities
Riseup, which is an email and VPN provider based in the United States, was forced to comply with data requests a few years ago:
After exhausting our legal options, Riseup recently chose to comply with two sealed warrants from the FBI, rather than facing contempt of court (which would have resulted in jail time for Riseup birds and/or termination of the Riseup organization).
There was a “gag order” that prevented us from disclosing even the existence of these warrants until now. This was also the reason why we could not update our “Canary” [warrant canary that warns users about these events].
This appears to be similar to the ProtonMail situation, except that with ProtonMail, the goal was to identify the user with IP address logs.
Tutanota saves unencrypted emails for German authorities
A similar situation unfolded in 2020 with the German email provider Tutanota. In this case, Tutanota was required by a German court to log incoming and outgoing emails for a specific user identified in a German court order. This only affected unencrypted emails for a specific user, as Tutanota explained here.
However, all unencrypted emails that were sent and received by this user would have ended up with the German government, while encrypted emails would have been safely encrypted (and unreadable). The original article explains the case is in German here.
Similar to the ProtonMail case, this was a specific court order targeting one individual who was using Tutanota's service for (alleged) illegal activities. In other words, the courts did not force a blanket policy that affects all of the service\'s users.
When logging requests are denied (with VPNs)
When putting the current logging situation into context, it's also important to examine when logging requests are denied. We have written about different examples of this in our no logs VPN guide. This includes cases where ExpressVPN, Private Internet Access (PIA), and OVPN have all successfully denied government requests for user data.
As one example, we'll take a look at a recent case with OVPN, a Swedish-based VPN service that has successfully fought back against logging demands. The VPN was ordered by a court to log users who were accused of violating copyright laws by downloading movies. They were being sued by a group called the “Rights Alliance” on behalf of the movie industry.
Rather than comply with the request, OVPN lawyered up and went to court to fight for its users. And they won the case, proving that they are a truly no logs VPN service that takes their users\' privacy seriously.
To summarize the verdict, the Rights Alliance and their security experts have not been able prove any weaknesses in OVPN's systems that could mean that logs are stored. OVPN therefore wins the information injunction as our statements and evidence regarding our no log VPN policy have not been disproven. The movie companies also need to pay OVPN\'s legal fees which amounts to 108,000 SEK (roughly $12,300 at current exchange rate).
While the nature of an email service and VPN service are very different, this case does show that there are examples when privacy companies successfully fight back against demands for user data.
However, there are other VPNs that bow down and comply with these demands, as we have seen with PureVPN logging users for the FBI, as well as with IPVanish, which is based in the US.
Should people still use ProtonMail?
While this latest logging fiasco (and ProtonMail's website revisions) will probably shake many peoples' trust in the service, ProtonMail itself remains secure and private compared to most other options. With most free email services, such as Gmail and Yahoo, your inbox is wide open for data collection and advertising exploitation.
Conversely, ProtonMail keeps your inbox encrypted and secure at rest, without giving others access. Sure, they may be forced to log user IP addresses, but there is a simple solution for that (see below). Additionally, you can be certain that advertisers are not collecting the content of your inbox to hit you with targeted ads.
Nonetheless, if you now want to seek out alternatives to ProtonMail, see our guide on private and secure email services. We'll still be recommending ProtonMail because nothing has really changed. The same goes for Tutanota.
Be smart and always use a VPN (and other privacy tools)
We've said this before and we'll say it again. Everyone reading this should be using a VPN when going online. A VPN is simply basic protection that will hide your IP address and geographic location when you go online. This is something everyone needs in today's world of mass surveillance and tracking.
Had the ProtonMail user in question been using a good VPN, and also implementing basic OPSEC, he probably would never have been arrested. ProtonMail would have logged the user's IP address, but that would have only led investigators to a VPN server in some random data center, rather than the user in question.
In addition to using a secure browser and a VPN, we also recommend using a good ad blocker that can effectively block ads and trackers on all browsers. There is also the option to combine both VPN and ad blocker, which is especially effective in many circumstances, while also being easy to use. See our VPN ad blocker guide for additional information.
Consider using an encrypted messenger for really private communications
Lastly, this is a good opportunity to repeat another piece of advice that we have been saying for years:
If you really need privacy, don\'t bother using email. Instead, use a good encrypted messaging service.
Email is simply an outdated method of communication that is leaky and contains lots of private data. By contrast, there are some great privacy-focused encrypted messaging systems, from Signal to Telegram and Wickr. We have also been impressed with Session, which takes privacy to another level and keeps no metadata whatsoever.
Check out our guide on the best encrypted messaging services to learn more.







This is the nature of email services. Other email providers are surely doing the same thing. This doesn’t bother me too much, because I use a VPN and extra security with accounts that need it.
Don’t you get it, peoples? Protonmail + Tor (w/ User Switcher and Manager pick either Fedora or Linux or customizes to put “Guess what is my user agent?”, obfs4 bridge & NoScript) without VPN. Everything looks fine and work.
Is this still an issue? Your Dec 1, 2023 round up of recommended secure email services lists them, and mentions that they strip IPs from emails. Is that something they did to address this situation?
Yes, it’s still an issue.
https://cyberinsider.com/protonmail-data-requests-user-logs/
That said, we recommend using a good VPN service with any email provider to hide your IP address.
Proton mail also marking your emails as spam and asking human verification eveysingle decide or ip even with vpn so how’s that possible they are collecting more than you think fingerprint and iOS device profiles etc devices in your network so one of the big tech or government tell them spy on you they will obey like good dog that’s what they are!! Big tech dog… delete your proton mail asap never use this spy network again.. trust me.
If you want privacy and encryption for your Emails or Web Mail messages, You use an Email or Web Mail from the TOR Network or the Dark Net or the Deep Web. If you want privacy for your Internet connection, Use the OVPN Software or App or a VPN Software or App from the TOR Network or the Dark Net or Deep Web.
If you really want to claim ownership of your smartphone and do whatever you want with it , the first and foremost thing to do is to replace that over the counter ROM with custom one. You can download or even create one yourself if you have the necessary tools, a search for “custom ROM” will yield more details. Modern smartphones hardware can accomplish a lot of functions that some desktop computers if it weren’t for the stock ROM’s limitations. The developer of these stock ROMs seem to only interested in using the power of your smartphone hardware against you.
Who said anything about doing something illegal? Simply hate spamming & phising-go figure… Their “customer service” sucks. Paid member, yet, non-existent “customer service”! Read more articles, then, comments on this site! I’m NOT unique with this BIG problem!
Why do any of you think that you can do something illegal and not get caught by big brother?? We are being watched by the powers that be no matter where you think you can hide.
Problem is Big Brother is the be
Iggest crook out there.
Absolutely, the popo is corrupt to the core! No doubt in my mind. Im a former Governmental auditor.
Perfect Privacy VPN even successfully denied data government requests.
Not surprised-Snowden and all we won’t go into.
Besides the above article, where I only read the headline, bc I’m over it. Many people & I simply hate spamming & phising-go figure… Not looking to do anything illegal- not a new concept. Their “customer service” sucks. Paid member, yet, non-existent “customer service”! Read more articles, then, comments on this site! I’m NOT unique with this issue! Selling my info to bad players isn’t a good and ethical way to do business- the end.
You could view it as a lock for your door, any locksmith can pick it but you want to make it as hard/time consuming as you can.
In that regards the way of payment matters, as tracking through our centralised globalised banking network should be extremely efficient for a lot of partys.
You can only trust open source code if you can make sure that thats rly the code running, without additives, which would mean self hosting or enormous blockchaining.
Even through sure, a lot of attack vectors get hardened in contrast to proprietary software.
Disagree extremely hard, its a slow process, the more small chunks you give them the bigger the ones they can grab, with social acceptance, the next time.
Any step into any direction should be treated as a clear signal into a more and more fascist controlling government putting democracy into greater and greater risk cause the power gets more and more concentrated.
Open your history books, and watch what happened when single persons got able to grab over proportional amounts of power.
The human isnt a creature of wisdom, its manipulative af, you shouldn’t want to create/harden a leverpoint for centralised power of single partys.
We germans voted, wanted and loved Hitler. Thats one side of democracy. The dark “Ego” side. Please keep that in mind. The US isnt save from such phenomenons.
Keep in mind that there are a lot of voices saying TOR node network is infiltrated by a lot of different powerful interest groups, and the probability is high that you are routing through a chain of nodes from the same infiltrators and therefore lowering your security severely through tor.
But at least for journalists wanting to bypass smaller government surveillance from third world country’s its still an awesome tool i think!
You could be right . I’m from 3rd world country that doesn’t have a single Tor node and I don’t get alert mails noting a login from a different country if my exist Tor node is either and in most cases are from Germany or USA.
Thinking about it you can tell the source or destination of a network packet if your node is the entry or exist respectively and there are only 3 nodes in Tor circuits. But then again, Tor claims they can’t track our network traffic even if they want to them-self!
Vote for a government hardening democracy through knowledge and transparency or get into the fbi yourself. No other ways i see, NCA’s are a powerful tool.
In my view, ProtonMail obeying the court order in question was in line with their terms of service. There have been many more instances when they successfully fought off warrants but this case involved potential terrorism. That is not something a company like them (or anyone else) should ignore.
Here’s a radical idea, stop breaking the law or engage in illegal or criminal activities and then you won’t have the authorities snooping around, peering into your life.
Well the problem is that weird stuff is declared as suspicious by courts all over the world, with which they can than get legal search warrants for literally everyone, its just a game of perspectives.
So just the wrong party would need to get in charge, and they’ll have open doors fck1ng up everyone who they dont like.
Betraying the ground concepts of swiss jurisdiction wouldnt be hard for most bigger governments i think, so this means any protonmail user can easily get spied upon by any government the swiss “accepts”.
Something which isnt shocking, but needs to be communicated clearly and transparently.
Some dont break the law at all. Yet still wind up in jail, fines, lawyers, harrassment by law, and even worse, death penalty when its all said and done… But they were innocent the WHOLE TIME!! you trying to make it sound like its all good to sort through everybody shit to see if theres any terrorists using email addresses from Proton.
Which means you ALSO approve of any of law related men snooping on into EVERYBODYS emails from tutanota and the rest of the private mailboxes across the world. Just as long as some legal law man says “open it up I think theres a terrorist”, its all good to open flood gates of emails and every agency(corrupted or not) ALL go digging through ALL of the citizens of the worlds emails. You dont think the law, the gov’s behind their laws, the men involved, you think theyre ALL GOOD and none are CORRUPT or VINDICTIVE and never VIOLATE THEIR POWERS. you my boy r a sad site for the future of PRIVACY!
Hell, you just like them. I dont want everybody reading my mail before the mailman hands it to me. AND THEY NEVER USED TO! So how in tf is it ok to all of sudden read peoples mail now before they even get to look at it??! Freakin IDIOT. have a nice crap day, bozo.
I’m your local sheriff. I understand that you leave your door unlocked and you have no problem with me coming into your home unannounced and looking around, shuffling through your stuff, and taking pictures.
In canada peacefull truckers were called terrorists, those days in Ontario anyone who says Vaxx is bad can be called terrorist.
They weren’t peaceful protesters. They violated court orders to disperse, held weapons and threatened many people at the time. They exercised their rights to assemble in Ontario. But they refused to leave when legally ordered and they faced legal implications at that time.
If they can be legally ordered to disperse at the whims of an authority, then they never truly had the right to assemble, don’t you think?
Don’t advertise as having a private and secure service if it’s not.
IMO Protonmail is just another Hushmail. Anyone wh ohas been around for a long time remembers when Hushmail was forced to turn over in excess of 100K decrypted emails to the DEA. This was the first time I had ever heard of MLATs (Mutual Legal Assistance Treaty).
The only way to even begin to use Protonmail safely is to:
1) Use a VPN to prevent Proton from ever knowing your real IP address; and
2) Use a second set of PGP keys that you generate yourself — Proton won’t have the private half of those keys.